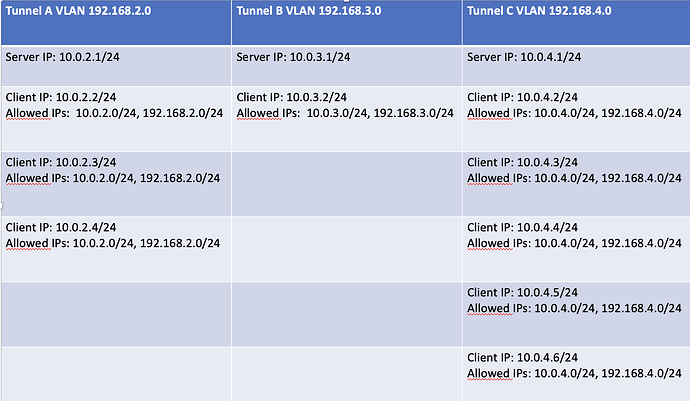
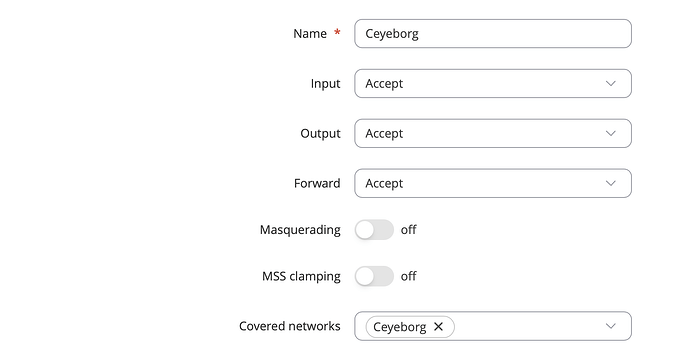
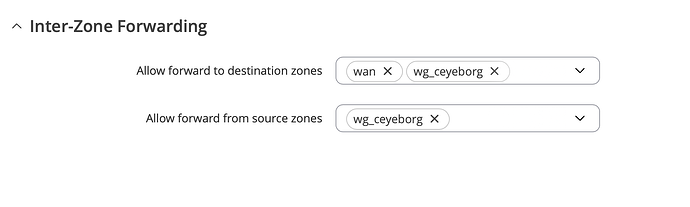
tcpdump: data link type LINUX_SLL2
tcpdump: listening on any, link-type LINUX_SLL2 (Linux cooked v2), snapshot length 262144 bytes
18:29:13.187971 eth0 In IP15 (invalid)
18:29:13.187971 eth0.5 In IP (tos 0x0, ttl 64, id 15470, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.4.4 > 192.168.179.36: ICMP echo request, id 6, seq 1011, length 64
18:29:13.188086 Ceyb2wg Out IP (tos 0x0, ttl 63, id 15470, offset 0, flags [DF], proto ICMP (1), length 84)
10.0.4.1 > 192.168.179.36: ICMP echo request, id 6, seq 1011, length 64
18:29:13.248088 qmimux0 Out IP (tos 0x0, ttl 60, id 36501, offset 0, flags [DF], proto ICMP (1), length 84)
10.152.81.132 > 1.1.1.1: ICMP echo request, id 5586, seq 0, length 64
18:29:13.311059 qmimux0 In IP (tos 0x0, ttl 54, id 54896, offset 0, flags [none], proto ICMP (1), length 84)
1.1.1.1 > 10.152.81.132: ICMP echo reply, id 5586, seq 0, length 64
18:29:13.334453 eth0 In IP7 (invalid)
18:29:13.334453 eth0.3 In IP (tos 0x0, ttl 64, id 439, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.2.2 > 192.168.2.1: ICMP echo request, id 46167, seq 0, length 64
18:29:13.334808 eth0.3 Out IP (tos 0x0, ttl 64, id 17109, offset 0, flags [none], proto ICMP (1), length 84)
192.168.2.1 > 192.168.2.2: ICMP echo reply, id 46167, seq 0, length 64
18:29:13.334837 eth0 Out IP10 (invalid)
18:29:14.212478 eth0 In IP15 (invalid)
18:29:14.212478 eth0.5 In IP (tos 0x0, ttl 64, id 15550, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.4.4 > 192.168.179.36: ICMP echo request, id 6, seq 1012, length 64
18:29:14.212607 Ceyb2wg Out IP (tos 0x0, ttl 63, id 15550, offset 0, flags [DF], proto ICMP (1), length 84)
10.0.4.1 > 192.168.179.36: ICMP echo request, id 6, seq 1012, length 64
18:29:14.448143 eth0 In IP1 (invalid)
18:29:14.448143 eth0.3 In IP (tos 0x0, ttl 64, id 40663, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.2.3 > 192.168.2.1: ICMP echo request, id 59413, seq 0, length 64
18:29:14.448411 eth0.3 Out IP (tos 0x0, ttl 64, id 29103, offset 0, flags [none], proto ICMP (1), length 84)
192.168.2.1 > 192.168.2.3: ICMP echo reply, id 59413, seq 0, length 64
18:29:14.448429 eth0 Out IP10 (invalid)
18:29:15.150834 eth0 In IP9 (invalid)
18:29:15.150834 eth0.3 In IP (tos 0x0, ttl 64, id 13269, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.2.4 > 192.168.2.1: ICMP echo request, id 32366, seq 0, length 64
18:29:15.151121 eth0.3 Out IP (tos 0x0, ttl 64, id 34987, offset 0, flags [none], proto ICMP (1), length 84)
192.168.2.1 > 192.168.2.4: ICMP echo reply, id 32366, seq 0, length 64
18:29:15.151140 eth0 Out IP10 (invalid)
18:29:15.235981 eth0 In IP15 (invalid)
18:29:15.235981 eth0.5 In IP (tos 0x0, ttl 64, id 15554, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.4.4 > 192.168.179.36: ICMP echo request, id 6, seq 1013, length 64
18:29:15.236120 Ceyb2wg Out IP (tos 0x0, ttl 63, id 15554, offset 0, flags [DF], proto ICMP (1), length 84)
10.0.4.1 > 192.168.179.36: ICMP echo request, id 6, seq 1013, length 64
18:29:15.936063 pppoe-wan Out IP (tos 0x0, ttl 60, id 29957, offset 0, flags [DF], proto ICMP (1), length 84)
84.131.58.225 > 1.1.1.1: ICMP echo request, id 5591, seq 0, length 64
18:29:15.945795 pppoe-wan In IP (tos 0x0, ttl 60, id 15365, offset 0, flags [none], proto ICMP (1), length 84)
1.1.1.1 > 84.131.58.225: ICMP echo reply, id 5591, seq 0, length 64
18:29:16.260081 eth0 In IP15 (invalid)
18:29:16.260081 eth0.5 In IP (tos 0x0, ttl 64, id 15769, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.4.4 > 192.168.179.36: ICMP echo request, id 6, seq 1014, length 64
18:29:16.260252 Ceyb2wg Out IP (tos 0x0, ttl 63, id 15769, offset 0, flags [DF], proto ICMP (1), length 84)
10.0.4.1 > 192.168.179.36: ICMP echo request, id 6, seq 1014, length 64
18:29:16.354061 qmimux0 Out IP (tos 0x0, ttl 60, id 36551, offset 0, flags [DF], proto ICMP (1), length 84)
10.152.81.132 > 1.1.1.1: ICMP echo request, id 5596, seq 0, length 64
18:29:16.411966 qmimux0 In IP (tos 0x0, ttl 54, id 39252, offset 0, flags [none], proto ICMP (1), length 84)
1.1.1.1 > 10.152.81.132: ICMP echo reply, id 5596, seq 0, length 64
18:29:17.055059 eth0 In IP8 (invalid)
18:29:17.055059 eth0.3 In IP (tos 0x0, ttl 64, id 38757, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.2.5 > 192.168.2.1: ICMP echo request, id 40726, seq 0, length 64
18:29:17.055290 eth0.3 Out IP (tos 0x0, ttl 64, id 26456, offset 0, flags [none], proto ICMP (1), length 84)
192.168.2.1 > 192.168.2.5: ICMP echo reply, id 40726, seq 0, length 64
18:29:17.055305 eth0 Out IP10 (invalid)
18:29:17.284063 eth0 In IP15 (invalid)
18:29:17.284063 eth0.5 In IP (tos 0x0, ttl 64, id 15811, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.4.4 > 192.168.179.36: ICMP echo request, id 6, seq 1015, length 64
18:29:17.284175 Ceyb2wg Out IP (tos 0x0, ttl 63, id 15811, offset 0, flags [DF], proto ICMP (1), length 84)
10.0.4.1 > 192.168.179.36: ICMP echo request, id 6, seq 1015, length 64
18:29:18.308061 eth0 In IP15 (invalid)
18:29:18.308061 eth0.5 In IP (tos 0x0, ttl 64, id 15924, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.4.4 > 192.168.179.36: ICMP echo request, id 6, seq 1016, length 64
18:29:18.308235 Ceyb2wg Out IP (tos 0x0, ttl 63, id 15924, offset 0, flags [DF], proto ICMP (1), length 84)
10.0.4.1 > 192.168.179.36: ICMP echo request, id 6, seq 1016, length 64
18:29:18.344571 eth0 In IP7 (invalid)
18:29:18.344571 eth0.3 In IP (tos 0x0, ttl 64, id 5323, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.2.2 > 192.168.2.1: ICMP echo request, id 16472, seq 0, length 64
18:29:18.344806 eth0.3 Out IP (tos 0x0, ttl 64, id 17162, offset 0, flags [none], proto ICMP (1), length 84)
192.168.2.1 > 192.168.2.2: ICMP echo reply, id 16472, seq 0, length 64
18:29:18.344820 eth0 Out IP10 (invalid)
^C
44 packets captured
47 packets received by filter
0 packets dropped by kernel