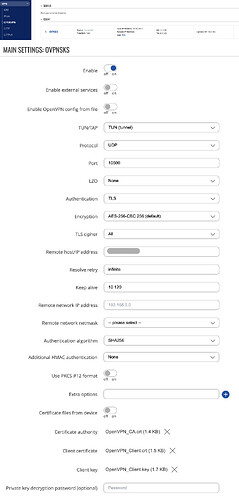
Hello,
I just did a factory reset of my TRB500 router and reconfigured my OpenVPN TUN site-to-site connection. The tunnel is up. Already, I can ping the TRB500 (which is an OpenVPN client) from the server (pfSense) and also from TRB500 to pfSense on their IP addresses used for the tunnel, but impossible to ping the LAN address (192.168.2.1) of the TRB500 from the server (pfSense).
It’s seems, the TRB500 does not forward packets coming from the tunnel to the LAN (or the firewall is blocking something?).
I installed tcpdump (please see bellow) and we see that ping on the tunnel IP address works, but we don’t see any ping request when I tried to ping to “192.168.2.1”.
However, on the server side (pfSense), in my routing table, I have a route 192.168.2.0/24 which sends to the tunnel gateway (10.90.200.2) (and conversely in the TRB500 I have a route from back).
What else can I try?
Thanks for your help
____ _ ___ ____
| _ \ _ _| |_ / _ \/ ___|
| |_) | | | | __| | | \___ \
| _ <| |_| | |_| |_| |___) |
|_| \_\\__,_|\__|\___/|____/
---------------------------------
Teltonika TRB5 series 2023
---------------------------------
Device: TRB500
Kernel: 4.14.319
Firmware: TRB5_R_00.07.05
Build: fbfe39de21
Build date: 2023-10-05 10:07:09
---------------------------------
root@TRB500:~# opkg update
Downloading https://downloads.openwrt.org/releases/21.02.0/targets/sdxprairie/generic/packages/Packages.gz
*** Failed to download the package list from https://downloads.openwrt.org/releases/21.02.0/targets/sdxprairie/generic/packages/Packages.gz
Downloading https://downloads.openwrt.org/releases/21.02.0/packages/arm_cortex-a7_neon-vfpv4/base/Packages.gz
Updated list of available packages in /var/opkg-lists/openwrt_base
Downloading https://downloads.openwrt.org/releases/21.02.0/packages/arm_cortex-a7_neon-vfpv4/base/Packages.sig
Signature check passed.
Downloading https://downloads.openwrt.org/releases/21.02.0/packages/arm_cortex-a7_neon-vfpv4/luci/Packages.gz
Updated list of available packages in /var/opkg-lists/openwrt_luci
Downloading https://downloads.openwrt.org/releases/21.02.0/packages/arm_cortex-a7_neon-vfpv4/luci/Packages.sig
Signature check passed.
Downloading https://downloads.openwrt.org/releases/21.02.0/packages/arm_cortex-a7_neon-vfpv4/packages/Packages.gz
Updated list of available packages in /var/opkg-lists/openwrt_packages
Downloading https://downloads.openwrt.org/releases/21.02.0/packages/arm_cortex-a7_neon-vfpv4/packages/Packages.sig
Signature check passed.
Downloading https://downloads.openwrt.org/releases/21.02.0/packages/arm_cortex-a7_neon-vfpv4/routing/Packages.gz
Updated list of available packages in /var/opkg-lists/openwrt_routing
Downloading https://downloads.openwrt.org/releases/21.02.0/packages/arm_cortex-a7_neon-vfpv4/routing/Packages.sig
Signature check passed.
Downloading https://downloads.openwrt.org/releases/21.02.0/packages/arm_cortex-a7_neon-vfpv4/telephony/Packages.gz
Updated list of available packages in /var/opkg-lists/openwrt_telephony
Downloading https://downloads.openwrt.org/releases/21.02.0/packages/arm_cortex-a7_neon-vfpv4/telephony/Packages.sig
Signature check passed.
Downloading https://downloads.openwrt.org/releases/21.02.0/packages/arm_cortex-a7_neon-vfpv4/vuci/Packages.gz
*** Failed to download the package list from https://downloads.openwrt.org/releases/21.02.0/packages/arm_cortex-a7_neon-vfpv4/vuci/Packages.gz
Downloading http://opkg.teltonika-networks.com/1cea26e83f9e63789112c95393d0586301318cd1dc122cde40715025f69abfb9/Packages.gz
Updated list of available packages in /var/opkg-lists/tlt_packages
Downloading http://opkg.teltonika-networks.com/1cea26e83f9e63789112c95393d0586301318cd1dc122cde40715025f69abfb9/Packages.sig
Signature check passed.
Collected errors:
* opkg_download: Failed to download https://downloads.openwrt.org/releases/21.02.0/targets/sdxprairie/generic/packages/Packages.gz, wget returned 8.
* opkg_download: Failed to download https://downloads.openwrt.org/releases/21.02.0/packages/arm_cortex-a7_neon-vfpv4/vuci/Packages.gz, wget returned 8.
root@TRB500:~# opkg install tcpdump
Installing tcpdump (4.99.4-1) to root...
Downloading http://opkg.teltonika-networks.com/1cea26e83f9e63789112c95393d0586301318cd1dc122cde40715025f69abfb9/tcpdump_4.99.4-1_arm_cortex-a7_neon-vfpv4.ipk
Configuring tcpdump.
root@TRB500:~#
root@TRB500:~# ifconfig
br-lan Link encap:Ethernet HWaddr 20:97:27:08:2F:7E
inet addr:192.168.2.1 Bcast:192.168.2.255 Mask:255.255.255.0
inet6 addr: fe80::2297:27ff:fe08:2f7e/64 Scope:Link
inet6 addr: fd49:97fb:78bd::1/60 Scope:Global
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:11492 errors:0 dropped:0 overruns:0 frame:0
TX packets:9692 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:1193053 (1.1 MiB) TX bytes:7458185 (7.1 MiB)
ecm0 Link encap:Ethernet HWaddr 20:97:27:08:2F:7F
UP BROADCAST MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
eth0 Link encap:Ethernet HWaddr 20:97:27:08:2F:7E
inet addr:169.254.4.1 Bcast:169.254.255.255 Mask:255.255.0.0
inet6 addr: fe80::2297:27ff:fe08:2f7e/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:11492 errors:0 dropped:0 overruns:0 frame:0
TX packets:9672 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:3497923809 (3.2 GiB) TX bytes:7455916 (7.1 MiB)
Interrupt:41
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:462 errors:0 dropped:0 overruns:0 frame:0
TX packets:462 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:39842 (38.9 KiB) TX bytes:39842 (38.9 KiB)
rmnet_data0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:100.119.158.252 Mask:255.255.255.255
inet6 addr: fe80::dd37:57ac:9bd1:a534/64 Scope:Link
UP RUNNING MTU:1500 Metric:1
RX packets:1231 errors:0 dropped:0 overruns:0 frame:0
TX packets:878 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:1309358 (1.2 MiB) TX bytes:91094 (88.9 KiB)
rmnet_ipa0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet6 addr: fe80::244d:b113:85eb:56c2/64 Scope:Link
UP RUNNING MTU:9216 Metric:1
RX packets:505 errors:0 dropped:0 overruns:0 frame:0
TX packets:878 errors:0 dropped:13 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:1319206 (1.2 MiB) TX bytes:98118 (95.8 KiB)
tun_c_OVPNSKS Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:10.90.200.2 P-t-P:10.90.200.2 Mask:255.255.255.0
inet6 addr: fe80::d641:c8d6:3a37:f177/64 Scope:Link
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1500 Metric:1
RX packets:6 errors:0 dropped:0 overruns:0 frame:0
TX packets:10 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:500
RX bytes:504 (504.0 B) TX bytes:808 (808.0 B)
root@TRB500:~# tcpdump -i tun_c_OVPNSKS icmp
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on tun_c_OVPNSKS, link-type RAW (Raw IP), snapshot length 262144 bytes
13:37:42.380191 IP 10.90.200.1 > 10.90.200.2: ICMP echo request, id 1341, seq 0, length 64
13:37:42.380429 IP 10.90.200.2 > 10.90.200.1: ICMP echo reply, id 1341, seq 0, length 64
13:37:42.957589 IP 10.90.200.1 > 10.90.200.2: ICMP echo request, id 1341, seq 1, length 64
13:37:42.957699 IP 10.90.200.2 > 10.90.200.1: ICMP echo reply, id 1341, seq 1, length 64
13:37:43.980880 IP 10.90.200.1 > 10.90.200.2: ICMP echo request, id 1341, seq 2, length 64
13:37:43.981003 IP 10.90.200.2 > 10.90.200.1: ICMP echo reply, id 1341, seq 2, length 64
6 packets captured
6 packets received by filter
0 packets dropped by kernel