Solve this one first. tcpdump on the RUT and on the PC.
What are the outputs ?
Solve this one first. tcpdump on the RUT and on the PC.
What are the outputs ?
Server Ping to RUT LAN PC:
RUT tcpdump:
root@RUT241:~# tcpdump -i any -n -v icmp
tcpdump: WARNING: any: That device doesn't support promiscuous mode
(Promiscuous mode not supported on the "any" device)
tcpdump: listening on any, link-type LINUX_SLL2 (Linux cooked v2), snapshot length 262144 bytes
16:44:59.395432 WG_AIO In IP (tos 0x0, ttl 64, id 48171, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 1, length 64
16:44:59.395690 br-lan Out IP (tos 0x0, ttl 63, id 48171, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 1, length 64
16:44:59.395726 eth0.1 Out IP (tos 0x0, ttl 63, id 48171, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 1, length 64
16:45:00.554449 WG_AIO In IP (tos 0x0, ttl 64, id 48807, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 2, length 64
16:45:00.554623 br-lan Out IP (tos 0x0, ttl 63, id 48807, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 2, length 64
16:45:00.554657 eth0.1 Out IP (tos 0x0, ttl 63, id 48807, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 2, length 64
16:45:01.477687 WG_AIO In IP (tos 0x0, ttl 64, id 49425, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 3, length 64
16:45:01.477860 br-lan Out IP (tos 0x0, ttl 63, id 49425, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 3, length 64
16:45:01.477894 eth0.1 Out IP (tos 0x0, ttl 63, id 49425, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 3, length 64
16:45:02.679367 WG_AIO In IP (tos 0x0, ttl 64, id 50399, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 4, length 64
16:45:02.679540 br-lan Out IP (tos 0x0, ttl 63, id 50399, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 4, length 64
16:45:02.679576 eth0.1 Out IP (tos 0x0, ttl 63, id 50399, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 4, length 64
16:45:03.756320 WG_AIO In IP (tos 0x0, ttl 64, id 51239, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 5, length 64
16:45:03.756494 br-lan Out IP (tos 0x0, ttl 63, id 51239, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 5, length 64
16:45:03.756528 eth0.1 Out IP (tos 0x0, ttl 63, id 51239, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 5, length 64
16:45:04.714351 WG_AIO In IP (tos 0x0, ttl 64, id 51270, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 6, length 64
16:45:04.714521 br-lan Out IP (tos 0x0, ttl 63, id 51270, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 6, length 64
16:45:04.714558 eth0.1 Out IP (tos 0x0, ttl 63, id 51270, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 6, length 64
16:45:05.674435 WG_AIO In IP (tos 0x0, ttl 64, id 51634, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 7, length 64
16:45:05.674602 br-lan Out IP (tos 0x0, ttl 63, id 51634, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 7, length 64
16:45:05.674637 eth0.1 Out IP (tos 0x0, ttl 63, id 51634, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 7, length 64
16:45:06.633299 WG_AIO In IP (tos 0x0, ttl 64, id 51949, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 8, length 64
16:45:06.633464 br-lan Out IP (tos 0x0, ttl 63, id 51949, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 8, length 64
16:45:06.633501 eth0.1 Out IP (tos 0x0, ttl 63, id 51949, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 8, length 64
16:45:07.650804 WG_AIO In IP (tos 0x0, ttl 64, id 52686, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 9, length 64
16:45:07.650972 br-lan Out IP (tos 0x0, ttl 63, id 52686, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 9, length 64
16:45:07.651008 eth0.1 Out IP (tos 0x0, ttl 63, id 52686, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 9, length 64
16:45:08.875429 WG_AIO In IP (tos 0x0, ttl 64, id 53683, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 10, length 64
16:45:08.875596 br-lan Out IP (tos 0x0, ttl 63, id 53683, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 10, length 64
16:45:08.875633 eth0.1 Out IP (tos 0x0, ttl 63, id 53683, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 10, length 64
16:45:09.681599 WG_AIO In IP (tos 0x0, ttl 64, id 53756, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 11, length 64
16:45:09.681766 br-lan Out IP (tos 0x0, ttl 63, id 53756, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 11, length 64
16:45:09.681802 eth0.1 Out IP (tos 0x0, ttl 63, id 53756, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 11, length 64
16:45:10.794581 WG_AIO In IP (tos 0x0, ttl 64, id 53801, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 12, length 64
16:45:10.794751 br-lan Out IP (tos 0x0, ttl 63, id 53801, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 12, length 64
16:45:10.794787 eth0.1 Out IP (tos 0x0, ttl 63, id 53801, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 12, length 64
16:45:11.754377 WG_AIO In IP (tos 0x0, ttl 64, id 54613, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 13, length 64
16:45:11.754558 br-lan Out IP (tos 0x0, ttl 63, id 54613, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 13, length 64
16:45:11.754594 eth0.1 Out IP (tos 0x0, ttl 63, id 54613, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 13, length 64
16:45:12.746719 WG_AIO In IP (tos 0x0, ttl 64, id 54871, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 14, length 64
16:45:12.746906 br-lan Out IP (tos 0x0, ttl 63, id 54871, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 14, length 64
16:45:12.746942 eth0.1 Out IP (tos 0x0, ttl 63, id 54871, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 14, length 64
16:45:13.771627 WG_AIO In IP (tos 0x0, ttl 64, id 55709, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 15, length 64
16:45:13.771799 br-lan Out IP (tos 0x0, ttl 63, id 55709, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 15, length 64
16:45:13.771836 eth0.1 Out IP (tos 0x0, ttl 63, id 55709, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 15, length 64
16:45:14.954323 WG_AIO In IP (tos 0x0, ttl 64, id 56351, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 16, length 64
16:45:14.954491 br-lan Out IP (tos 0x0, ttl 63, id 56351, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 16, length 64
16:45:14.954526 eth0.1 Out IP (tos 0x0, ttl 63, id 56351, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 16, length 64
16:45:15.812405 WG_AIO In IP (tos 0x0, ttl 64, id 56695, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 17, length 64
16:45:15.812576 br-lan Out IP (tos 0x0, ttl 63, id 56695, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 17, length 64
16:45:15.812613 eth0.1 Out IP (tos 0x0, ttl 63, id 56695, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.116: ICMP echo request, id 16426, seq 17, length 64
RUT LAN PC:
C:\Users\User>"C:\Users\User\Downloads\WinDump.exe" icmp
C:\Users\User\Downloads\WinDump.exe: listening on \Device\NPF_{DF764C8F-1301-4EFF-8920-AD58D6E50EE2}
16:44:59.707128 IP my-vpn-endpoint-host.colocrossing.com > DESKTOP-CR57F34.lan: ICMP echo request, id 16426, seq 1, length 64
16:45:00.865869 IP my-vpn-endpoint-host.colocrossing.com > DESKTOP-CR57F34.lan: ICMP echo request, id 16426, seq 2, length 64
16:45:01.789093 IP my-vpn-endpoint-host.colocrossing.com > DESKTOP-CR57F34.lan: ICMP echo request, id 16426, seq 3, length 64
16:45:02.990566 IP my-vpn-endpoint-host.colocrossing.com > DESKTOP-CR57F34.lan: ICMP echo request, id 16426, seq 4, length 64
16:45:04.067201 IP my-vpn-endpoint-host.colocrossing.com > DESKTOP-CR57F34.lan: ICMP echo request, id 16426, seq 5, length 64
16:45:05.025761 IP my-vpn-endpoint-host.colocrossing.com > DESKTOP-CR57F34.lan: ICMP echo request, id 16426, seq 6, length 64
16:45:05.985905 IP my-vpn-endpoint-host.colocrossing.com > DESKTOP-CR57F34.lan: ICMP echo request, id 16426, seq 7, length 64
16:45:06.944015 IP my-vpn-endpoint-host.colocrossing.com > DESKTOP-CR57F34.lan: ICMP echo request, id 16426, seq 8, length 64
16:45:07.962256 IP my-vpn-endpoint-host.colocrossing.com > DESKTOP-CR57F34.lan: ICMP echo request, id 16426, seq 9, length 64
16:45:09.186544 IP my-vpn-endpoint-host.colocrossing.com > DESKTOP-CR57F34.lan: ICMP echo request, id 16426, seq 10, length 64
16:45:09.992946 IP my-vpn-endpoint-host.colocrossing.com > DESKTOP-CR57F34.lan: ICMP echo request, id 16426, seq 11, length 64
16:45:11.106035 IP my-vpn-endpoint-host.colocrossing.com > DESKTOP-CR57F34.lan: ICMP echo request, id 16426, seq 12, length 64
16:45:12.065868 IP my-vpn-endpoint-host.colocrossing.com > DESKTOP-CR57F34.lan: ICMP echo request, id 16426, seq 13, length 64
16:45:13.057654 IP my-vpn-endpoint-host.colocrossing.com > DESKTOP-CR57F34.lan: ICMP echo request, id 16426, seq 14, length 64
16:45:14.082756 IP my-vpn-endpoint-host.colocrossing.com > DESKTOP-CR57F34.lan: ICMP echo request, id 16426, seq 15, length 64
16:45:15.265812 IP my-vpn-endpoint-host.colocrossing.com > DESKTOP-CR57F34.lan: ICMP echo request, id 16426, seq 16, length 64
16:45:16.123606 IP my-vpn-endpoint-host.colocrossing.com > DESKTOP-CR57F34.lan: ICMP echo request, id 16426, seq 17, length 64
So the “RUT LAN PC” doesn’t reply to ICMP echo requests. Why ? A firewall ?
Sorry for the delay as a first time user I have reached the max number of replies I had to create a new account in order to answer. Of course only the french-speaking users will be able to understand.
I am assuming it’s a configuration issue within the RUT, since the point of failure appears to be in the routing between the wireguard connection and LAN.
The RUT is configured factory with the exception of the settings in my first post. The RUT configuration guides I’ve seen all indicate this should work and I am uncertain how to proceed.
No. The “RUT LAN PC” physical interface “sees” the ICMP packets but this is not proof that the core OS receives them and can reply.
I’m open to additional troubleshooting ideas to isolate the point of failure - I’m at a loss for how to proceed with narrowing it down.
This is becoming very annoying. Do you have a spare Linux PC / Raspberry / Beaglebone or the like somewhere ?
What is the default route of this “RUT LAN PC” ?
Hi Mike,
I’ve followed every guide I can find on the forum and in the documentation (1, 2) and it appears the wireguard connection is working (I can successfully connect to the the RUT WebUI / SSH using the wireguard address while my PC Client is connected to wireguard), but am unable to ping the RUT’s LAN address (192.168.1.1) or anything on the RUT’s LAN. From everything I can tell browsing the forums for alternative solutions, you’d be the guy to know. Any ideas?
I suspect its a routing / firewall configuration issue on the RUT, and am happy to share my config / try any number of things. By all accounts, the guides in the docs make it seem like the configuration I have should work.
After making some changes to the RUT firewall config, tcpdump appears to indicate ping generating a request and a reply.
Ping from PC Client (10.7.0.2) to RUT Lan:
RUT tcpdump 192.168.1.1:
root@RUT241:~# tcpdump -i any -n -v icmp
tcpdump: WARNING: any: That device doesn't support promiscuous mode
(Promiscuous mode not supported on the "any" device)
tcpdump: listening on any, link-type LINUX_SLL2 (Linux cooked v2), snapshot length 262144 bytes
12:08:51.961261 lo In IP (tos 0xc0, ttl 64, id 63998, offset 0, flags [none], proto ICMP (1), length 116)
127.0.0.1 > 127.0.0.1: ICMP 127.0.0.1 udp port 41325 unreachable, length 96
IP (tos 0x0, ttl 64, id 16241, offset 0, flags [DF], proto UDP (17), length 88)
127.0.0.1.53 > 127.0.0.1.41325: 37146 1/0/0 rms.teltonika-networks.com. A 18.196.62.30 (60)
12:08:51.980578 WG1 Out IP (tos 0xc8, ttl 64, id 24118, offset 0, flags [none], proto ICMP (1), length 116)
10.7.0.3 > 9.9.9.9: ICMP 10.7.0.3 udp port 46391 unreachable, length 96
IP (tos 0x48, ttl 55, id 24815, offset 0, flags [none], proto UDP (17), length 88)
9.9.9.9.53 > 10.7.0.3.46391: 4852 1/0/0 rms.teltonika-networks.com. A 18.196.62.30 (60)
12:08:53.888233 WG1 In IP (tos 0x0, ttl 127, id 44224, offset 0, flags [none], proto ICMP (1), length 60)
my.vpn.endpoint > 192.168.1.1: ICMP echo request, id 1, seq 100, length 40
12:08:53.888443 qmimux0 Out IP (tos 0x0, ttl 64, id 8403, offset 0, flags [none], proto ICMP (1), length 60)
192.168.1.1 > my.vpn.endpoint: ICMP echo reply, id 1, seq 100, length 40
12:08:58.523989 WG1 In IP (tos 0x0, ttl 127, id 44225, offset 0, flags [none], proto ICMP (1), length 60)
my.vpn.endpoint > 192.168.1.1: ICMP echo request, id 1, seq 101, length 40
12:08:58.524200 qmimux0 Out IP (tos 0x0, ttl 64, id 8818, offset 0, flags [none], proto ICMP (1), length 60)
192.168.1.1 > my.vpn.endpoint: ICMP echo reply, id 1, seq 101, length 40
12:09:03.598461 WG1 In IP (tos 0x0, ttl 127, id 44226, offset 0, flags [none], proto ICMP (1), length 60)
my.vpn.endpoint > 192.168.1.1: ICMP echo request, id 1, seq 102, length 40
12:09:03.598669 qmimux0 Out IP (tos 0x0, ttl 64, id 8943, offset 0, flags [none], proto ICMP (1), length 60)
192.168.1.1 > my.vpn.endpoint: ICMP echo reply, id 1, seq 102, length 40
12:09:08.761108 WG1 In IP (tos 0x0, ttl 127, id 44227, offset 0, flags [none], proto ICMP (1), length 60)
my.vpn.endpoint > 192.168.1.1: ICMP echo request, id 1, seq 103, length 40
12:09:08.761318 qmimux0 Out IP (tos 0x0, ttl 64, id 9169, offset 0, flags [none], proto ICMP (1), length 60)
192.168.1.1 > my.vpn.endpoint: ICMP echo reply, id 1, seq 103, length 40
^C
10 packets captured
23 packets received by filter
0 packets dropped by kernel
RUT tcpdump 192.168.1.101:
root@RUT241:~# tcpdump -i any -n -v icmp
tcpdump: WARNING: any: That device doesn't support promiscuous mode
(Promiscuous mode not supported on the "any" device)
tcpdump: listening on any, link-type LINUX_SLL2 (Linux cooked v2), snapshot length 262144 bytes
12:09:50.361341 WG1 In IP (tos 0x0, ttl 127, id 54115, offset 0, flags [none], proto ICMP (1), length 60)
my.vpn.endpoint > 192.168.1.101: ICMP echo request, id 1, seq 104, length 40
12:09:50.361605 br-lan Out IP (tos 0x0, ttl 126, id 54115, offset 0, flags [none], proto ICMP (1), length 60)
192.168.1.1 > 192.168.1.101: ICMP echo request, id 1, seq 104, length 40
12:09:50.361636 eth0.1 Out IP (tos 0x0, ttl 126, id 54115, offset 0, flags [none], proto ICMP (1), length 60)
192.168.1.1 > 192.168.1.101: ICMP echo request, id 1, seq 104, length 40
12:09:50.361925 eth0 In IP (tos 0x0, ttl 64, id 52383, offset 0, flags [none], proto ICMP (1), length 60)
192.168.1.101 > 192.168.1.1: ICMP echo reply, id 1, seq 104, length 40
12:09:50.361934 eth0.1 In IP (tos 0x0, ttl 64, id 52383, offset 0, flags [none], proto ICMP (1), length 60)
192.168.1.101 > 192.168.1.1: ICMP echo reply, id 1, seq 104, length 40
12:09:50.361955 br-lan In IP (tos 0x0, ttl 64, id 52383, offset 0, flags [none], proto ICMP (1), length 60)
192.168.1.101 > 192.168.1.1: ICMP echo reply, id 1, seq 104, length 40
12:09:50.362094 qmimux0 Out IP (tos 0x0, ttl 63, id 52383, offset 0, flags [none], proto ICMP (1), length 60)
192.168.1.101 > my.vpn.endpoint: ICMP echo reply, id 1, seq 104, length 40
12:09:55.016963 WG1 In IP (tos 0x0, ttl 127, id 54116, offset 0, flags [none], proto ICMP (1), length 60)
my.vpn.endpoint > 192.168.1.101: ICMP echo request, id 1, seq 105, length 40
12:09:55.017113 br-lan Out IP (tos 0x0, ttl 126, id 54116, offset 0, flags [none], proto ICMP (1), length 60)
192.168.1.1 > 192.168.1.101: ICMP echo request, id 1, seq 105, length 40
12:09:55.017144 eth0.1 Out IP (tos 0x0, ttl 126, id 54116, offset 0, flags [none], proto ICMP (1), length 60)
192.168.1.1 > 192.168.1.101: ICMP echo request, id 1, seq 105, length 40
12:09:55.017358 eth0 In IP (tos 0x0, ttl 64, id 52639, offset 0, flags [none], proto ICMP (1), length 60)
192.168.1.101 > 192.168.1.1: ICMP echo reply, id 1, seq 105, length 40
12:09:55.017366 eth0.1 In IP (tos 0x0, ttl 64, id 52639, offset 0, flags [none], proto ICMP (1), length 60)
192.168.1.101 > 192.168.1.1: ICMP echo reply, id 1, seq 105, length 40
12:09:55.017386 br-lan In IP (tos 0x0, ttl 64, id 52639, offset 0, flags [none], proto ICMP (1), length 60)
192.168.1.101 > 192.168.1.1: ICMP echo reply, id 1, seq 105, length 40
12:09:55.017501 qmimux0 Out IP (tos 0x0, ttl 63, id 52639, offset 0, flags [none], proto ICMP (1), length 60)
192.168.1.101 > my.vpn.endpoint: ICMP echo reply, id 1, seq 105, length 40
client_loop: send disconnect: Connection reset
Which ones ?
What is the numeric value of my.vpn.endpoint and other litteral addresses ? The traces are hard to follow.
Which ones ?
I turned on masquerading on the lan. That’s all.
The numeric value of my.vpn.endpoint is the public IP address of the Wireguard server (not 10.7.0.1).
So the ping is originating at the wireguard server public IP → RUT LAN IP (192.168.1.1) and back to the wireguard server public IP. The server SSH session is just never seeing the reply.
As in lan => wan + wireguard ? Can you confirm ?
In the echo requests from my.vpn.endpoint to 192.168.1.101 the source address appears to have a curious value. Why is another question.
Disable masquerading for bothe lan=>wan+wireguard and wireguard=>lan, and retry the ping. What is the tcpdump output ?
It may be worth noting, the connection to this device is via cell modem. Not sure that it makes a difference.
root@RUT241:~# tcpdump -i any -n -v icmp
tcpdump: WARNING: any: That device doesn't support promiscuous mode
(Promiscuous mode not supported on the "any" device)
tcpdump: listening on any, link-type LINUX_SLL2 (Linux cooked v2), snapshot length 262144 bytes
15:44:02.070605 WG1 In IP (tos 0x0, ttl 64, id 14742, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.1: ICMP echo request, id 8862, seq 1, length 64
15:44:02.070931 qmimux0 Out IP (tos 0x0, ttl 64, id 9580, offset 0, flags [none], proto ICMP (1), length 84)
192.168.1.1 > my.vpn.endpoint: ICMP echo reply, id 8862, seq 1, length 64
15:44:03.168150 WG1 In IP (tos 0x0, ttl 64, id 15722, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.1: ICMP echo request, id 8862, seq 2, length 64
15:44:03.168385 qmimux0 Out IP (tos 0x0, ttl 64, id 9604, offset 0, flags [none], proto ICMP (1), length 84)
192.168.1.1 > my.vpn.endpoint: ICMP echo reply, id 8862, seq 2, length 64
15:44:04.120745 WG1 In IP (tos 0x0, ttl 64, id 16464, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.1: ICMP echo request, id 8862, seq 3, length 64
15:44:04.120983 qmimux0 Out IP (tos 0x0, ttl 64, id 9649, offset 0, flags [none], proto ICMP (1), length 84)
192.168.1.1 > my.vpn.endpoint: ICMP echo reply, id 8862, seq 3, length 64
15:44:04.972742 WG1 In IP (tos 0x0, ttl 64, id 16508, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.1: ICMP echo request, id 8862, seq 4, length 64
15:44:04.972980 qmimux0 Out IP (tos 0x0, ttl 64, id 9653, offset 0, flags [none], proto ICMP (1), length 84)
192.168.1.1 > my.vpn.endpoint: ICMP echo reply, id 8862, seq 4, length 64
15:44:06.002549 WG1 In IP (tos 0x0, ttl 64, id 16611, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.1: ICMP echo request, id 8862, seq 5, length 64
15:44:06.002782 qmimux0 Out IP (tos 0x0, ttl 64, id 9734, offset 0, flags [none], proto ICMP (1), length 84)
192.168.1.1 > my.vpn.endpoint: ICMP echo reply, id 8862, seq 5, length 64
15:44:07.016059 WG1 In IP (tos 0x0, ttl 64, id 16733, offset 0, flags [DF], proto ICMP (1), length 84)
my.vpn.endpoint > 192.168.1.1: ICMP echo request, id 8862, seq 6, length 64
15:44:07.016302 qmimux0 Out IP (tos 0x0, ttl 64, id 9756, offset 0, flags [none], proto ICMP (1), length 84)
192.168.1.1 > my.vpn.endpoint: ICMP echo reply, id 8862, seq 6, length 64
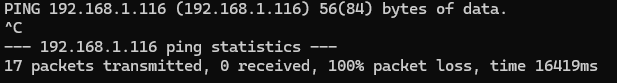
What is the result of this ping ?
Apologies - I thought I included the screenshot. All timed out. Still not working.
I see your listen port for one of tunnels is set to the https port 443. I mention this, because in my very limited experience, it’s not something I’ve seen before - is it worth seeing what happens if you set to a different unused port?
Use of port 443 for wireguard is uncommon but doesn’t seem to be the cause it works for me on a RUTX11.