Not an expert user, but with the help of this forum and others I have a wireguard instance/tunnel and a peer to a commercial VPN provider. The wg command in CLI indicates a handshake takes place so the tunnel should be established. But the provider indicates devices are not using the tunnel.
This is true regardless of whether I use 0.0.0.0/0 or 0.0.0.0/1 + 128.0.0.0/1 as Allowed IPs. If I turn ‘Route allowed IPs’ on I lose internet connectivity. The VPN provider is not the problem as I can tunnel directly from a device.
I have updated the firmware.
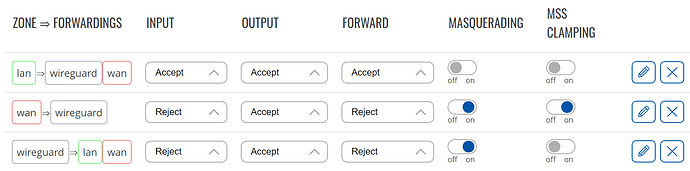
Firewall arrangement according to wiki pages I found:
Any help would be appreciated.
Hello,
Sending all traffic through the wg interface is tricky, an exception for the wg server at the other end itself is required else all frames will be lost.
The way to do that is to create a route to the wg server, with a higher priority than the one of the wg interface:
- edit the wg interface parameters, set the metric to 3 in Advanced settings,
- create a static route to the wg server from a ssh console or the Network->Routing menu with metric less than 3, like this one:
ip -4 route add ip-of-server dev qmimux0 metric 2
Regards,
Thank you. Setting wg interface metric to 3 is done.
In the Network->Routing menu I find the static route settings but I am unsure what to put where to get the definitions, route and priority right. Is this it?
(inserting interface as gateway - otherwise it seems to me routing will be straight to the provider server and bypass the wg interface in the router?)
After save & apply this does not come up under status->routes and my provider says I am not using the tunnel regardless of whether I insert the interface or not.
Sorry to be daft in the eyes of the experienced, but I really haven’t had to deal with the mechanics of internet & routing before.
You don’t need to set the IPv4 Gateway field, just clear it. The interface is enough.
Do you use de wan or mobile interface for access to the outside world ?
Be sure to have the correct Target field value.
I didn’t check carefully before but your firewall settings are pretty restrictive, set wan=>wireguard and wireguard=>wan to Accept/Accept/Accept at least for testing.
The IPv4 Gateway field is clear and the firewall settings are loose for testing, but no luck.
The added route has now appeared under Status->Routes. There I now have a lan route metric 1, three wan routes metric 2 (zero, router IP and VPN endpoint IP as respective targets) and my wireguard interface with metric 3.
The VPN endpoint has also appeared under ARP under Status->Routes, with wan as its interface. I probably misunderstand what is going on, but it seems to me the route that I want has the lowest priority.
Lowest metric is highest priority.
Could you show the output of:
ip -4 route show
ifconfig
Output of ip -4 route show:
default via 192.168.1.1 dev eth1 proto static src 192.168.1.3 metric 2
(IP+MASK AS IN INTERFACE ADDRESS) dev (NAME OF INTERFACE) proto static scope link metric 3
(IP ENDPOINT OF VPN) dev eth1 proto static scope link metric 2
192.168.1.0/24 dev br-lan proto static scope link metric 1
192.168.1.0/24 dev eth1 proto static scope link metric 2
ifconf yields a very long reply with lots of hardware addresses etc that I’m not sure I should be posting. Is there something specific we are looking for?
What is the value of NAME OF INTERFACE ? Of IP + MASK ? It is hard to see what is going on without a clear picture.
The ip -4 route show was executed when the wg interface was down. Correct ?
Could you summarily describe your network ?
The name of interface is just the name I made up for the wg interface, the one I input when I added the wireguard.
Before and after the ip-4 route show I also requested wg and it came back with a recent (minutes, not seconds, and the same one both times) handshake and very low traffic.
May I see the output of the wg command ? Of ip -4 route show when the tunnel is active ?
Set Allowed IPs to 0.0.0.0/1 + 128.0.0.0/1 in order to avoid confusion with the default route.
Sorry, forgot you asked about the network. Teltonika X10 (ie no SIM) behind another router which in turn is connected to a media converter and an optical receiver working out towards the internet.
The idea is to have one network (wifi or wired) through the Teltonika automatically on VPN and another network for guests and traffic with no VPN.
I get the same results when I plug the media converter straight into the Teltonika router.
So now what is the result with the special metric 2 route active and Allowed Ips set to 0.0.0.0/1 + 128.0.0.0/1 + ::/0 ?
Do you still loose Internet access ?
interface: (AS NAMED)
public key: W6QzSMF7hlqasTfSQNxcFPFtZqbOdgNHL2uMqYyekFo=
private key: (hidden)
listening port: 48574
peer: ipW9/ysMc9vQbg/x7WK/udnl06+NJioWZZ4XIqz4PQY=
endpoint: (XX)
allowed ips: 0.0.0.0/1, 128.0.0.0/1
latest handshake: 18 seconds ago
transfer: 92 B received, 180 B sent
persistent keepalive: every 25 seconds
root@RUTX10:~# p -4 route show
default via 192.168.1.1 dev eth1 proto static src 192.168.1.3 metric 2
(INTERFACE IP) dev Residens proto static scope link metric 3
(XX?) dev eth1 proto static scope link metric 2
192.168.1.0/24 dev br-lan proto static scope link metric 1
192.168.1.0/24 dev eth1 proto static scope link metric 2
(XX) and (XX?) are not the same. And the peer one (XX?) I don’t recognize from before. Endpoint in settings is given as a web address so not sure if I can be directed to different serve endpoints dynamically.
I have internet access all the time. But nothing is routed through the VPN when I check on the provider’s site.
Another way to see that is in the output of the wg command. Have you enabled “Route Allowed IPs” ?
(added ::/0 to the list but no change)
Enabling Route Allowed IPs cuts my internet access.
Could you describe the difference ? How do they resolve ? Do a nslookup XX and nslookup XX?
Sorry, lost history when my session timed out and had to log in again.
I redid the exercise, now they are different but each a static IP associated to my VPN provider.
I copied the same thing from when I enabled Route Allowed IPs and I did not have internet access and got the first as a static from my provider, the second was 128.0.0.0
I won’t be able to help you without a clear picture of the IP addresses / routes etc involved.