Hi all,
Second post here.
I’m trying to set up an OpenVPN server on a RUT956, version RUT9M_R_00.07.04.3
My goal is to have the router acting as a server and have Windows/iOS/Android/MAC connected as client to this server.
To simplify the configuration, I’m trying to use this option:
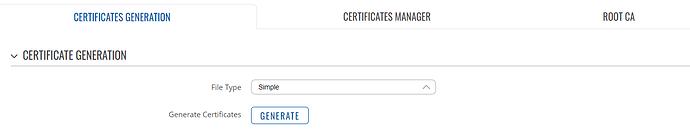
I thus used this, located here system/admin/certificates/generation
I managed to start the server side with basic configuration.
Furthermore, I managed to create the ovpn config file for the client, using the “simple” certificates / keys created on the server.
But I get this error :
2024-01-30 11:00:38 Certificate does not have key usage extension
2024-01-30 11:00:38 OpenSSL: error:0A000086:SSL routines::certificate verify failed:
2024-01-30 11:00:38 TLS_ERROR: BIO read tls_read_plaintext error
2024-01-30 11:00:38 TLS Error: TLS object → incoming plaintext read error
2024-01-30 11:00:38 TLS Error: TLS handshake failed
From my research, this seems to be related to the latest version of OpenVPN having tighter security.
I tried to find a solution, but after many hours of trying, I’m stuck.
I looked at many topics like those, but they do not apply exactly at what I’m trying to accomplish
https://wiki.teltonika-networks.com/view/OpenVPN_client_on_Windows
https://wiki.teltonika-networks.com/view/How_to_generate_TLS_certificates_(Windows)%3F
I reached the vendor, but to resolve an issue, I need to pay $200 !
From what I read, if you did not buy directly from Teltonika, you cannot get support ?
For now, I will be using the old PPTP, but it’s unsecure and not supported on latest Android.
Any pointers/help will be appreciated.
Is there a how-to article for my use case? I did not find any.
FYI, I was using an ASUS router where OpenVPN is super easy to enable, and the router provides the client file and it works. I switch to Teltonika, to try a more robust router, but unsure if I will keep this route!