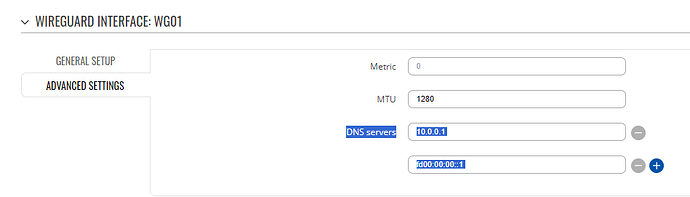
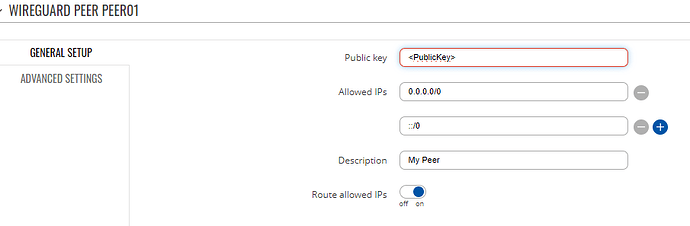
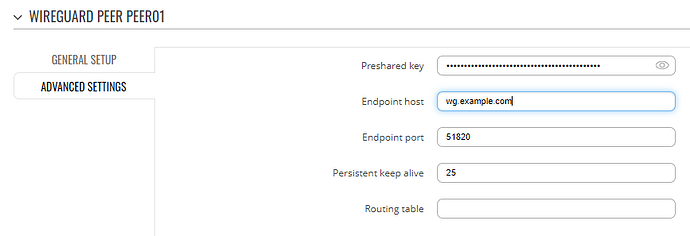
Will be setting up a fixed ip solution for testing this week. But i’m having a hard time seeing if this is the reason why i can’t get the teltonika modem to work the same way as my other wireguard peers. I have two mobile phones and two laptops, which i exported config-files for or generated the qr-codes for, and they work from the start. But with the teltonika i get one handshake, when i run “wg” on the teltonika CLI, but no response from the ubuntu server…
This is my current setup:
Ubuntu server:
Server
[Interface]
PrivateKey = SNmXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX=
Address = 10.8.0.1/24
ListenPort = 51820
PreUp =
PostUp = iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -o eth0 -j MASQUERADE; iptables -A INPUT -p udp -m udp --dport 51820 -j ACCEPT; iptables -A FORWARD -i wg0 -j ACCEPT; iptables -A FORWARD -o wg0 -j ACCEPT;
PreDown =
PostDown =
Client: rut955 (82f8d25d-7a7b-4c52-97ee-4292319d72c3)
[Peer]
PublicKey = cCVXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX=
PresharedKey = AiJXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX=
AllowedIPs = 10.8.0.2/32
AND The exported CONF-file for RUT955 looks like this:
The thing I’m curious about is which keys, i should put where in the teltonika modem setup
[Interface]
PrivateKey = sOSXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX=
Address = 10.8.0.2/24
DNS = 1.1.1.1
[Peer]
PublicKey = mGRXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX=
PresharedKey = AiJXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX=
AllowedIPs = 0.0.0.0/0, ::/0
PersistentKeepalive = 0
Endpoint = example.duckdns.org:51820
The thing I’m curious about, is the public/private key differences, i see one public key for the rut955 in the server setup, and another one in the exported configuration file (which i normally use with wg-quick if there is a laptop)
So in the tunnel config:
I currently have:
Private key: sOSXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX=
Public key: cCVXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX=
And for the peer i have:
Public key: mGRXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX=
Preshared key: AiJXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX=
Can you see any obvious errors i have made? Or could you maybe show some snippets of your setup, so I might grasp the concept easier…