I have a RUTXR1 set up in a site2site configuration with an OpenWRT router as peer.
Lets call the RUTXR1 site A (192.168.1.0/24), and the OpenWRT site B (192.168.2.0/24).
I have this requirement that all clients on site B have their internet access routed through the wireguard tunnel, and use site A as their exit point. The only internet traffic leaving site B, should be the Wireguard tunnel packets to (and from) site A.
I seem to have set up site B correctly, and I can reach any client on site A (using their IP) from B, but I just can’t get them to reach anything on the internet.
I have added the WAN zone in the forwarding from Wireguard the same as in this post: https://community.teltonika-networks.com/46208/wireguard-and-no-connection-to-internet-firewall-rutx09
Apparently there must be something else that I’m missing here. What setting/s could block clients in B from using A as their gateway? I only have a rudimantary network knowledge/understanding, so I would appreciate a gentle answer. I have no problems following detailed guidance though. ![]()
Hello,
Thank you for reaching out!
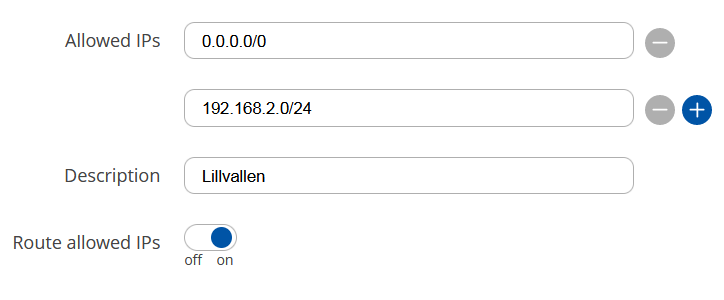
Could you post the peer config of both sides? On the RUTXR1, the OpenWRT router should be allowed to use 0.0.0.0/0 IP addresses, and the same needs to be configured on the OpenWRT side. Make sure to enable the Route allowed IPs option on OpenWRT.
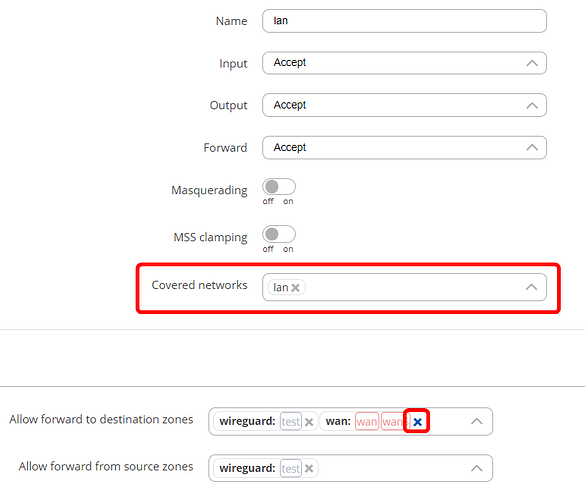
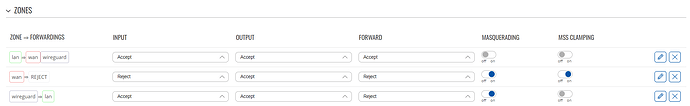
Additionally, on the OpenWRT side, the LAN clients should only be able to forward the traffic to WireGuard tunnel, and not the WAN zone:
On the RUTXR1 side, Wireguard to LAN forwarding should be enabled (as you mentioned was already done).
Best regards,
HI Daumantas!
Thank you for the fast response. Teltonika’s support is really outstanding!
To add some more context to this issue:
I used to have a working configuration with site A and B as described in my opening post, but with a different router at site A. That router lacked Wireguard capability, which is one of the reasons I switched to Teltonika instead (WWAN failover is the other main reason). So in my previous configuration I had a RPi4 setup with OpenWRT as a client in the A site, and then a port forward from the A router to that RPi for the Wireguard traffic, which then exited site A as any other A client traffic would.
I think I have copied all relevant parameters from the old RPi to the RUTXR1, but obviously I have missed something.
Since the B site is still the same config as before, I don’t think there are issues there, but I’ll add the requested info.
Screenshots coming up in next post.
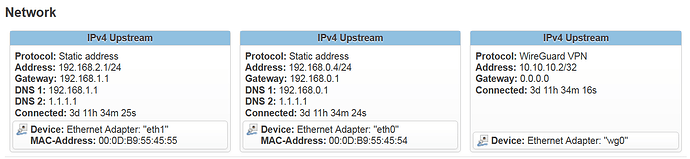
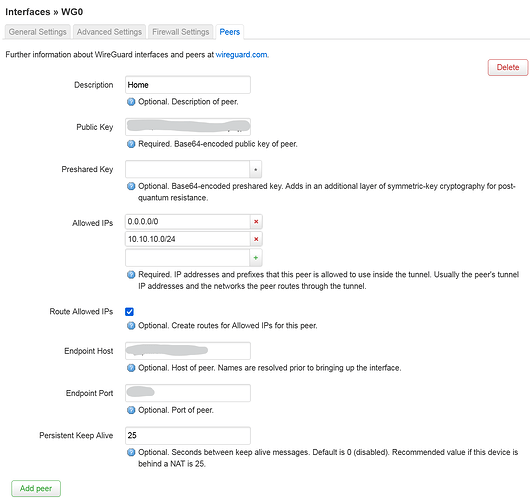
This is the overview from site B. As you can see, the B router sits behind yet another router and has a port forward from that upstream router to deliver the Wireguard traffic. This means double-NAT, and I guess it could have an effect on MTU size etc. However, there are no issues communicating back and forth between clients in the A and B networks, so I still fail to narrow down the root cause of this…
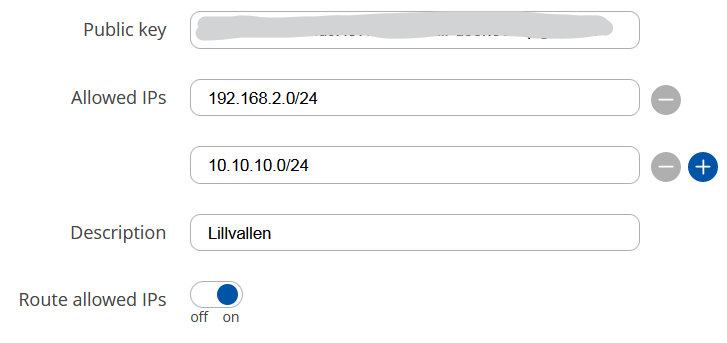
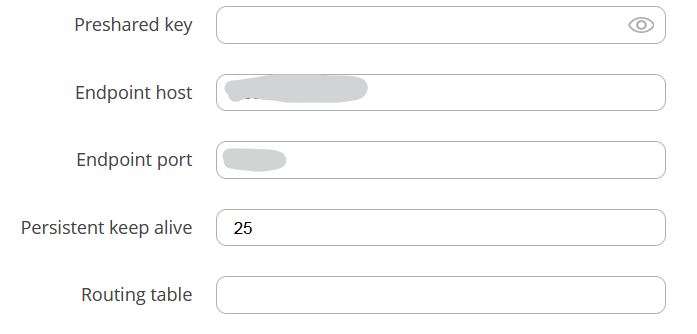
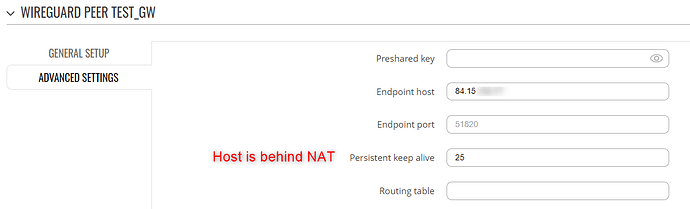
Site B peer A details.
Here you see the Route Allowed IPs is checked, and all IPs (0.0.0.0/0) are part of the allowed range (which I guess makes 10.10.10.0/24 a bit superfluous, right?
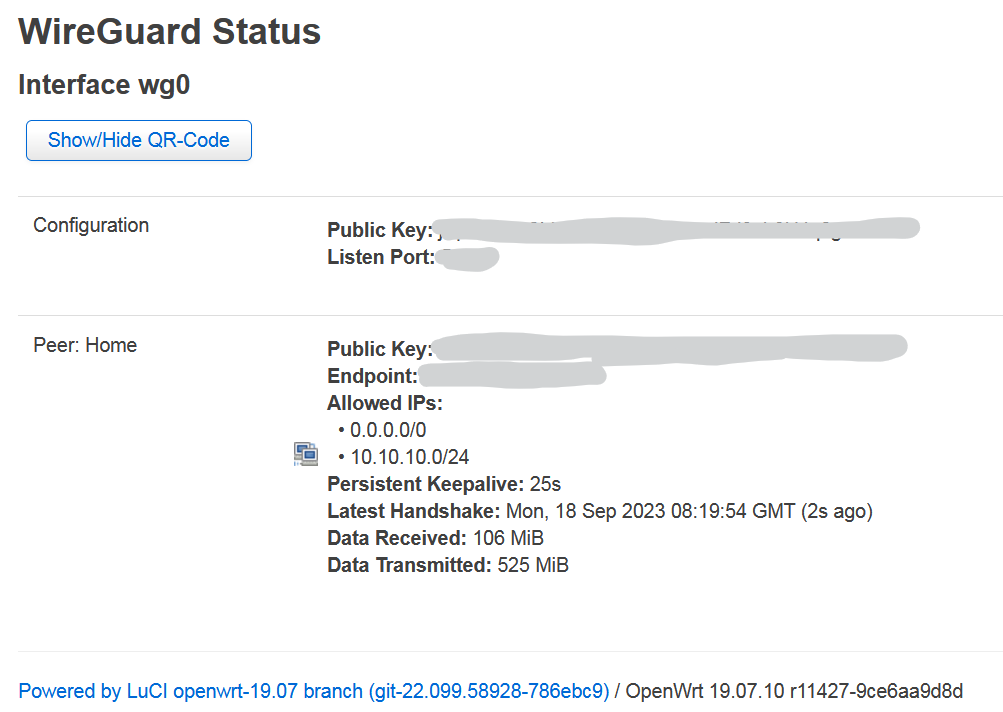
Site A (RUTXR1) Wireguard details
Heavily masked, I admit, but the tunnel works, so I hope it’s an ok level of detail I provide to solve the issue. Please advice I you need more specifics.
Hello,
Thank you for providing the information!
A few things I noticed:
-
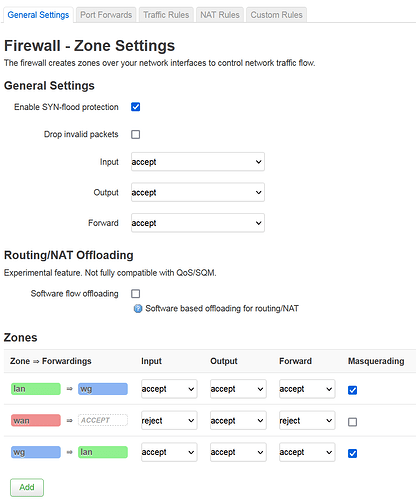
On the OpenWRT router, in the Firewall settings, I’ve noticed that
Masqueradingis disabled on the WAN zone, but enabled on the LAN zone. Could you explain a reason behind this? Perhaps you are utilizing a private network between these devices? If that’s not the case, a topology would be helpful. -
Could you try adding
0.0.0.0/0on the Teltonika side, in theAllowed IPssection? Make sure to disable theRoute allowed IPsoption first, as you will most likely lose access to the RUTXR1 otherwise. -
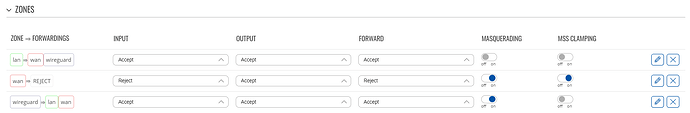
Please also attach a screenshot of the Firewall settings on RUTXR1, as this is the place where forwarding needs to be enabled on Wireguard zone, as well as Wireguard zone added to the WAN zones’
Allow forward from source zonesfield.
Best regards,
Thank you for the observations. let me address them one by one:
- This configuration wasn’t done by myself. A friend did it for me a couple of years ago. So, tbh, I don’t even understand the concept of masquerading
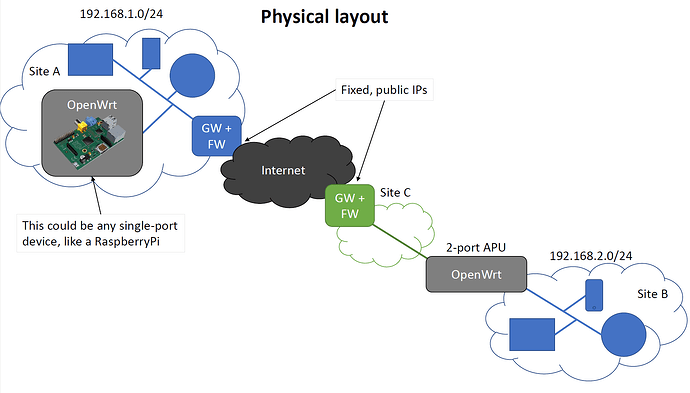
 But yes, there is a private network in-between site B and the Internet. I wrote it in the second post, but it wasn’t that obvious. I’m a guy with a graphical mind, so pictures speak better to me than written text. Here is a picture of how it worked previously, before my switch over to the RUTXR1 for site A
But yes, there is a private network in-between site B and the Internet. I wrote it in the second post, but it wasn’t that obvious. I’m a guy with a graphical mind, so pictures speak better to me than written text. Here is a picture of how it worked previously, before my switch over to the RUTXR1 for site A
- I tried to first disable the
Route allowed IPsand then added0.0.0.0/0to the list of allowed IPs from peer B (in the RUTXR1 config). The only consequence I noticed with this change, was that I lost contact with site B.
This is another thing that I should have mentioned; I’m currently at site A, whilst site B is some 650km away from me, and I have no other remote access to it besides the Wireguard tunnel. But Í have a way of probing for internet access from a client that sits in the B network, which I can access (over the Wireguard tunnel, of course )
)
Connection with site B was re-established as soon as I removed the changes made.
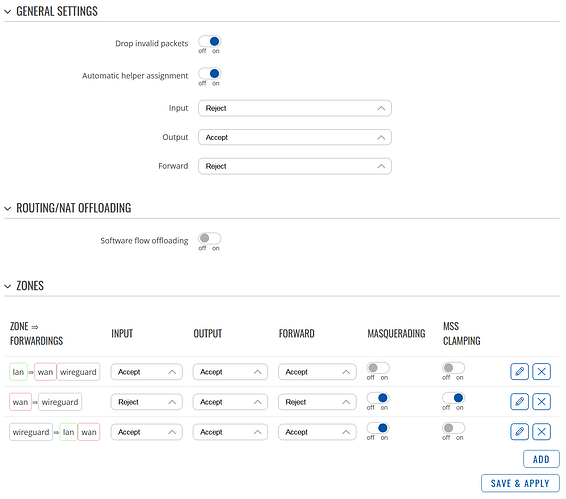
- This is my current firewall config for the RUTXR1 / site A. I have tried to copy the settings from the old RPi router/client to the best of my understanding.

I wouldn’t be surprised if this is the culprit…
Hello,
I’ve tried configuring your setup locally, and got it to work using the following settings:
-
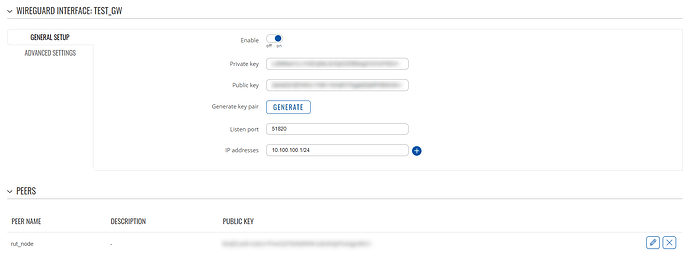
RUTX50 (the gateway):
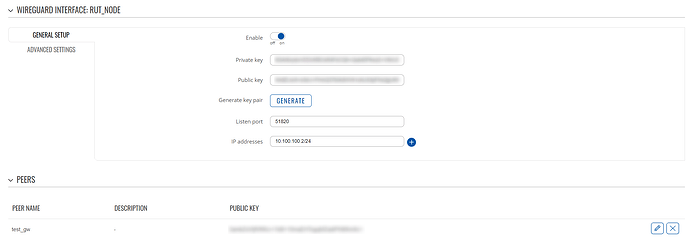
Wireguard instance settings:
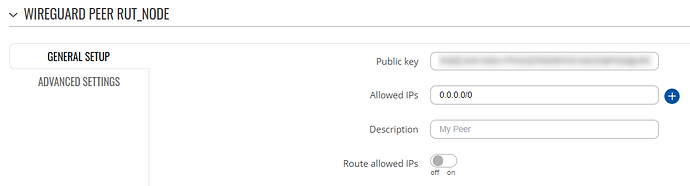
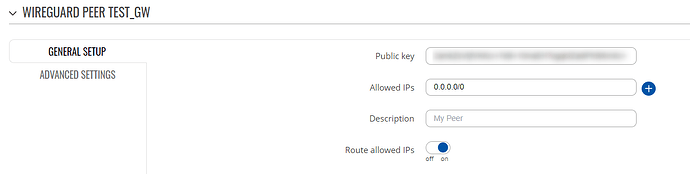
Wireguard peer settings:
Firewall settings:
-
RUTX10 (the node):
Wireguard instance settings:
Wireguard peer settings:
Firewall settings:
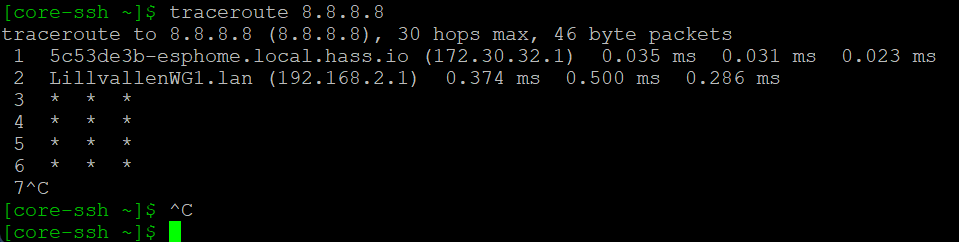
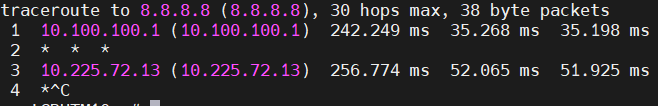
When running traceroute from the RUTX10 (the node), all packets are routed via the Wireguard tunnel:
Since your configuration seems to be similar, I’d recommend double checking the RUTXR1 firewall settings, as well as making sure the WireGuard tunnel is established. Make sure that the DNS servers are added on the WireGuard node separately, as that may be causing issues.
Best regards,
Hi.
I have now gone through the configuration settings you supplied and noticed some variations compared to my set-up. These are my findings when adjusting to your recommendations:
- The firewall settings in the gateway (Site A in my case) differ in how your setup shows “wan => REJECT”, while I had “wan => wireguard” previously. After some trial and error, I think I got the hang of how to create zone forwardings, and now my configuration matches yours. This unfortunately didn’t have any (apparent) effect, ie. status quo.
- Any attempt to turn off
Route allowed IPsin the wireguard Peer settings in site A, causes the tunnel traffic to fail. This is regardless if I allow all ips (0.0.0.0/0) or add in the site B network (192.168.2.0/24) or any other combination of networks. Turning off that switch just kills all traffic to and from site B (as viewed by me on site A). - If I do a traceroute from the diagnostic tools in OpenWRT on the site B router, then it can access 8.8.8.8, but that seems to go outside the wireguard tunnel. I conclude this from the IP addresses that the trace hops returns.
If I do the same from a client behind router B, then it can’t reach8.8.8.8, but I can see that it stays within the wireguard tunnel.
Regarding DNS; I did a simple ping to a FQDN from the site B client, and can see that name resoution seems to work just fine. (Although the ICMP echo does not, but that was expected.)
Hello,
Thank you for checking.
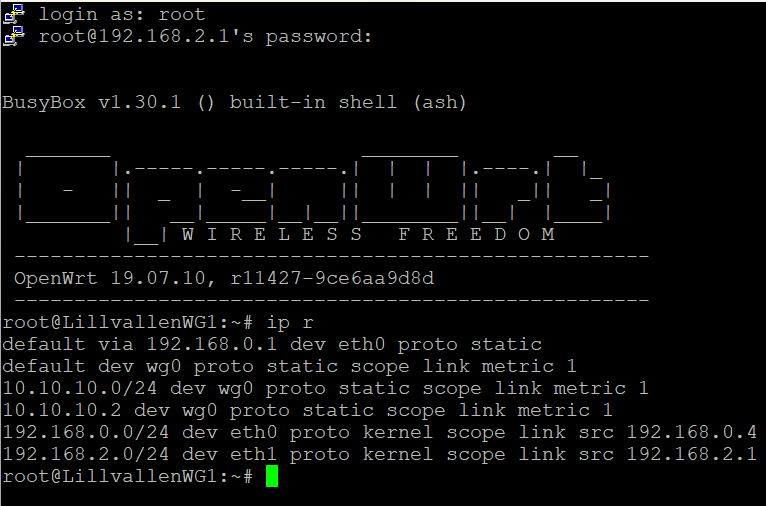
Could you post the output of ip r command on OpenWRT?
Make sure that Route Allowed IPs is enabled on 0.0.0.0/0 is specified as the routed network on the OpenWRT side. If the packets are being sent to the wrong interface, the issue may be related to the metric of Wireguard interface.
It should be noted that RUTXR1 should also have 0.0.0.0/0 as a routed address, as otherwise it will reject the packets.
Best regards,
Sure! This is the output of ip r when done from the console of the site B router:
Regarding the peer setting of site B, you can see it in post 8 above.
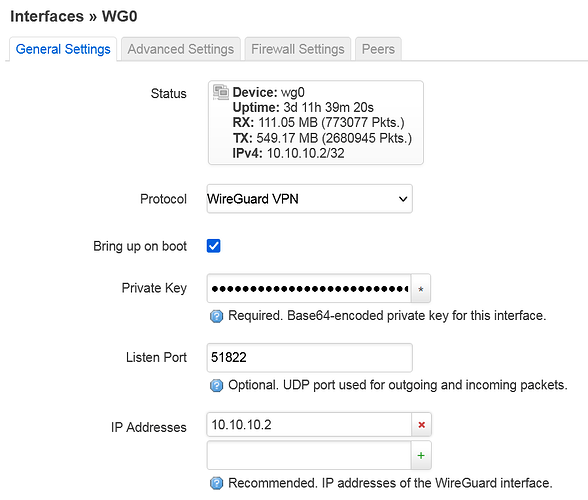
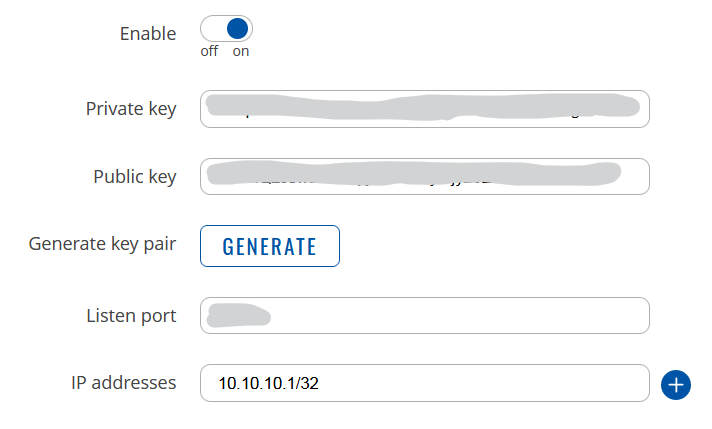
I’m sorry, but that last part about site A is unclear to me. Should I have the full ip range as Allowed IPs in the general setup for the Wireguard? Because right now I only have the tunnel IP (10.10.10.1/32) .
The peer settings however, have the full ip range: