Is it posible to do a VPN with AWS?
Hello,
Yes, it is possible. You can create a VPN gateway and a site-to-site instance on AWS, then configure your RUT device for IPSec.
However, some changes will need to be made via the CLI/SSH. You can find instructions on how to access the CLI here: RutOS Command Line Interface (login using the username: root).
First, make sure that you are using the latest firmware available on your RUT device.
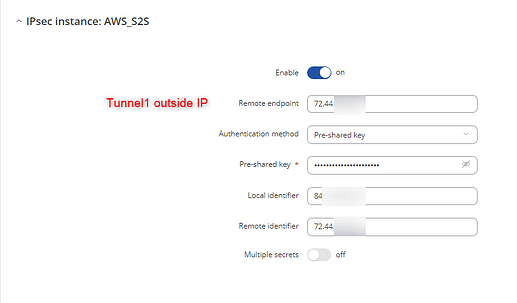
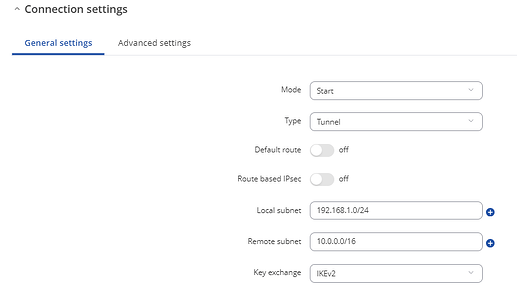
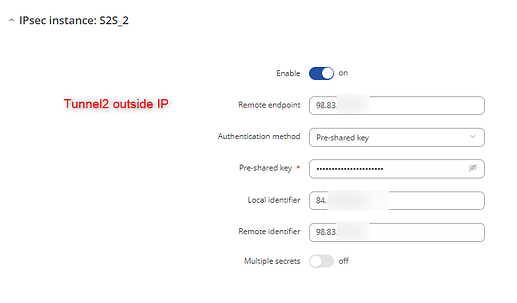
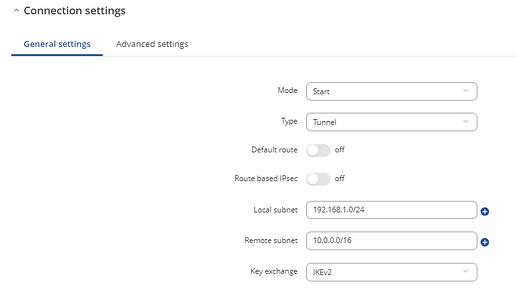
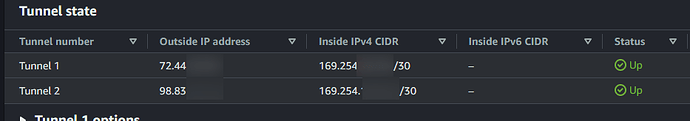
Then, configure IPSec. Here’s an example:
Tunnel1:
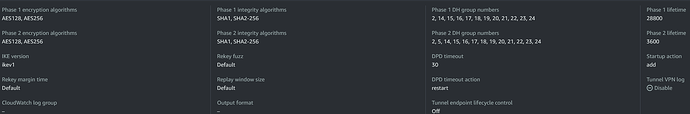
Advanced settings (tab):
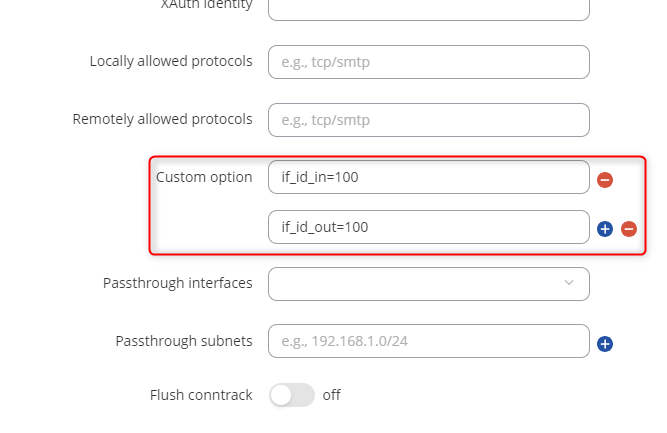
Tunnel2:
Advanced settings (tab):
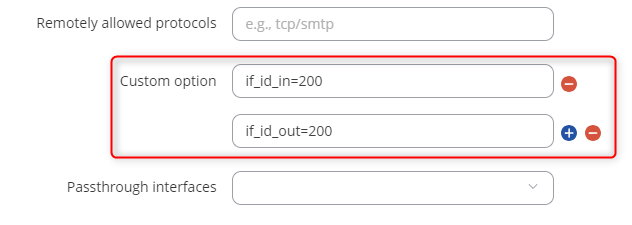
Access the router via CLI/SSH, and then edit the /etc/config/network file using the vi editor to make the necessary adjustments (vi /etc/config/network command).
/etc/config/network (replace IPs according to the AWS config - 169.254.x.x - Inside IPv4 IPs).
config rule 'ipsec_rule'
option action_group 'lookup'
option tos '0'
option priority '220'
option invert '0'
option lookup '220'
config interface 'ipsec1'
option mtu '1419'
option tunlink 'loopback'
option ifid '100'
option proto 'xfrm'
config interface 'ipsec1_static'
option proto 'static'
option ipaddr '169.254.xxx.xxx'
option netmask '255.255.255.252'
option device '@ipsec1'
option disabled '0'
config interface 'ipsec2'
option mtu '1419'
option tunlink 'loopback'
option ifid '200'
option proto 'xfrm'
config interface 'ipsec2_static'
option proto 'static'
option ipaddr '169.254.xxx.xxx'
option netmask '255.255.255.252'
option device '@ipsec2'
option disabled '0'
Make sure to restart the network and IPSec:
/etc/init.d/network restart
/etc/init.d/ipsec restart
Results:
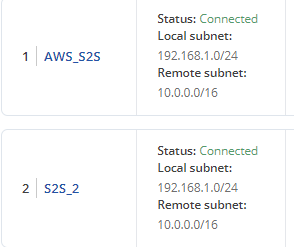
Hope this helps!
Kind Regards,
ill try this today, thanks for the help @AndzejJ
just one question
from what i see your setting the networks that are going to be able to pass from AWS to the TELTONIKA and viceversa that means thath the interesting traffic allow is 192.168.1.0/24 from TELTONIKA and 10.0.0.0/16 from AWS so
is it posible to use bgp or static routes with this method?
or the traffic is encrypted directly on the ipsec?
Hello @vivarock12,
You can modify the local/remove subnets as needed—what I provided is just an example.
Regarding BGP, it should work since the IPSec XFRM interface is available.
Additionally, I realized I forgot to include the screenshots from the IPSec ‘Advanced’ tab showing the if_id_in and if_id_out options. I’ll update my first response to include them, so please take a look.
Hope this helps!
Kind Regards,
im trying at the moment just one extra question in the //etc/config/network file:
config rule 'ipsec_rule'
option action_group 'lookup'
option tos '0'
option priority '220'
option invert '0'
option lookup '220'
config interface 'ipsec1'
option mtu '1419'
option tunlink 'loopback'
option ifid '100'
option proto 'xfrm'
config interface 'ipsec1_static'
option proto 'static'
option ipaddr '169.254.xxx.xxx'
option netmask '255.255.255.252'
option device '@ipsec1'
option disabled '0'
config interface 'ipsec2'
option mtu '1419'
option tunlink 'loopback'
option ifid '200'
option proto 'xfrm'
config interface 'ipsec2_static'
option proto 'static'
option ipaddr '169.254.xxx.xxx'
option netmask '255.255.255.252'
option device '@ipsec2'
option disabled '0'
what is the OPTION DEVICE ‘@ipsecX’
is the name of the VPN ipsec vpn or i just let it like that becasusa i already have a DMVPN running so it should have ‘@ipsec2’ and ‘@ipsec3’? or how ?
i think they are refering to the ones we created before forget about it.
so with the extra options your telling the ipsec tunnel to permit the traffic from the interface:
config interface 'ipsec1'
option ifid '100'
option proto 'xfrm'
with the id 100 to pass traffic through the tunnel
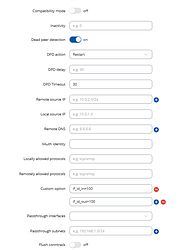
im getting stuck with DPD with are the logs on the TELTONIKA
Tue Oct 15 04:40:09 2024 daemon.info ipsec: 13[ENC] <AWS_PRIM-AWS_PRIM_c|2> parsed INFORMATIONAL_V1 request 846498007 [ HASH N(DPD) ]
Tue Oct 15 04:40:09 2024 daemon.info ipsec: 13[ENC] <AWS_PRIM-AWS_PRIM_c|2> generating INFORMATIONAL_V1 request 1251989080 [ HASH N(DPD_ACK) ]
Tue Oct 15 04:40:09 2024 daemon.info ipsec: 13[NET] <AWS_PRIM-AWS_PRIM_c|2> sending packet: from PUBLIC_TELTONIKA[4500] to PUBLIC_AWS[4500] (92 bytes)
Tue Oct 15 04:40:19 2024 daemon.info ipsec: 05[NET] <AWS_PRIM-AWS_PRIM_c|2> received packet: from PUBLIC_AWS[4500] to PUBLIC_TELTONIKA[4500] (92 bytes)
Tue Oct 15 04:40:19 2024 daemon.info ipsec: 05[ENC] <AWS_PRIM-AWS_PRIM_c|2> parsed INFORMATIONAL_V1 request 4027976226 [ HASH N(DPD) ]
Tue Oct 15 04:40:19 2024 daemon.info ipsec: 05[ENC] <AWS_PRIM-AWS_PRIM_c|2> generating INFORMATIONAL_V1 request 60564778 [ HASH N(DPD_ACK) ]
Tue Oct 15 04:40:19 2024 daemon.info ipsec: 05[NET] <AWS_PRIM-AWS_PRIM_c|2> sending packet: from PUBLIC_TELTONIKA[4500] to PUBLIC_AWS[4500] (92 bytes)
Tue Oct 15 04:40:32 2024 daemon.info ipsec: 00[IKE] <AWS_PRIM-AWS_PRIM_c|2> closing CHILD_SA AWS_PRIM-AWS_PRIM_c{1} with SPIs c069f293_i (360 bytes) cb1deef9_o (0 bytes) and TS 10.10.0.0/24 === 172.31.0.0/16
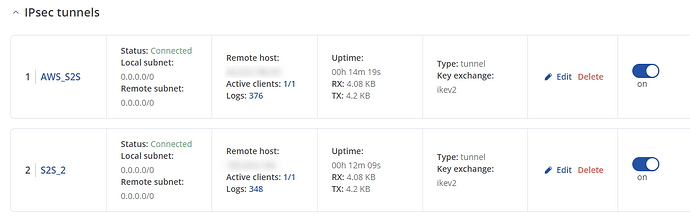
the configuration on the AWS SIDE
and here the teltonika config for ipsec advanced settings:
and the phases
1
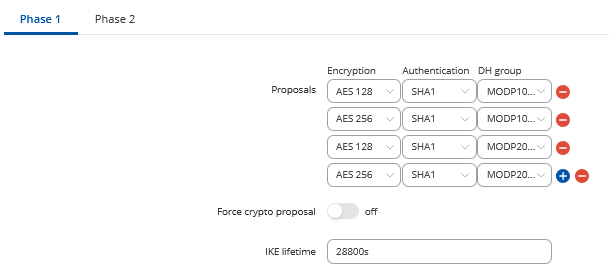
2
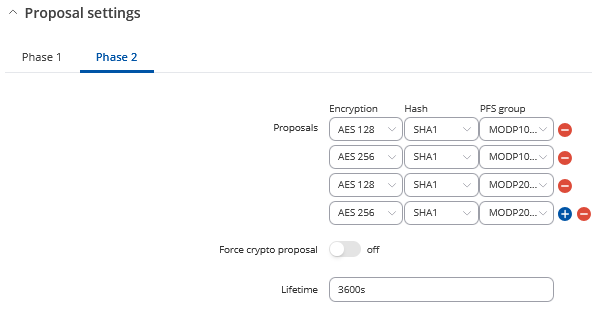
@AndzejJ i dont know if theres any recomendation for the DPD trouble im getting?
@vivarock12 Hello,
You currently have a timeout of 30 seconds configured for DPD. Please, adjust the DPD delay option to be something lower, like 10 seconds. So something like:
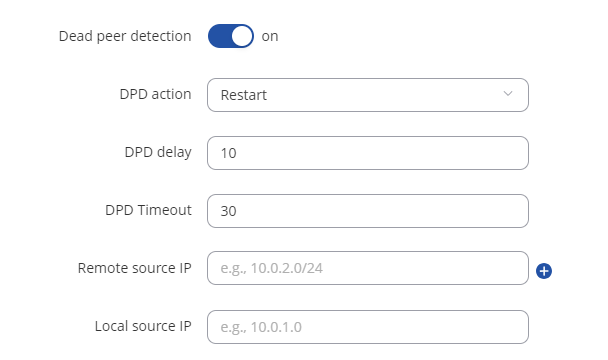
I suggest downloading a configuration from AWS (generic type) and make sure that you have configured everything properly.
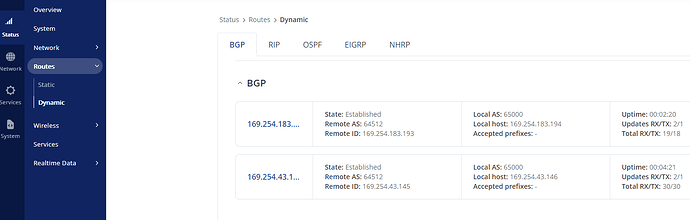
BGP seems to work fine as well:
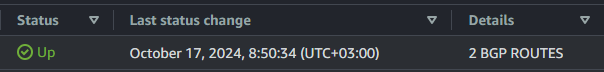
Hope this helps!
Kind Regards,
This topic was automatically closed after 15 days. New replies are no longer allowed.