Thx for reaching out to me. I read the topic about the FRITZ!box connection which you mentioned already - I believe the group discussing it didn’t get it to work. Finally the author switched to wireguard.
I would use wireguard as well, unfortunately my 6 years old FRITZ!box only supports IPsec with the limited settings I posted.
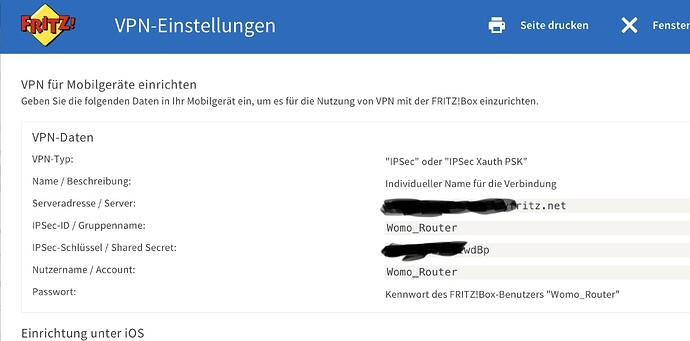
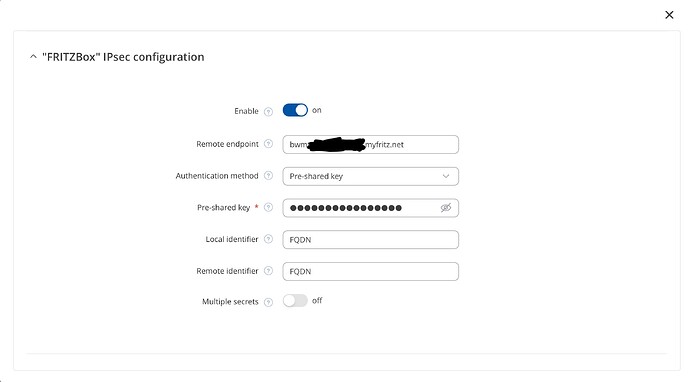
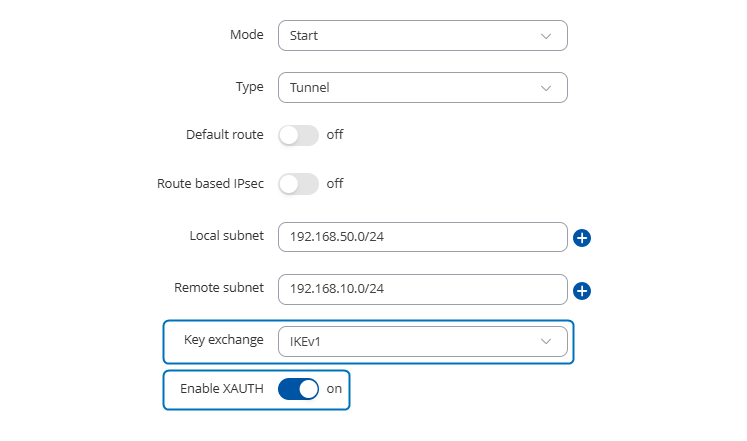
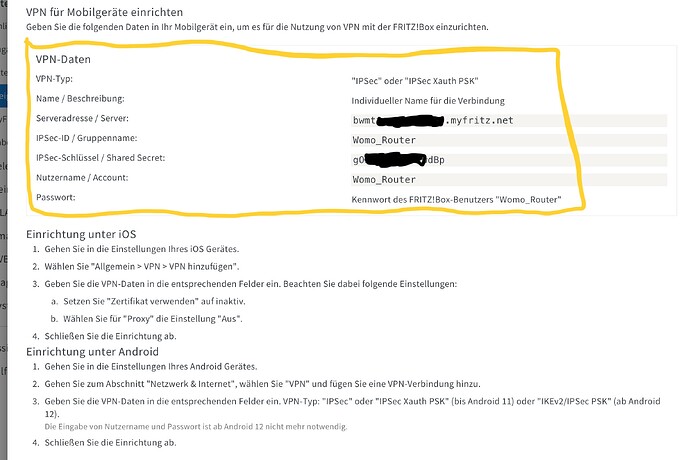
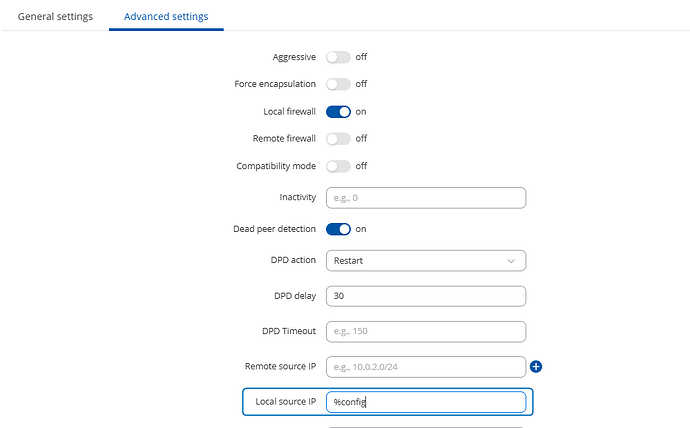
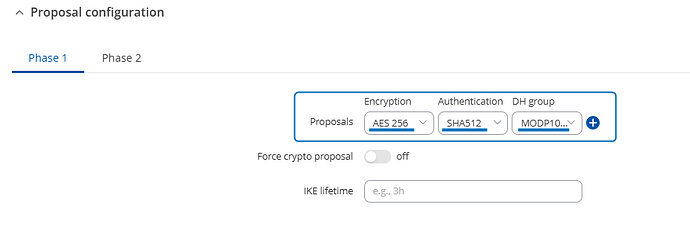
About Cisco : I want to connect the rutc50 to my FRITZ!Box using IPsec protocol, as this is the only option my FRITZ!box has.
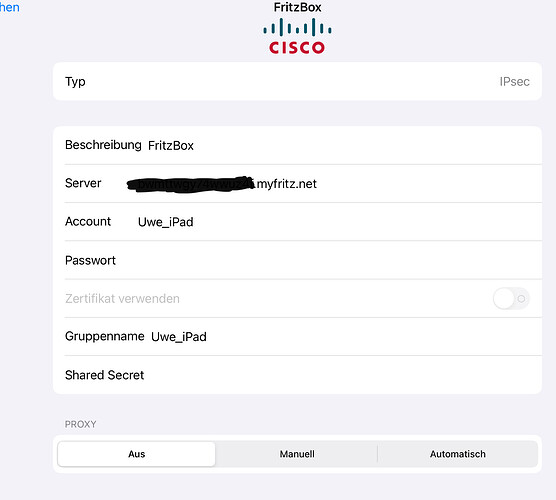
The ‚CISCO‘ comes into the picture as on the iPhone ( 15 pro max ) and iPad this connection to this FRITZ!box is labeled with ‚CISCO‘, no idea why.
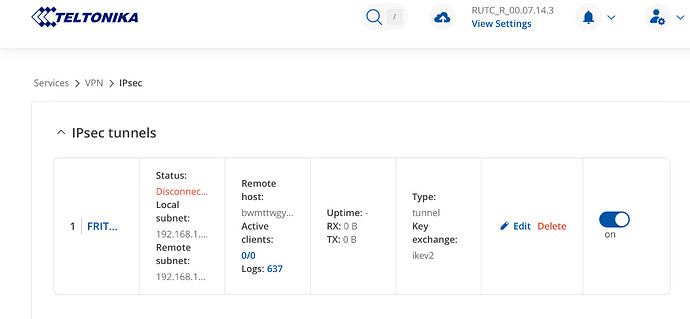
Here the logs ( last minutes from today ) and screenshots
315576 Wed Jun 4 08:35:34 2025 daemon.info ipsec: 15[NET] <FRITZBox|10896> sending packet: from 2a02:3031:212:9444:b16b:6dda:13c8:e8ee[4500] to 2a02:8108:0:60::2bf[4500] (528 bytes)
315577 Wed Jun 4 08:35:34 2025 daemon.info ipsec: 07[NET] <FRITZBox|10896> received packet: from 2a02:8108:0:60::2bf[4500] to 2a02:3031:212:9444:b16b:6dda:13c8:e8ee[4500] (96 bytes)
315578 Wed Jun 4 08:35:34 2025 daemon.info ipsec: 07[ENC] <FRITZBox|10896> parsed IKE_AUTH response 1 [ N(AUTH_FAILED) ]
315579 Wed Jun 4 08:35:34 2025 daemon.info ipsec: 07[IKE] <FRITZBox|10896> received AUTHENTICATION_FAILED notify error
315580 Wed Jun 4 08:36:03 2025 daemon.info ipsec: 14[IKE] <FRITZBox|10897> initiating IKE_SA FRITZBox[10897] to 2a02:8108:0:60::2bf
315581 Wed Jun 4 08:36:03 2025 daemon.info ipsec: 14[CFG] <FRITZBox|10897> configured proposals: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/AES_CTR_128/AES_CTR_192/AES_CTR_256/3DES_CBC/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/AES_XCBC_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/CURVE_448/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048, IKE:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/AES_CCM_16_128/AES_CCM_16_192/AES_CCM_16_256/CHACHA20_POLY1305/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/AES_CCM_12_128/AES_CCM_12_192/AES_CCM_12_256/AES_CCM_8_128/AES_CCM_8_192/AES_CCM_8_256/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/CURVE_448/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048
315582 Wed Jun 4 08:36:03 2025 daemon.info ipsec: 14[CFG] <FRITZBox|10897> sending supported signature hash algorithms: sha256 sha384 sha512 identity
315583 Wed Jun 4 08:36:03 2025 daemon.info ipsec: 14[ENC] <FRITZBox|10897> generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ]
315584 Wed Jun 4 08:36:03 2025 daemon.info ipsec: 14[NET] <FRITZBox|10897> sending packet: from 2a02:3031:212:9444:b16b:6dda:13c8:e8ee[500] to 2a02:8108:0:60::2bf[500] (1112 bytes)
315585 Wed Jun 4 08:36:04 2025 daemon.info ipsec: 15[NET] <FRITZBox|10897> received packet: from 2a02:8108:0:60::2bf[500] to 2a02:3031:212:9444:b16b:6dda:13c8:e8ee[500] (432 bytes)
315586 Wed Jun 4 08:36:04 2025 daemon.info ipsec: 15[ENC] <FRITZBox|10897> parsed IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) ]
315587 Wed Jun 4 08:36:04 2025 daemon.info ipsec: 15[CFG] <FRITZBox|10897> selecting proposal:
315588 Wed Jun 4 08:36:04 2025 daemon.info ipsec: 15[CFG] <FRITZBox|10897> no acceptable ENCRYPTION_ALGORITHM found
315589 Wed Jun 4 08:36:04 2025 daemon.info ipsec: 15[CFG] <FRITZBox|10897> selecting proposal:
315590 Wed Jun 4 08:36:04 2025 daemon.info ipsec: 15[CFG] <FRITZBox|10897> proposal matches
315591 Wed Jun 4 08:36:04 2025 daemon.info ipsec: 15[CFG] <FRITZBox|10897> received proposals: IKE:AES_CBC_256/HMAC_SHA2_512_256/PRF_HMAC_SHA2_512/MODP_2048
315592 Wed Jun 4 08:36:04 2025 daemon.info ipsec: 15[CFG] <FRITZBox|10897> configured proposals: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/AES_CTR_128/AES_CTR_192/AES_CTR_256/3DES_CBC/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/AES_XCBC_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/CURVE_448/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048, IKE:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/AES_CCM_16_128/AES_CCM_16_192/AES_CCM_16_256/CHACHA20_POLY1305/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/AES_CCM_12_128/AES_CCM_12_192/AES_CCM_12_256/AES_CCM_8_128/AES_CCM_8_192/AES_CCM_8_256/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/CURVE_448/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048
315593 Wed Jun 4 08:36:04 2025 daemon.info ipsec: 15[CFG] <FRITZBox|10897> selected proposal: IKE:AES_CBC_256/HMAC_SHA2_512_256/PRF_HMAC_SHA2_512/MODP_2048
315594 Wed Jun 4 08:36:04 2025 daemon.info ipsec: 15[IKE] <FRITZBox|10897> authentication of ‘FQDN’ (myself) with pre-shared key
315595 Wed Jun 4 08:36:04 2025 daemon.info ipsec: 15[CFG] <FRITZBox|10897> proposing traffic selectors for us:
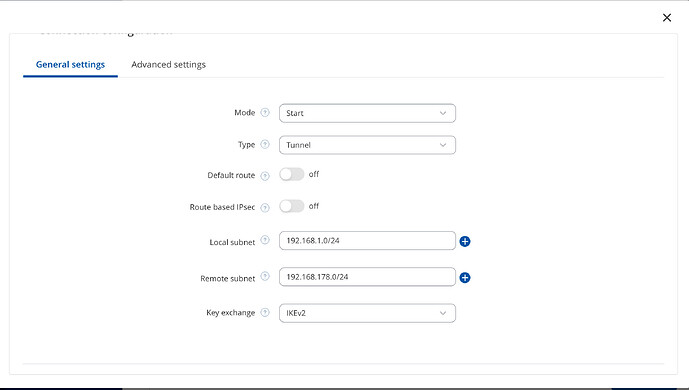
315596 Wed Jun 4 08:36:04 2025 daemon.info ipsec: 15[CFG] <FRITZBox|10897> 192.168.1.0/24
315597 Wed Jun 4 08:36:04 2025 daemon.info ipsec: 15[CFG] <FRITZBox|10897> proposing traffic selectors for other:
315598 Wed Jun 4 08:36:04 2025 daemon.info ipsec: 15[CFG] <FRITZBox|10897> 192.168.178.0/24
315599 Wed Jun 4 08:36:04 2025 daemon.info ipsec: 15[CFG] <FRITZBox|10897> configured proposals: ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_128/AES_CBC_192/AES_CBC_256/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/AES_XCBC_96/NO_EXT_SEQ, ESP:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/NO_EXT_SEQ
315600 Wed Jun 4 08:36:04 2025 daemon.info ipsec: 15[IKE] <FRITZBox|10897> establishing CHILD_SA FRITZBox_c{10919}
315601 Wed Jun 4 08:36:04 2025 daemon.info ipsec: 15[ENC] <FRITZBox|10897> generating IKE_AUTH request 1 [ IDi N(INIT_CONTACT) IDr AUTH SA TSi TSr N(MOBIKE_SUP) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_6_ADDR) N(ADD_6_ADDR) N(EAP_ONLY) N(MSG_ID_SYN_SUP) ]
315602 Wed Jun 4 08:36:04 2025 daemon.info ipsec: 15[NET] <FRITZBox|10897> sending packet: from 2a02:3031:212:9444:b16b:6dda:13c8:e8ee[4500] to 2a02:8108:0:60::2bf[4500] (528 bytes)
315603 Wed Jun 4 08:36:04 2025 daemon.info ipsec: 07[NET] <FRITZBox|10897> received packet: from 2a02:8108:0:60::2bf[4500] to 2a02:3031:212:9444:b16b:6dda:13c8:e8ee[4500] (96 bytes)
315604 Wed Jun 4 08:36:04 2025 daemon.info ipsec: 07[ENC] <FRITZBox|10897> parsed IKE_AUTH response 1 [ N(AUTH_FAILED) ]
315605 Wed Jun 4 08:36:04 2025 daemon.info ipsec: 07[IKE] <FRITZBox|10897> received AUTHENTICATION_FAILED notify error
315606 Wed Jun 4 08:36:33 2025 daemon.info ipsec: 14[IKE] <FRITZBox|10898> initiating IKE_SA FRITZBox[10898] to 2a02:8108:0:60::2bf
315607 Wed Jun 4 08:36:33 2025 daemon.info ipsec: 14[CFG] <FRITZBox|10898> configured proposals: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/AES_CTR_128/AES_CTR_192/AES_CTR_256/3DES_CBC/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/AES_XCBC_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/CURVE_448/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048, IKE:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/AES_CCM_16_128/AES_CCM_16_192/AES_CCM_16_256/CHACHA20_POLY1305/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/AES_CCM_12_128/AES_CCM_12_192/AES_CCM_12_256/AES_CCM_8_128/AES_CCM_8_192/AES_CCM_8_256/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/CURVE_448/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048
315608 Wed Jun 4 08:36:33 2025 daemon.info ipsec: 14[CFG] <FRITZBox|10898> sending supported signature hash algorithms: sha256 sha384 sha512 identity
315609 Wed Jun 4 08:36:33 2025 daemon.info ipsec: 14[ENC] <FRITZBox|10898> generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ]
315610 Wed Jun 4 08:36:33 2025 daemon.info ipsec: 14[NET] <FRITZBox|10898> sending packet: from 2a02:3031:212:9444:b16b:6dda:13c8:e8ee[500] to 2a02:8108:0:60::2bf[500] (1112 bytes)
315611 Wed Jun 4 08:36:34 2025 daemon.info ipsec: 15[NET] <FRITZBox|10898> received packet: from 2a02:8108:0:60::2bf[500] to 2a02:3031:212:9444:b16b:6dda:13c8:e8ee[500] (432 bytes)
315612 Wed Jun 4 08:36:34 2025 daemon.info ipsec: 15[ENC] <FRITZBox|10898> parsed IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) ]
315613 Wed Jun 4 08:36:34 2025 daemon.info ipsec: 15[CFG] <FRITZBox|10898> selecting proposal:
315614 Wed Jun 4 08:36:34 2025 daemon.info ipsec: 15[CFG] <FRITZBox|10898> no acceptable ENCRYPTION_ALGORITHM found
315615 Wed Jun 4 08:36:34 2025 daemon.info ipsec: 15[CFG] <FRITZBox|10898> selecting proposal:
315616 Wed Jun 4 08:36:34 2025 daemon.info ipsec: 15[CFG] <FRITZBox|10898> proposal matches
315617 Wed Jun 4 08:36:34 2025 daemon.info ipsec: 15[CFG] <FRITZBox|10898> received proposals: IKE:AES_CBC_256/HMAC_SHA2_512_256/PRF_HMAC_SHA2_512/MODP_2048
315618 Wed Jun 4 08:36:34 2025 daemon.info ipsec: 15[CFG] <FRITZBox|10898> configured proposals: IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/AES_CTR_128/AES_CTR_192/AES_CTR_256/3DES_CBC/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/AES_XCBC_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/CURVE_448/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048,
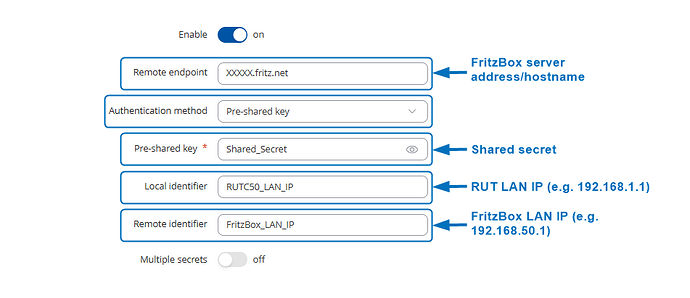
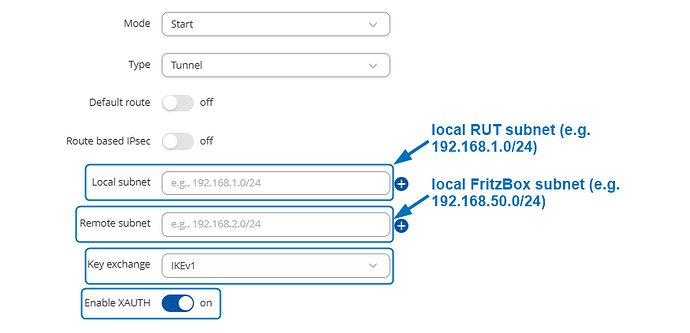
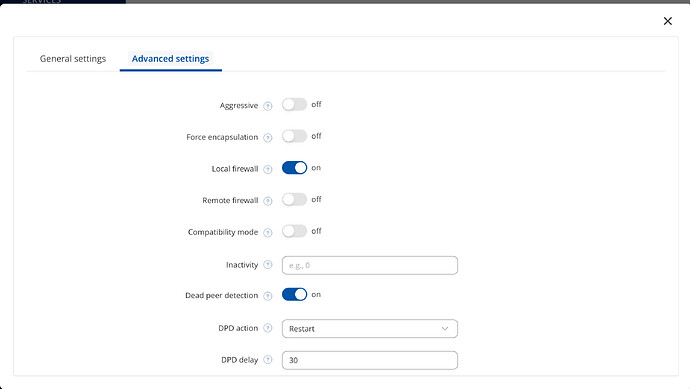
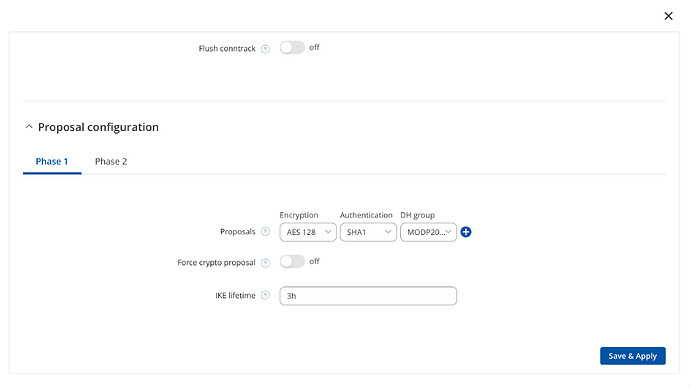
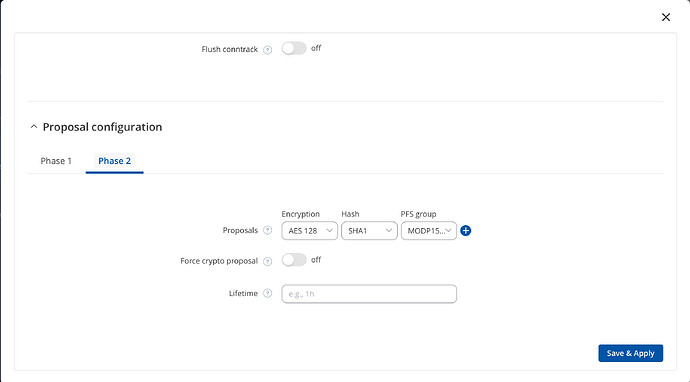
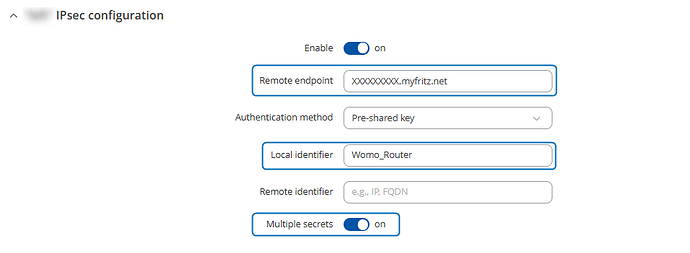
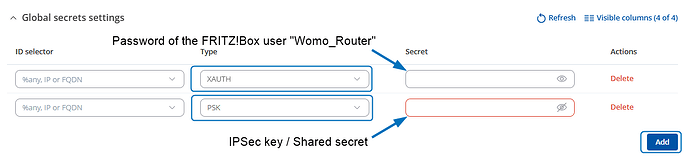
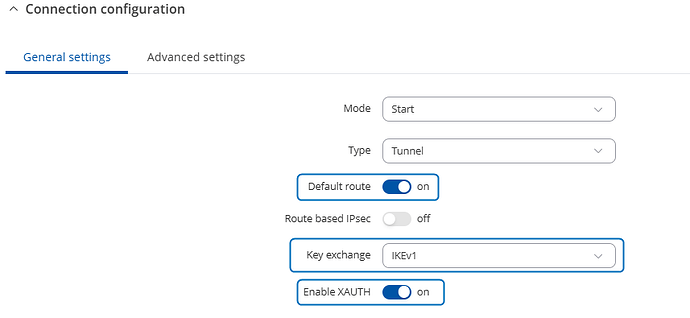
Below the IPsec settings from the Rutc50