I need to replace an old router
The config file on the old router is:
client
dev tun
proto udp
remote vpn-2024.xxxxx.de 62457
resolv-retry infinite
nobind
persist-key
persist-tun
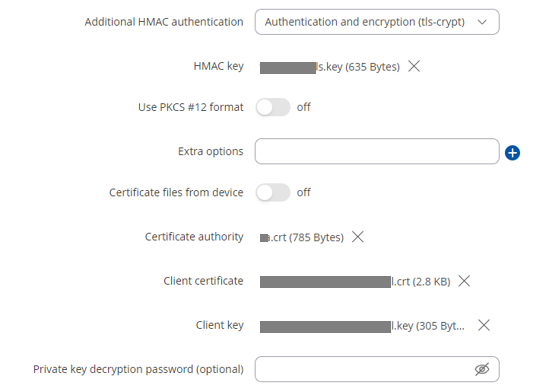
ca ca.crt
cert KFZ.crt
key KFZ.key
remote-cert-tls server
verb 3
cipher AES-256-GCM
auth SHA512
tls-ciphersuites TLS_AES_256_GCM_SHA384
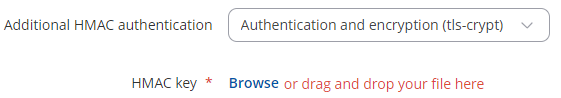
tls-crypt vpn-2024-tls.key
auth-retry nointeract
I’ve tried two ways but neither works
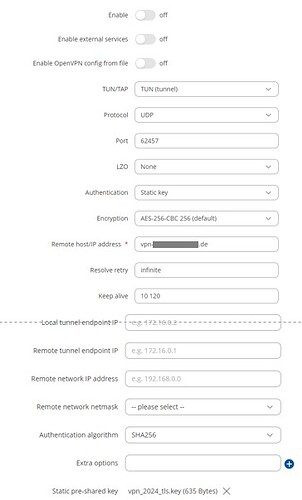
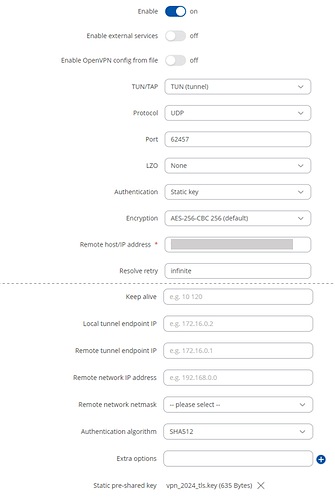
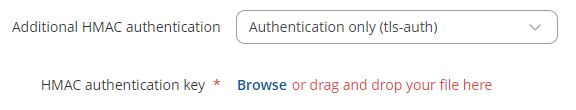
1: authentication static key
Status: Disconnected
RX: 0 B
TX: 560 B
LOG:
Tue Apr 16 20:33:22 2024 daemon.warn openvpn(KFZ)[18348]: Cipher negotiation is disabled since neither P2MP client nor server mode is enabled
Tue Apr 16 20:33:22 2024 daemon.notice openvpn(KFZ)[18348]: OpenVPN 2.5.3 mips-openwrt-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD]
Tue Apr 16 20:33:22 2024 daemon.notice openvpn(KFZ)[18348]: library versions: OpenSSL 3.0.12 24 Oct 2023, LZO 2.10
Tue Apr 16 20:33:22 2024 daemon.warn openvpn(KFZ)[18348]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Tue Apr 16 20:33:22 2024 daemon.notice openvpn(KFZ)[18348]: Outgoing Static Key Encryption: Cipher 'AES-256-CBC' initialized with 256 bit key
Tue Apr 16 20:33:22 2024 daemon.notice openvpn(KFZ)[18348]: Outgoing Static Key Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication
Tue Apr 16 20:33:22 2024 daemon.notice openvpn(KFZ)[18348]: Incoming Static Key Encryption: Cipher 'AES-256-CBC' initialized with 256 bit key
Tue Apr 16 20:33:22 2024 daemon.notice openvpn(KFZ)[18348]: Incoming Static Key Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication
Tue Apr 16 20:33:24 2024 daemon.notice openvpn(KFZ)[18348]: TUN/TAP device tun_c_KFZ opened
Tue Apr 16 20:33:24 2024 daemon.notice openvpn(KFZ)[18348]: do_ifconfig, ipv4=0, ipv6=0
Tue Apr 16 20:33:24 2024 daemon.notice openvpn(KFZ)[18348]: /etc/openvpn/updown.sh tun_c_KFZ 1500 1572 init
Tue Apr 16 20:33:24 2024 daemon.notice openvpn(KFZ)[18348]: Data Channel MTU parms [ L:1572 D:1450 EF:72 EB:398 ET:0 EL:3 ]
Tue Apr 16 20:33:24 2024 daemon.notice openvpn(KFZ)[18348]: Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1572,tun-mtu 1500,proto UDPv4,cipher AES-256-CBC,auth SHA256,keysize 256,secret'
Tue Apr 16 20:33:24 2024 daemon.notice openvpn(KFZ)[18348]: Expected Remote Options String (VER=V4): 'V4,dev-type tun,link-mtu 1572,tun-mtu 1500,proto UDPv4,cipher AES-256-CBC,auth SHA256,keysize 256,secret'
Tue Apr 16 20:33:24 2024 daemon.notice openvpn(KFZ)[18348]: TCP/UDP: Preserving recently used remote address: [AF_INET]172.65.195.23:62457
Tue Apr 16 20:33:24 2024 daemon.notice openvpn(KFZ)[18348]: Socket Buffers: R=[180224->180224] S=[180224->180224]
Tue Apr 16 20:33:24 2024 daemon.notice openvpn(KFZ)[18348]: UDP link local: (not bound)
Tue Apr 16 20:33:24 2024 daemon.notice openvpn(KFZ)[18348]: UDP link remote: [AF_INET]172.65.195.23:62457
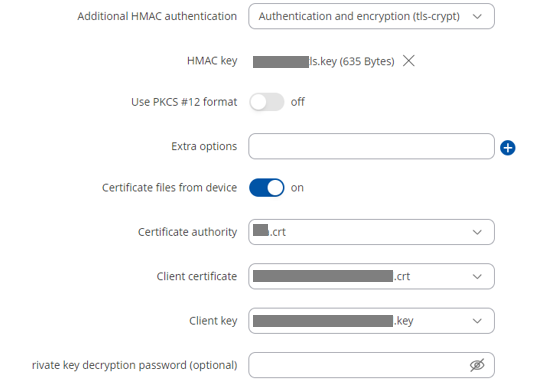
2: authentication TLS
Error
Tue Apr 16 20:36:34 2024 daemon.err openvpn(KFZ)[19586]: Options error: If you use one of --cert or --key, you must use them both
Tue Apr 16 20:36:34 2024 daemon.warn openvpn(KFZ)[19586]: Use --help for more information.
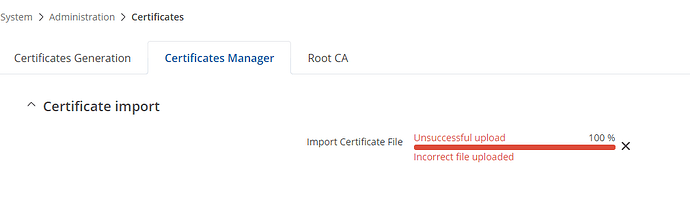
3: add vpn configuration file & static key
Error
Tue Apr 16 20:37:39 2024 daemon.warn openvpn(KFZ)[19912]: Multiple --down scripts defined. The previously configured script is overridden.
Tue Apr 16 20:37:39 2024 daemon.warn openvpn(KFZ)[19912]: Multiple --up scripts defined. The previously configured script is overridden.
Tue Apr 16 20:37:39 2024 daemon.err openvpn(KFZ)[19912]: Cannot pre-load keyfile (vpn-2024-tls.key)
Tue Apr 16 20:37:39 2024 daemon.notice openvpn(KFZ)[19912]: Exiting due to fatal error
what is the problem ?