Hello,
We have several sites with the same local IP subnet that we want to manage with remote vpn over an VPN hub. Basically what we want is use the vpn subnet as the management for the local lan via nat translation. Is this possible?
Hello,
We have several sites with the same local IP subnet that we want to manage with remote vpn over an VPN hub. Basically what we want is use the vpn subnet as the management for the local lan via nat translation. Is this possible?
Hello,
It is possible.
Performing NAT (specifically NETMAP) over a layer 3 VPN is usually not advisable, however, since RMS VPN currently offers only a layer 3 VPN, I will try to describe the process here.
For this, create an RMS hub and add your devices and users to the 'clients ’ tab. There, you should be able to set a static IP address for the devices as well. Here’s an example:
Then, add routes via your desired networks via corresponding devices and a route to your client with a full host address (/32):
On the devices themselves, configure the following iptables rules. In my case, RUT955 is on the 10.1.1.0/24 network, and RUTX11 is on the 10.1.2.0/24. Both have 192.168.1.0/24 LAN:
RUT955:
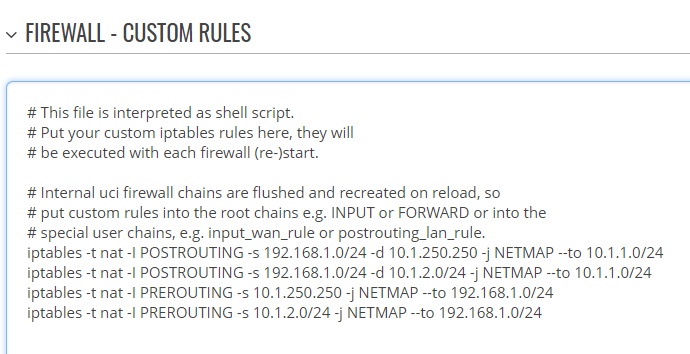
iptables -t nat -I POSTROUTING -s 192.168.1.0/24 -d 10.1.250.250 -j NETMAP --to 10.1.1.0/24
iptables -t nat -I POSTROUTING -s 192.168.1.0/24 -d 10.1.2.0/24 -j NETMAP --to 10.1.1.0/24
iptables -t nat -I PREROUTING -s 10.1.250.250 -j NETMAP --to 192.168.1.0/24
iptables -t nat -I PREROUTING -s 10.1.2.0/24 -j NETMAP --to 192.168.1.0/24
RUTX11:
iptables -t nat -I POSTROUTING -s 192.168.1.0/24 -d 10.1.250.250 -j NETMAP --to 10.1.2.0/24
iptables -t nat -I POSTROUTING -s 192.168.1.0/24 -d 10.1.1.0/24 -j NETMAP --to 10.1.2.0/24
iptables -t nat -I PREROUTING -s 10.1.250.250 -j NETMAP --to 192.168.1.0/24
iptables -t nat -I PREROUTING -s 10.1.1.0/24 -j NETMAP --to 192.168.1.0/24
Note: I’ve added prerouting and postrouting rules from RUT955 (10.1.1.0/24) to RUTX11 (10.1.2.0/24) and vice versa to enable communication between LANs as well. If you want to route only to a single client (10.1.250.250), you can adjust the rules accordingly.
Keep in mind that these rules can be executed directly from the command line (command line instructions are available here). However, these rules are lost on a device reboot. For these rules to retain after reboot, you can add them to custom firewall rules in Network → Firewall → Custom rules. The rules added on this page will be executed automatically after every reboot.
In case of any issues, please, try restarting the VPN Hub first. If the issues persists, restart the firewall service on the devices as well via the following command:
/etc/init.d/firewall restart
Kind Regards,
Hello Andzej,
I’ve followed your instructions.
The only thing I added/changed was the virtual ip address. That was still set to the default (192.168.255.0/24) and changed it to 10.1.250.0/24. After that it worked.
Could you further elaborate why performing NAT over a layer 3 VPN is usually not advisable?
Hello,
Glad to hear that this is working for you now.
Regarding your question. It was about performing NETMAP to route between identical networks. Mainly this is related to the scalability and network management aspects. As you introduce more devices, the challenge lies not only in configuring the new device but also in setting up iptable rules on the other devices if communication is required between the new device and the older devices. Any network modifications would require you to adjust rules and configurations across all devices that are using NETMAP.
However, if the NETMAP routing is directed only towards a singular management device (10.1.250.250), the complexity is somewhat mitigated. In this scenario, the approach should be fine.
Kind Regards,
Allright,
Thanks for the support.
This topic was automatically closed after 15 days. New replies are no longer allowed.