Hello,
Several users have recently asked how to route all traffic through a wireguard interface, just setting Allowed IPs to 0.0.0.0/0 + ::/0 (or similar with /1 masks) is doomed to fail because there must be an exception at least for the IP address of the wg server.
A workaround is to play with the metric of a static route to the server, it works but must be actively maintained if the IP address changes.
Here is a much cleaner solution, it is derived from the wg-quick utility.
As the UI doesn’t provide for PostUp and PreDown scripts, the method uses mwan3 in order to act on ifup and ifdown events.
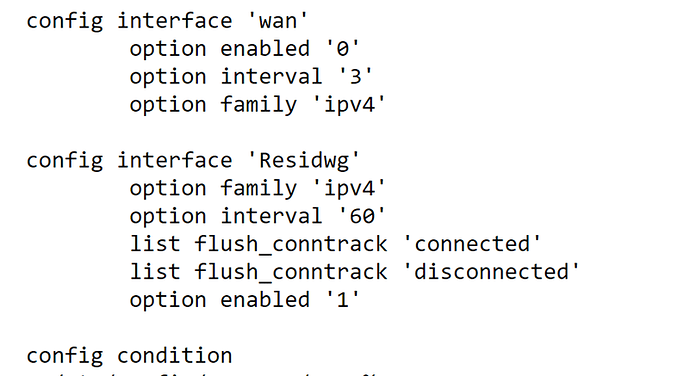
First declare the wg interface in /etc/config/mwan3, like below. Set the name and table value to suit your needs:
config interface 'wgxxx'
option family 'ipv4'
option interval '60'
list flush_conntrack 'connected'
list flush_conntrack 'disconnected'
option enabled '1'
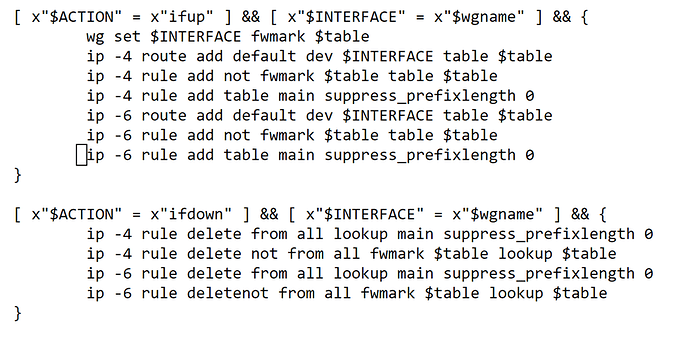
then add the following code to /etc/mwan3.user:
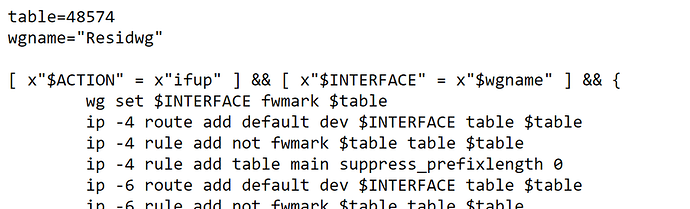
table=51820
wgname="wgxxx"
[ x"$ACTION" = x"ifup" ] && [ x"$INTERFACE" = x"$wgname" ] && {
logger -t "mwan3.user[$$]" -p notice " add rules/routes $ACTION interface $INTERFACE device $DEVICE"
wg set $INTERFACE fwmark $table
ip -4 route add default dev $INTERFACE table $table
if [ $(ip -4 rule show 2>/dev/null | grep -c "lookup $table") -eq 0 ]; then
ip -4 rule add not fwmark $table table $table
fi
if [ $(ip -4 rule show 2>/dev/null | grep -c "from all lookup main suppress_prefixlength 0") -eq 0 ]; then
ip -4 rule add table main suppress_prefixlength 0
fi
ip -6 route add default dev $INTERFACE table $table
if [ $(ip -6 rule show 2>/dev/null | grep -c "lookup $table") -eq 0 ]; then
ip -6 rule add not fwmark $table table $table
fi
if [ $(ip -6 rule show 2>/dev/null | grep -c "from all lookup main suppress_prefixlength 0") -eq 0 ]; then
ip -6 rule add table main suppress_prefixlength 0
fi
}
[ x"$ACTION" = x"ifdown" ] && [ x"$INTERFACE" = x"$wgname" ] && {
logger -t "mwan3.user[$$]" -p notice " delete rules/routes $ACTION interface $INTERFACE device $DEVICE"
while [ $(ip -4 rule show 2>/dev/null | grep -c "lookup $table") -gt 0 ]; do
ip -4 rule delete table $table
done
while [ $(ip -4 rule show 2>/dev/null | grep -c "from all lookup main suppress_prefixlength 0") -gt 0 ]; do
ip -4 rule delete table main suppress_prefixlength 0
done
while [ $(ip -6 rule show 2>/dev/null | grep -c "lookup $table") -gt 0 ]; do
ip -6 rule delete table $table
done
while [ $(ip -6 rule show 2>/dev/null | grep -c "from all lookup main suppress_prefixlength 0") -gt 0 ]; do
ip -6 rule delete table main suppress_prefixlength 0
done
}
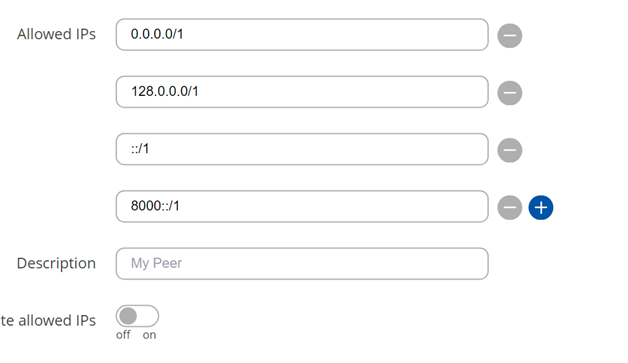
Allowed IPs must be set to
0.0.0.0/1 + 128.0.0.0/1 + ::/1 + 8000::/1
At the end, restart mwan3:
/etc/init.d/mwan3 restart
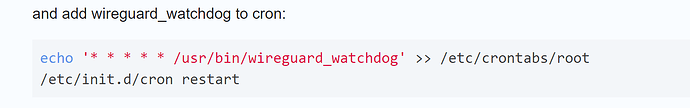
and add wireguard_watchdog to cron:
echo '* * * * * /usr/bin/wireguard_watchdog' >> /etc/crontabs/root
/etc/init.d/cron restart
Local traffic (DHCP, DHCPv6, router sollicitation and so on) is still processed normally.
@Talleyrand: could you test this ?
Regards,