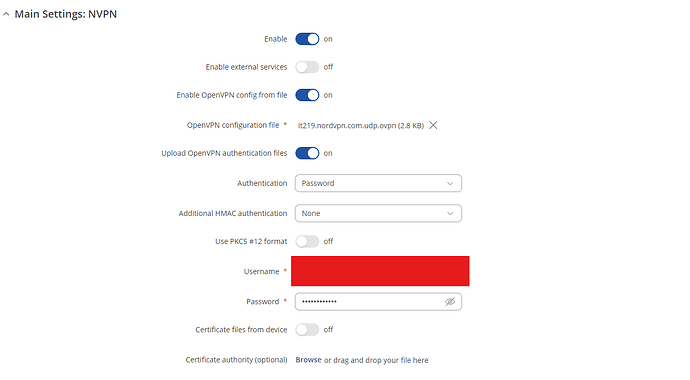
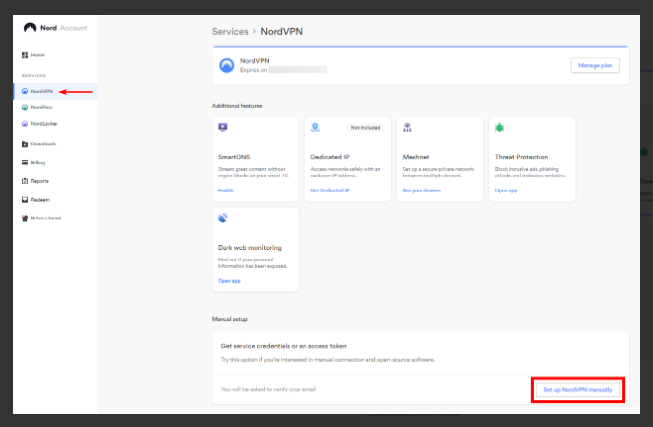
I cannot connect to the NordVPN server.
Donwloded the conf file from https://nordvpn.com/it/servers/tools/
Log:
Sat May 18 16:54:49 2024 daemon.warn openvpn(NVPN)[29368]: DEPRECATED OPTION: --cipher set to ‘AES-256-CBC’ but missing in --data-ciphers (AES-256-GCM:AES-128-GCM). Future OpenVPN version will ignore --cipher for cipher negotiations. Add ‘AES-256-CBC’ to --data-ciphers or change --cipher ‘AES-256-CBC’ to --data-ciphers-fallback ‘AES-256-CBC’ to silence this warning.
Sat May 18 16:54:49 2024 daemon.notice openvpn(NVPN)[29368]: OpenVPN 2.5.3 arm-openwrt-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD]
Sat May 18 16:54:49 2024 daemon.notice openvpn(NVPN)[29368]: library versions: OpenSSL 3.0.12 24 Oct 2023, LZO 2.10
Sat May 18 16:54:49 2024 daemon.warn openvpn(NVPN)[29368]: WARNING: --ping should normally be used with --ping-restart or --ping-exit
Sat May 18 16:54:49 2024 daemon.warn openvpn(NVPN)[29368]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Sat May 18 16:54:49 2024 daemon.notice openvpn(NVPN)[29368]: Outgoing Control Channel Authentication: Using 512 bit message hash ‘SHA512’ for HMAC authentication
Sat May 18 16:54:49 2024 daemon.notice openvpn(NVPN)[29368]: Incoming Control Channel Authentication: Using 512 bit message hash ‘SHA512’ for HMAC authentication
Sat May 18 16:54:49 2024 daemon.notice openvpn(NVPN)[29368]: TCP/UDP: Preserving recently used remote address: [AF_INET]82.102.21.123:1194
Sat May 18 16:54:49 2024 daemon.notice openvpn(NVPN)[29368]: Socket Buffers: R=[180224->180224] S=[180224->180224]
Sat May 18 16:54:49 2024 daemon.notice openvpn(NVPN)[29368]: UDP link local: (not bound)
Sat May 18 16:54:49 2024 daemon.notice openvpn(NVPN)[29368]: UDP link remote: [AF_INET]82.102.21.123:1194
Sat May 18 16:54:49 2024 daemon.notice openvpn(NVPN)[29368]: TLS: Initial packet from [AF_INET]82.102.21.123:1194, sid=5ee60684 67eb8f7f
Sat May 18 16:54:49 2024 daemon.notice openvpn(NVPN)[29368]: VERIFY OK: depth=2, C=PA, O=NordVPN, CN=NordVPN Root CA
Sat May 18 16:54:49 2024 daemon.notice openvpn(NVPN)[29368]: VERIFY OK: depth=1, O=NordVPN, CN=NordVPN CA9
Sat May 18 16:54:49 2024 daemon.notice openvpn(NVPN)[29368]: VERIFY KU OK
Sat May 18 16:54:49 2024 daemon.notice openvpn(NVPN)[29368]: Validating certificate extended key usage
Sat May 18 16:54:49 2024 daemon.notice openvpn(NVPN)[29368]: ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Sat May 18 16:54:49 2024 daemon.notice openvpn(NVPN)[29368]: VERIFY EKU OK
Sat May 18 16:54:49 2024 daemon.notice openvpn(NVPN)[29368]: VERIFY X509NAME OK: CN=it219.nordvpn.com
Sat May 18 16:54:49 2024 daemon.notice openvpn(NVPN)[29368]: VERIFY OK: depth=0, CN=it219.nordvpn.com
Sat May 18 16:54:50 2024 daemon.notice openvpn(NVPN)[29368]: Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 4096 bit RSA, signature: RSA-SHA512
Sat May 18 16:54:50 2024 daemon.notice openvpn(NVPN)[29368]: [it219.nordvpn.com] Peer Connection Initiated with [AF_INET]82.102.21.123:1194
Sat May 18 16:54:51 2024 daemon.notice openvpn(NVPN)[29368]: SENT CONTROL [it219.nordvpn.com]: ‘PUSH_REQUEST’ (status=1)
Sat May 18 16:54:51 2024 daemon.notice openvpn(NVPN)[29368]: AUTH: Received control message: AUTH_FAILED
Sat May 18 16:54:51 2024 daemon.notice openvpn(NVPN)[29368]: SIGTERM[soft,auth-failure] received, process exiting