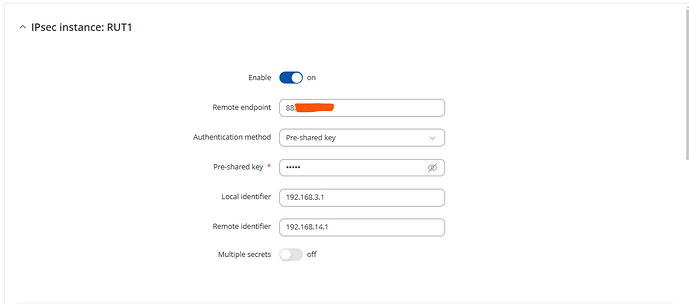
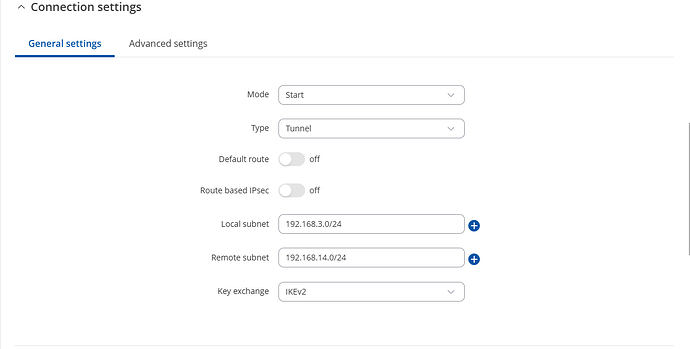
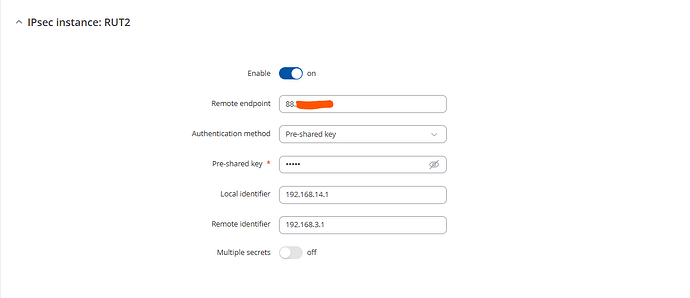
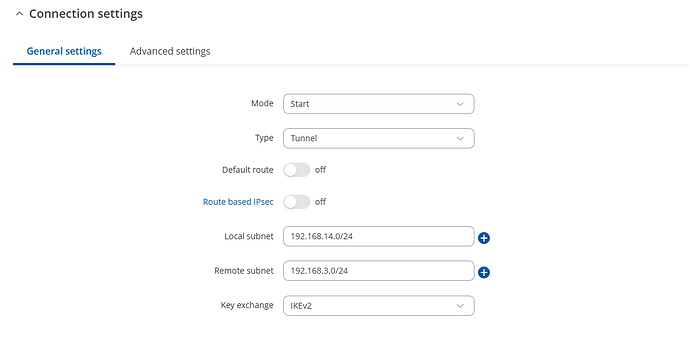
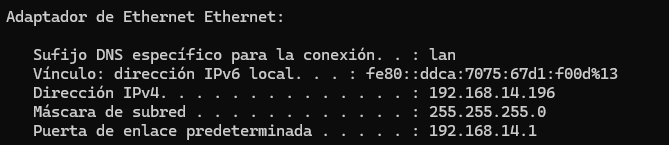
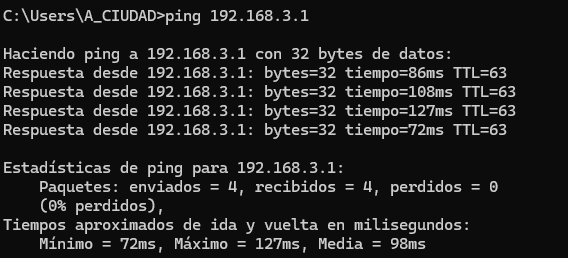
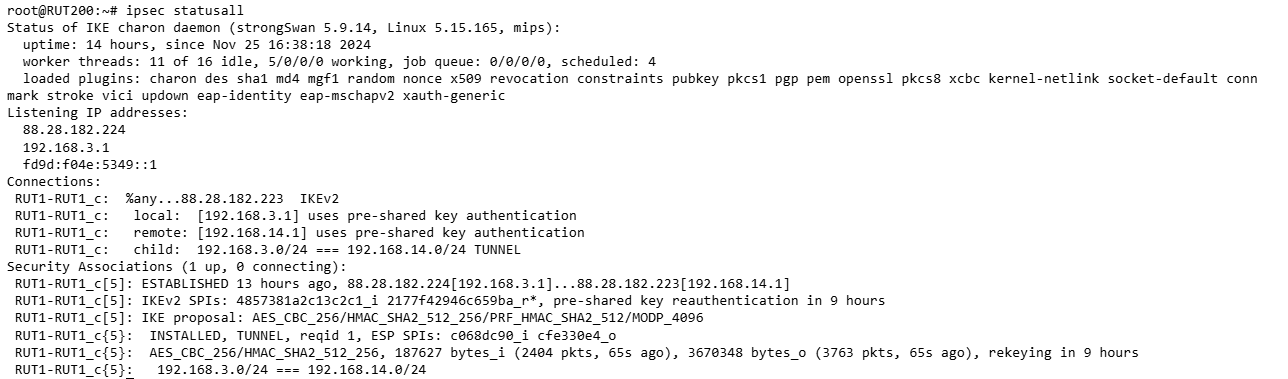
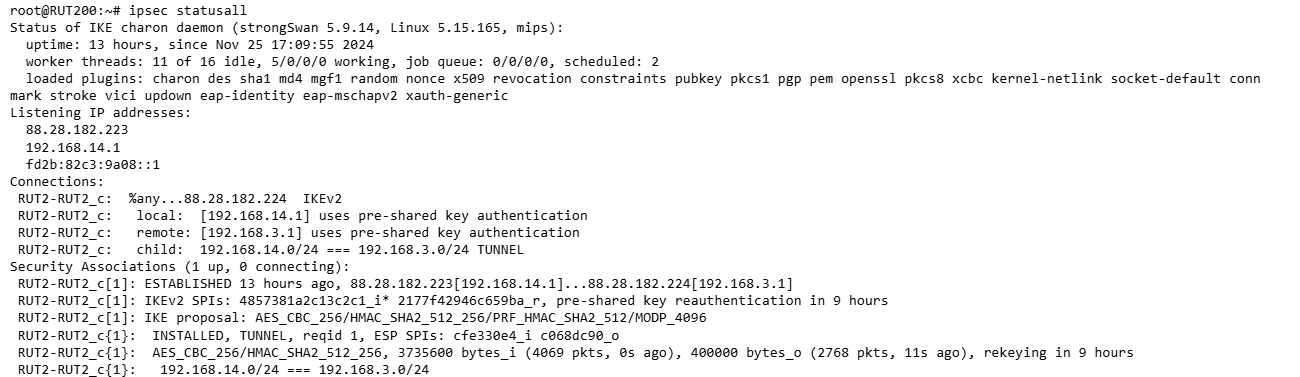
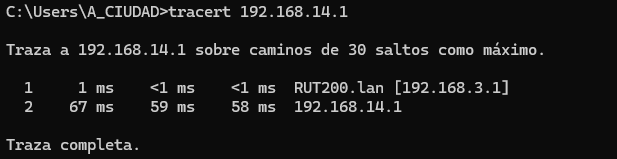
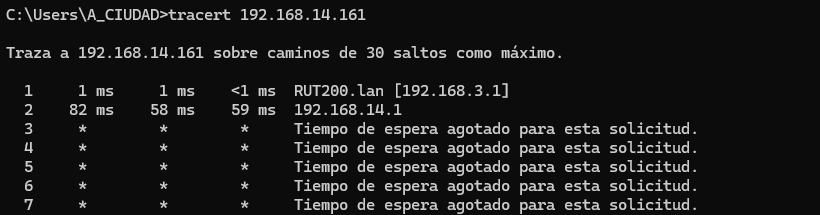
Hi @flebourse,
The data obtained by doing tcpdump, is as follows:
RUT1 → RUT2:
root@RUT200:~# tcpdump -i any -n -v icmp
tcpdump: data link type LINUX_SLL2
tcpdump: listening on any, link-type LINUX_SLL2 (Linux cooked v2), snapshot length 262144 bytes
10:20:05.467916 usb0 In IP (tos 0x0, ttl 64, id 64917, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.14.1 > 192.168.3.1: ICMP echo request, id 8858, seq 1, length 64
10:20:05.887105 usb0 Out IP (tos 0xc0, ttl 64, id 51758, offset 0, flags [none], proto ICMP (1), length 68)
88.28.182.224 > 91.228.165.148: ICMP host 88.28.182.224 unreachable, length 48
IP (tos 0x0, ttl 47, id 18682, offset 0, flags [DF], proto TCP (6), length 40)
91.228.165.148.8883 > 88.28.182.224.5016: Flags [F.], cksum 0xb2c6 (correct), seq 434732515, ack 1350749675, win 18, length 0
10:20:05.887310 usb0 Out IP (tos 0xc0, ttl 64, id 51759, offset 0, flags [none], proto ICMP (1), length 68)
88.28.182.224 > 91.228.165.148: ICMP host 88.28.182.224 unreachable, length 48
IP (tos 0x0, ttl 47, id 18683, offset 0, flags [DF], proto TCP (6), length 40)
91.228.165.148.8883 > 88.28.182.224.5016: Flags [F.], cksum 0xb2c6 (correct), seq 0, ack 1, win 18, length 0
10:20:06.504919 usb0 In IP (tos 0x0, ttl 64, id 64995, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.14.1 > 192.168.3.1: ICMP echo request, id 8858, seq 2, length 64
10:20:06.984907 usb0 In IP (tos 0xc0, ttl 64, id 65044, offset 0, flags [none], proto ICMP (1), length 116)
192.168.14.1 > 192.168.3.1: ICMP host 192.168.14.196 unreachable, length 96
IP (tos 0x0, ttl 63, id 21185, offset 0, flags [DF], proto TCP (6), length 88)
192.168.3.1.4218 > 192.168.14.196.42149: Flags [.], cksum 0x4700 (correct), seq 2705280711:2705280759, ack 986542620, win 4005, length 48
10:20:06.986166 usb0 In IP (tos 0xc0, ttl 64, id 65045, offset 0, flags [none], proto ICMP (1), length 116)
192.168.14.1 > 192.168.3.1: ICMP host 192.168.14.196 unreachable, length 96
IP (tos 0x0, ttl 63, id 21186, offset 0, flags [DF], proto TCP (6), length 88)
192.168.3.1.4218 > 192.168.14.196.42149: Flags [.], cksum 0x4700 (correct), seq 0:48, ack 1, win 4005, length 48
10:20:06.986785 usb0 In IP (tos 0xc0, ttl 64, id 65046, offset 0, flags [none], proto ICMP (1), length 116)
192.168.14.1 > 192.168.3.1: ICMP host 192.168.14.196 unreachable, length 96
IP (tos 0x0, ttl 63, id 21187, offset 0, flags [DF], proto TCP (6), length 88)
192.168.3.1.4218 > 192.168.14.196.42149: Flags [.], cksum 0x4700 (correct), seq 0:48, ack 1, win 4005, length 48
10:20:07.467789 usb0 In IP (tos 0x0, ttl 64, id 65054, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.14.1 > 192.168.3.1: ICMP echo request, id 8858, seq 3, length 64
10:20:08.475891 usb0 In IP (tos 0x0, ttl 64, id 65102, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.14.1 > 192.168.3.1: ICMP echo request, id 8858, seq 4, length 64
10:20:09.087089 usb0 Out IP (tos 0xc0, ttl 64, id 51964, offset 0, flags [none], proto ICMP (1), length 68)
88.28.182.224 > 91.228.165.148: ICMP host 88.28.182.224 unreachable, length 48
IP (tos 0x0, ttl 47, id 18684, offset 0, flags [DF], proto TCP (6), length 40)
91.228.165.148.8883 > 88.28.182.224.5016: Flags [F.], cksum 0xb2c6 (correct), seq 0, ack 1, win 18, length 0
10:20:09.087373 usb0 Out IP (tos 0xc0, ttl 64, id 51965, offset 0, flags [none], proto ICMP (1), length 68)
88.28.182.224 > 91.228.165.148: ICMP host 88.28.182.224 unreachable, length 48
IP (tos 0x0, ttl 47, id 18685, offset 0, flags [DF], proto TCP (6), length 40)
91.228.165.148.8883 > 88.28.182.224.5016: Flags [F.], cksum 0xb2c6 (correct), seq 0, ack 1, win 18, length 0
10:20:09.467921 usb0 In IP (tos 0x0, ttl 64, id 65156, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.14.1 > 192.168.3.1: ICMP echo request, id 8858, seq 5, length 64
10:20:10.114049 usb0 In IP (tos 0xc0, ttl 64, id 65213, offset 0, flags [none], proto ICMP (1), length 116)
192.168.14.1 > 192.168.3.1: ICMP host 192.168.14.196 unreachable, length 96
IP (tos 0x0, ttl 63, id 21188, offset 0, flags [DF], proto TCP (6), length 88)
192.168.3.1.4218 > 192.168.14.196.42149: Flags [.], cksum 0x4700 (correct), seq 0:48, ack 1, win 4005, length 48
10:20:10.114052 usb0 In IP (tos 0xc0, ttl 64, id 65214, offset 0, flags [none], proto ICMP (1), length 116)
192.168.14.1 > 192.168.3.1: ICMP host 192.168.14.196 unreachable, length 96
IP (tos 0x0, ttl 63, id 21189, offset 0, flags [DF], proto TCP (6), length 88)
192.168.3.1.4218 > 192.168.14.196.42149: Flags [.], cksum 0x4700 (correct), seq 0:48, ack 1, win 4005, length 48
10:20:10.115740 usb0 In IP (tos 0xc0, ttl 64, id 65215, offset 0, flags [none], proto ICMP (1), length 116)
192.168.14.1 > 192.168.3.1: ICMP host 192.168.14.196 unreachable, length 96
192.168.3.1.4218 > 192.168.14.196.42149: Flags [.], cksum 0x4700 (correct), seq 0:48, ack 1, win 4005, length 48
10:20:10.467770 usb0 In IP (tos 0x0, ttl 64, id 65220, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.14.1 > 192.168.3.1: ICMP echo request, id 8858, seq 6, length 64
10:20:11.467920 usb0 In IP (tos 0x0, ttl 64, id 65257, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.14.1 > 192.168.3.1: ICMP echo request, id 8858, seq 7, length 64
10:20:12.287049 usb0 Out IP (tos 0xc0, ttl 64, id 52162, offset 0, flags [none], proto ICMP (1), length 68)
88.28.182.224 > 91.228.165.148: ICMP host 88.28.182.224 unreachable, length 48
IP (tos 0x0, ttl 47, id 18686, offset 0, flags [DF], proto TCP (6), length 40)
91.228.165.148.8883 > 88.28.182.224.5016: Flags [F.], cksum 0xb2c6 (correct), seq 0, ack 1, win 18, length 0
10:20:12.287300 usb0 Out IP (tos 0xc0, ttl 64, id 52163, offset 0, flags [none], proto ICMP (1), length 68)
88.28.182.224 > 91.228.165.148: ICMP host 88.28.182.224 unreachable, length 48
IP (tos 0x0, ttl 47, id 18687, offset 0, flags [DF], proto TCP (6), length 40)
91.228.165.148.8883 > 88.28.182.224.5016: Flags [F.], cksum 0xb2c6 (correct), seq 0, ack 1, win 18, length 0
10:20:12.504919 usb0 In IP (tos 0x0, ttl 64, id 65278, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.14.1 > 192.168.3.1: ICMP echo request, id 8858, seq 8, length 64
10:20:13.224927 usb0 In IP (tos 0xc0, ttl 64, id 65304, offset 0, flags [none], proto ICMP (1), length 116)
192.168.14.1 > 192.168.3.1: ICMP host 192.168.14.196 unreachable, length 96
IP (tos 0x0, ttl 63, id 21191, offset 0, flags [DF], proto TCP (6), length 88)
192.168.3.1.4218 > 192.168.14.196.42149: Flags [.], cksum 0x4700 (correct), seq 0:48, ack 1, win 4005, length 48
10:20:13.226214 usb0 In IP (tos 0xc0, ttl 64, id 65305, offset 0, flags [none], proto ICMP (1), length 116)
192.168.14.1 > 192.168.3.1: ICMP host 192.168.14.196 unreachable, length 96
IP (tos 0x0, ttl 63, id 21192, offset 0, flags [DF], proto TCP (6), length 88)
192.168.3.1.4218 > 192.168.14.196.42149: Flags [.], cksum 0x4700 (correct), seq 0:48, ack 1, win 4005, length 48
10:20:13.226217 usb0 In IP (tos 0xc0, ttl 64, id 65306, offset 0, flags [none], proto ICMP (1), length 116)
192.168.14.1 > 192.168.3.1: ICMP host 192.168.14.196 unreachable, length 96
IP (tos 0x0, ttl 63, id 21193, offset 0, flags [DF], proto TCP (6), length 88)
192.168.3.1.4218 > 192.168.14.196.42149: Flags [.], cksum 0x4700 (correct), seq 0:48, ack 1, win 4005, length 48
10:20:13.467756 usb0 In IP (tos 0x0, ttl 64, id 65319, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.14.1 > 192.168.3.1: ICMP echo request, id 8858, seq 9, length 64
10:20:14.477760 usb0 In IP (tos 0x0, ttl 64, id 65338, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.14.1 > 192.168.3.1: ICMP echo request, id 8858, seq 10, length 64
10:20:15.478000 usb0 In IP (tos 0x0, ttl 64, id 65408, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.14.1 > 192.168.3.1: ICMP echo request, id 8858, seq 11, length 64
10:20:15.487076 usb0 Out IP (tos 0xc0, ttl 64, id 52464, offset 0, flags [none], proto ICMP (1), length 68)
88.28.182.224 > 91.228.165.148: ICMP host 88.28.182.224 unreachable, length 48
IP (tos 0x0, ttl 47, id 18688, offset 0, flags [DF], proto TCP (6), length 40)
91.228.165.148.8883 > 88.28.182.224.5016: Flags [F.], cksum 0xb2c6 (correct), seq 0, ack 1, win 18, length 0
10:20:15.487299 usb0 Out IP (tos 0xc0, ttl 64, id 52465, offset 0, flags [none], proto ICMP (1), length 68)
88.28.182.224 > 91.228.165.148: ICMP host 88.28.182.224 unreachable, length 48
IP (tos 0x0, ttl 47, id 18689, offset 0, flags [DF], proto TCP (6), length 40)
91.228.165.148.8883 > 88.28.182.224.5016: Flags [F.], cksum 0xb2c6 (correct), seq 0, ack 1, win 18, length 0
10:20:16.352911 usb0 In IP (tos 0xc0, ttl 64, id 65490, offset 0, flags [none], proto ICMP (1), length 116)
192.168.14.1 > 192.168.3.1: ICMP host 192.168.14.196 unreachable, length 96
IP (tos 0x0, ttl 63, id 21194, offset 0, flags [DF], proto TCP (6), length 88)
192.168.3.1.4218 > 192.168.14.196.42149: Flags [.], cksum 0x4700 (correct), seq 0:48, ack 1, win 4005, length 48
10:20:16.352914 usb0 In IP (tos 0xc0, ttl 64, id 65491, offset 0, flags [none], proto ICMP (1), length 116)
192.168.14.1 > 192.168.3.1: ICMP host 192.168.14.196 unreachable, length 96
IP (tos 0x0, ttl 63, id 21195, offset 0, flags [DF], proto TCP (6), length 88)
192.168.3.1.4218 > 192.168.14.196.42149: Flags [.], cksum 0x4700 (correct), seq 0:48, ack 1, win 4005, length 48
10:20:16.354616 usb0 In IP (tos 0xc0, ttl 64, id 65492, offset 0, flags [none], proto ICMP (1), length 116)
192.168.14.1 > 192.168.3.1: ICMP host 192.168.14.196 unreachable, length 96
IP (tos 0x0, ttl 63, id 21196, offset 0, flags [DF], proto TCP (6), length 88)
192.168.3.1.4218 > 192.168.14.196.42149: Flags [.], cksum 0x4700 (correct), seq 0:48, ack 1, win 4005, length 48
^C
31 packets captured
34 packets received by filter
0 packets dropped by kernel
RUT2->RU1:
root@RUT200:~# tcpdump -i any -n -v icmp
tcpdump: data link type LINUX_SLL2
tcpdump: listening on any, link-type LINUX_SLL2 (Linux cooked v2), snapshot length 262144 bytes
10:10:54.189294 usb0 In IP (tos 0x0, ttl 64, id 52308, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.3.1 > 192.168.14.1: ICMP echo request, id 9457, seq 2, length 64
10:10:55.189428 usb0 In IP (tos 0x0, ttl 64, id 52386, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.3.1 > 192.168.14.1: ICMP echo request, id 9457, seq 3, length 64
10:10:56.190411 usb0 In IP (tos 0x0, ttl 64, id 52481, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.3.1 > 192.168.14.1: ICMP echo request, id 9457, seq 4, length 64
10:10:57.189426 usb0 In IP (tos 0x0, ttl 64, id 52560, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.3.1 > 192.168.14.1: ICMP echo request, id 9457, seq 5, length 64
10:10:58.165127 usb0 In IP (tos 0x0, ttl 64, id 52572, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.3.1 > 192.168.14.1: ICMP echo request, id 9457, seq 6, length 64
10:10:59.189301 usb0 In IP (tos 0x0, ttl 64, id 52593, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.3.1 > 192.168.14.1: ICMP echo request, id 9457, seq 7, length 64
10:11:00.230419 usb0 In IP (tos 0x0, ttl 64, id 52642, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.3.1 > 192.168.14.1: ICMP echo request, id 9457, seq 8, length 64
10:11:01.189424 usb0 In IP (tos 0x0, ttl 64, id 52653, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.3.1 > 192.168.14.1: ICMP echo request, id 9457, seq 9, length 64
10:11:02.184422 usb0 In IP (tos 0x0, ttl 64, id 52709, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.3.1 > 192.168.14.1: ICMP echo request, id 9457, seq 10, length 64
10:11:03.184290 usb0 In IP (tos 0x0, ttl 64, id 52768, offset 0, flags [DF], proto ICMP (1), length 84)
10:11:04.189188 usb0 In IP (tos 0x0, ttl 64, id 52784, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.3.1 > 192.168.14.1: ICMP echo request, id 9457, seq 12, length 64
10:11:05.189317 usb0 In IP (tos 0x0, ttl 64, id 52880, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.3.1 > 192.168.14.1: ICMP echo request, id 9457, seq 13, length 64
10:11:06.229414 usb0 In IP (tos 0x0, ttl 64, id 52909, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.3.1 > 192.168.14.1: ICMP echo request, id 9457, seq 14, length 64
10:11:07.189414 usb0 In IP (tos 0x0, ttl 64, id 52998, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.3.1 > 192.168.14.1: ICMP echo request, id 9457, seq 15, length 64
10:11:08.229422 usb0 In IP (tos 0x0, ttl 64, id 53023, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.3.1 > 192.168.14.1: ICMP echo request, id 9457, seq 16, length 64
10:11:09.205285 usb0 In IP (tos 0x0, ttl 64, id 53043, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.3.1 > 192.168.14.1: ICMP echo request, id 9457, seq 17, length 64
10:11:10.229308 usb0 In IP (tos 0x0, ttl 64, id 53103, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.3.1 > 192.168.14.1: ICMP echo request, id 9457, seq 18, length 64
10:11:11.189438 usb0 In IP (tos 0x0, ttl 64, id 53160, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.3.1 > 192.168.14.1: ICMP echo request, id 9457, seq 19, length 64
^C
18 packets captured
21 packets received by filter
0 packets dropped by kernel
I have done the VPN between the two and I get the same error again. I can’t reach the connected device on the opposite LAN.