Can anyone advise on the correct way to isolate the Vlans from the main Lan and other physical ports.
Any help would be greatly appreciated.
Regards Padraic.
Can anyone advise on the correct way to isolate the Vlans from the main Lan and other physical ports.
Any help would be greatly appreciated.
Regards Padraic.
Hello,
Thank you for your question.
Reason why you can’t isolate VLANS is that by default VLANS are created in the same zone as LAN network, that’s why you can reach them.
To solve it you will need to remove your VLANS from LAN zone, create your firewall zone for new VLANS on your device and reject forwarding, then you will not be able to ping different VLANS. Follow the article below to separate VLAN zones. After completing configuration restart firewall or devices, because new rules will not apply after changes.
In previous ticked I gave you configuration example for VLANS, follow steps from there.
Previous response: RUTX50 VLAN config - Teltonika Networks - Teltonika Community
Best regards,
Eimantas
Hi Eimantas, I have already implemented the first part in the guide attached. And I have achieved isolation between the vlans.
The next step I need help with is the following.
My 4 vlans are connected through physical port 4 to my switch. I want to prevent any access to my router gui/interface from any device on any of the vlans.
To connect and configure the router, I want to have to plug in to one of the other three physical ports.
So I want to isolate the vlans from the lan.
Regards Padraic.
Hi Padraic …
“… to prevent any access to my router gui/interface from any device on any of the vlans.”
This is how I did it … In NETWORK > FIREWALL > TRAFFIC RULES, create a new rule that looks like the following …
DO NOT add your default vlan1 (management vlan) into the source zone’s box … I’ve seen stranger things done after a few beers … mostly by me.
Cheers … Mike
Hi Mike, thanks for getting back to me.
The source zone field, is for the VLANs I want to deny access to the web ui and cli?
I’m not sure if I should restrict all vlans or leave the management vlan with access to the router?
Regards Padraic.
Hi Padraic,
“The source zone field, is for the VLANs I want to deny access to the web ui and cli?”
Correct. The way I have it, and the way I’d HIGHLY recommend, is that you retain access to the management interfaces on your management vlan (default VLAN1 - lan). If you don’t do this, then you’ll lose all access to the management interfaces and won’t be able to configure anything.
And another suggestion …
It is also possible to set up your forwardings, so that access is allowed to the isolated VLANs if initiated from the management VLAN but not the other way round i.e. default VLAN1 (lan) can access all VLANs but they can’t initiate access to eachother or the management VLAN. This you will find useful, providing you trust everything sitting on your management VLAN. Assuming that all your VLANs, including VLAN1 are currently isolated from eachother, the only change you need to make to effect the above, is in …
NETWORK > FIREWALL > GENERAL SETTINGS > ZONES > ZONE FORWARDS:lan (your mgmt VLAN1)
In the “Allow forward to destination zones”
This one change, will also add the correct corresponding entries in the “Allow forward from source zones” for the other VLANs - you’ll be able to see this in the WebUI.
Hi Mike, I don’t seem to have to option to add a new rule, Could you send me a screenshot?
Regards Padraic.
With Advanced Menu option enabled …
Then you’ll see the add functionality at the bottom.
Edit the settings I mentioned before, first deleting anthing in the Source zone that the rule creation may have automatically added - just to ensure a clean slate before we add our stuff.
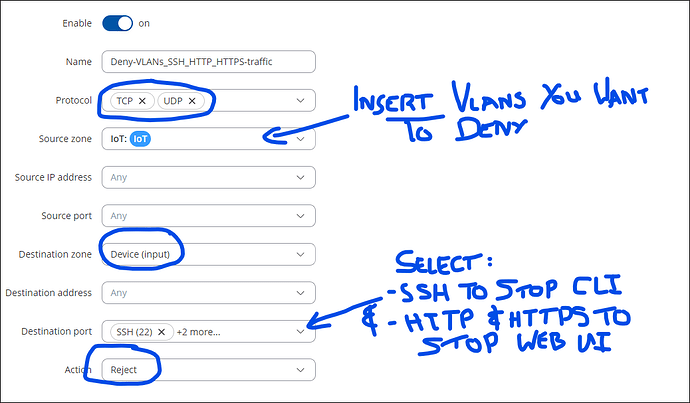
Let me know how you get on.
This topic was automatically closed after 15 days. New replies are no longer allowed.