Hello Everyone, I recently started at a new company and have been assigned the task of creating a VPN network using a Router that has the latest version of pfSense installed and multiple Teltonika RUT241 Routers. The idea is for these Routers to later have cameras connected to their LAN.
I have created in OpenVPN the P2P-TLS server on the PfSense Router and have used various tutorials to properly configure it.
Then I export the certificates and the key to the RUT241 and fill in the rest of the fields required for the OpenVPN Client.
For a brief moment, it appears connected and then disconnects, never to reconnect again. There was a time when I was able to connect for a long period, and I verified that both Routers could ping each other, but they could not see the devices connected to them.
If someone would be so kind as to advise me, I would be very grateful.
Kind regards!
Hello,
I assume the connection is working now, but the issue is with LAN to LAN communication. Is that correct?
If so, the configurations will depends on your requirements.
On the client (RUT), if you want to reach servers LAN, you need to add a route to server’s LAN in push options (available via WebUI). For example, if the server’s LAN is 192.168.5.0/24:
route 192.168.5.0 255.255.255.0
If you need to reach clients (RUT) LAN from the server, you need to associate the RUT’s LAN network with this specific TLS client. For this, on the server you need to add a TLS client (RUT) with a cert name to the ccd directory and define a route to this client (iroute). Please, take a look a these posts here and here.
You can find more information about OpenVPN here.
Kind Regards,
Hi Andzej,
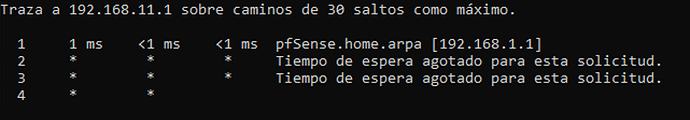
first of all thank you very much for your answer, I have managed to establish the tunnel connection, but the problem of reaching the clients (RUT) persists, I have checked the configuration of the clients as you indicated in your answer. However, I can’t ping the computers connected to the clients, but I can ping the other way round, i.e. from client to server, there is no problem.
Can you think what could be happening?
Thank you very much in advance.
dev ovpns3
verb 1
dev-type tun
dev-node /dev/tun3
writepid /var/run/openvpn_server3.pid
#user nobody
#group nobody
script-security 3
daemon
keepalive 10 60
ping-timer-rem
persist-tun
persist-key
proto udp4
auth SHA256
up /usr/local/sbin/ovpn-linkup
down /usr/local/sbin/ovpn-linkdown
local XXXXXXXXX
tls-server
server 192.168.199.0 255.255.255.0
client-config-dir /var/etc/openvpn/server3/csc
ifconfig 192.168.199.1 192.168.199.2
tls-verify “/usr/local/sbin/ovpn_auth_verify tls ‘OL_TLS_SRV’ 1”
lport 1194
management /var/etc/openvpn/server3/sock unix
push “route 192.168.1.0 255.255.255.0”
remote-cert-tls client
route 192.168.11.0 255.255.255.0
route 192.168.22.0 255.255.255.0
capath /var/etc/openvpn/server3/ca
cert /var/etc/openvpn/server3/cert
key /var/etc/openvpn/server3/key
dh /etc/dh-parameters.2048
tls-auth /var/etc/openvpn/server3/tls-auth 0
data-ciphers AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305:AES-256-CBC
data-ciphers-fallback AES-256-CBC
allow-compression no
persist-remote-ip
float
topology subnet
explicit-exit-notify 1
inactive 300
@Ene Hi,
Please, take a look at this article here for pfSense. Specifically, the following sections:
- Configuring SSL/TLS Server Side
- Configure the OpenVPN Server Instance
- Create Client-Specific Overrides
Make sure that you have configured TLS client for RUT on pfSense and added a route to it.
Kind Regards,
Hi Andzej,
I have carefully followed all the steps in the tutorial you sent me.
It still doesn’t work, so it occurs to me that it could be 2 things,
Either pfSense(v 2.7.2) doesn’t know how to redirect the traffic through the tunnel.
Or Teltonika has some traffic route in the firewall that doesn’t let the packets get through.
Another thing that might be relevant is that if I set up a tunnel through SharedKey it works perfectly in both directions. And it is only when I try to do it in STL that it stops working (at least in server → client direction).
Server side:
Client Side
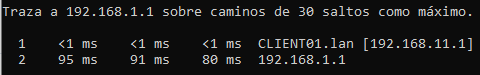
Thank you in advance
Hello @Ene,
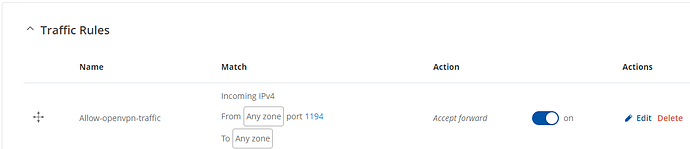
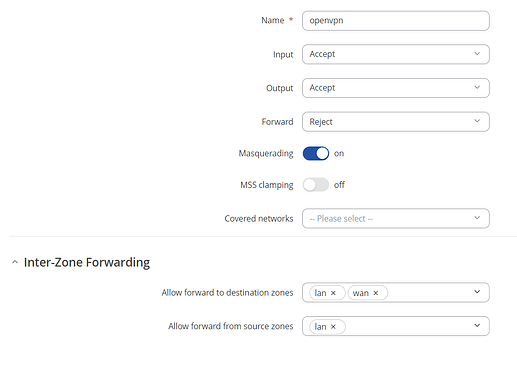
You can check if OpenVPN traffic is allowed to RUT LAN in Network → Firewall. Edit OpenVPN zone and check if forwarding from and to LAN is allowed.
However, since:
This would likely mean that there’s an issue on PfSense side with TLS and routes. If it would be a firewall issue, then the static key configuration would fail as well.
Did you enter CN of RUT correctly? Can you show how you added TLS clients and routes?
Kind Regards,
that has been the solution, I never really believed how important it was that both the server and the client side had the same name.
thank you very much for your help. you hit the nail on the head!
This topic was automatically closed after 15 days. New replies are no longer allowed.