So the handshake fails. May I see the output of the wg command ? Of ip -4 rule show and ip -4 route show ?
A good recipe for breaking things if you aren’t careful enough…
root@RUTX10:~# wg
interface: residwg
public key: (EDITED)
private key: (hidden)
listening port: 48574
fwmark: 0xbdbe
peer: (EDITED)
endpoint: 176.10.248.203:48574
allowed ips: 0.0.0.0/1, 128.0.0.0/1, ::/1, 8000::/1
transfer: 0 B received, 148 B sent
persistent keepalive: every 25 seconds
root@RUTX10:~# ip -4 route show
default via 192.168.1.1 dev eth1 proto static src 192.168.1.3 metric 2
10.0.138.0/24 dev residwg proto kernel scope link src 10.0.138.123
192.168.1.0/24 dev br-lan proto static scope link metric 1
192.168.1.0/24 dev eth1 proto static scope link metric 2
root@RUTX10:~# ip -4 rule show
0: from all lookup local
998: from all lookup main suppress_prefixlength 0
999: not from all fwmark 0xbdbe lookup 48574
1000: from all lookup main suppress_prefixlength 0
1001: not from all fwmark 0xbdbe lookup 48574
1002: from all iif residwg lookup 2
2002: from all fwmark 0x200/0x3f00 lookup 2
2061: from all fwmark 0x3d00/0x3f00 blackhole
2062: from all fwmark 0x3e00/0x3f00 unreachable
3002: from all fwmark 0x200/0x3f00 unreachable
32766: from all lookup main
32767: from all lookup default
Exactly. Don’t remember exactly what I did, but when fiddling even in the web UI I managed to brick the thing and had to do a physical factory reset ![]()
from all lookup main suppress_prefixlength 0
The rules appear twice in the ip -4 rule show,something has failed when the wg interface was shut down.
Look at the very first post I have hardened the code in the ifdown section copy it and restart the full network stack:
/etc/init.d/network restart
that should flush all unwanted rules.
Note: you don’t need to use the UI to start and stop the wg interface, you can execute:
ubus call network.interface.residwg up
ubus call network.interface.residwg down
from a shell for the same result.
The rules appear twice in the ip -4 rule show,something has failed when the wg interface was shut down.
Yes. I did a simple reboot and now get no double entries:
root@RUTX10:~# ip -4 rule show
0: from all lookup local
1000: from all lookup main suppress_prefixlength 0
1001: not from all fwmark 0xbdbe lookup 48574
1002: from all iif residwg lookup 2
2002: from all fwmark 0x200/0x3f00 lookup 2
2061: from all fwmark 0x3d00/0x3f00 blackhole
2062: from all fwmark 0x3e00/0x3f00 unreachable
3002: from all fwmark 0x200/0x3f00 unreachable
32766: from all lookup main
32767: from all lookup default
Note: you don’t need to use the UI to start and stop the wg interface, you can execute:
ubus call network.interface.residwg up ubus call network.interface.residwg downfrom a shell for the same result.
Thanks. Being completely unfamiliar with both command sets and syntax of the shells pushing that little button back and forth feels a lot safer… I work in the CLI of the web interface anyway. Will take a little while to make sure I get the new code down right (if there is a cut and paste way that won’t ruin it by inserting spaces or page breaks just let me know) but I’m on it.
For good measure I have also hardened the ifup section. It won’t hurt anyway.
Yes, I noticed something funny happened in the box halfway through the ifdown section.
(For any external readers engaged enough to read the exchange in full detail I can calm your nerves: Talleyrand figured out a way to copypaste so only proofreading was necessary.)
Network restarted. I now have no handshake at all rather than an empty one. But wg delivers more than nothing:
interface: residwg
public key: (EDITED)
private key: (hidden)
listening port: 48574
fwmark: 0xbdbe
peer: (EDITED)
endpoint: 176.10.248.203:48574
allowed ips: 0.0.0.0/1, 128.0.0.0/1, ::/1, 8000::/1
persistent keepalive: every 25 seconds
Logread -f gives an error message every minute:
Sat Nov 4 22:18:00 2023 cron.err crond[8672]: USER root pid 24091 cmd/usr/bin/wireguard_watchdog
Ip -4 route:
root@RUTX10:~# ip -4 route show
default via 192.168.1.1 dev eth1 proto static src 192.168.1.3 metric 2
10.0.138.0/24 dev residwg proto kernel scope link src 10.0.138.123
192.168.1.0/24 dev br-lan proto static scope link metric 1
192.168.1.0/24 dev eth1 proto static scope link metric 2
…and ip -4 rule:
root@RUTX10:~# ip -4 rule show
0: from all lookup local
1000: from all lookup main suppress_prefixlength 0
1001: not from all fwmark 0xbdbe lookup 48574
1002: from all iif residwg lookup 2
2002: from all fwmark 0x200/0x3f00 lookup 2
2061: from all fwmark 0x3d00/0x3f00 blackhole
2062: from all fwmark 0x3e00/0x3f00 unreachable
3002: from all fwmark 0x200/0x3f00 unreachable
32766: from all lookup main
32767: from all lookup default
listening port: 48574
This seems to be another issue I have mentionned in another post.
Edit /etc/config/network, delete all occurences of “option listen_port …”, and stop and restart the wg tunnel using the ubus commands above.
Another possibility is a typo in one or more keys, please check.
Logread -f gives an error message every minute:
Sat Nov 4 22:18:00 2023 cron.err crond[8672]: USER root pid 24091 cmd/usr/bin/wireguard_watchdog
For the moment you can disable the crontab entry, comment out the line in /etc/crontabs/root and restart cron.
Edit /etc/config/network, delete all occurences of “option listen_port …”, and stop and restart the wg tunnel using the ubus commands above.
Done. We’re back to an empty handshake with nothing received.
Another possibility is a typo in one or more keys, please check.
I copy pasted them at the time but have checked both for extra spaces and vs the config file. They look as they should.
That makes sense since they and the tunnel work in the vanilla, non-edited state of my router (even though the router then does not send the traffic that way)
2062: from all fwmark 0x3e00/0x3f00 unreachable
Could yo delete this one (another old hurdle, not sure if it applies here):
ip -4 rule delete from all fwmark 0x3e00/0x3f00 unreachable
endpoint: 176.10.248.203:48574
Have you hardcoded the IP address or used a name with name resolution ?
ip -4 route add default dev $INTERFACE table $table
Could you execute this command manually (substituing the right values of course) and see if there is any error ?
Which physical interface do you use for output ? wan ? mob1s?a1 ? other ?
Last try:
tcpdump -i any -n -v 'host 176.10.248.203'
in one terminal, and stop / restart the tunnel with ubus.
What is the output of tcpdump ?
Could yo delete this one (another old hurdle, not sure if it applies here):
ip -4 rule delete from all fwmark 0x3e00/0x3f00 unreachable
Done
endpoint: 176.10.248.203:48574
Have you hardcoded the IP address or used a name with name resolution ?
It used to be a domain as per the config file, but above when fiddling we exchanged that for a defined endpoint IP, so that is what we have right now. When the tunnel works (but there’s no traffic routed there) the endpoint varies and the tunnel works fine with the domain only.
ip -4 route add default dev $INTERFACE table $tableCould you execute this command manually (substituing the right values of course) and see if there is any error ?
Sure. Just to make sure I don’t get it wrong (still new although I’ve learned plenty today + I am getting tired) what we are talking about is entering the values for interface and table in the $versions above, right?
Which physical interface do you use for output ? wan ? mob1s?a1 ? other ?
My router is an X10 meaning no mobile. WAN. It sits behind another router and a media converter to optical but they do not disturb the tunnel when I establish one straight from my computer, for example.
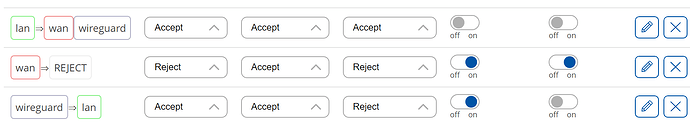
One question from me, and I realise we may well have been fiddling with this in code and that you probably see it in the routes/logs, but is this the way we want the firewall or do we want to let the wg interface send to wan?:
Last try:
tcpdump -i any -n -v 'host 176.10.248.203'in one terminal, and stop / restart the tunnel with ubus.
What is the output of tcpdump ?
Can I do this consecutively in the CLI in the web UI? Otherwise I fear I need a tip on how to open a terminal window to/from the router in parallel to that. Sorry for not knowing.
entering the values for interface and table in the $versions above, right?
Yes, $INTERFACE = residwg and $table = 48574
In the firewall page, set Wireguard=>lan to Accept/Accept/Accept.
Here is my wireguard config from /etc/config/network. Compare to yours.
config interface 'wgtls'
option proto 'wireguard'
option private_key 'edited='
option mtu '1280'
list dns '172.31.248.1'
list addresses '172.31.248.2/24'
option metric '8'
option disabled '0'
config wireguard_wgtls 'ax9000'
option endpoint_port '51820'
option preshared_key 'edited='
option public_key 'edited='
option persistent_keepalive '25'
option endpoint_host 'the-name-of-the-server'
option route_allowed_ips '1'
list allowed_ips '0.0.0.0/1'
list allowed_ips '128.0.0.0/1'
list allowed_ips '::/1'
list allowed_ips '8000::/1'
If you can spot something interesting …
I’m also getting tired. Restart tomorrow.
Install putty or openssh on you winx machine, generate ssh key of type ed25519 and import the public key in System->Administration->Access Control. Enable both ssh access and key based authentication and insert your public key in ‘public keys’.
Which metric have you set on the wg interface ? None ?
If so increase it to 4.