Hi.
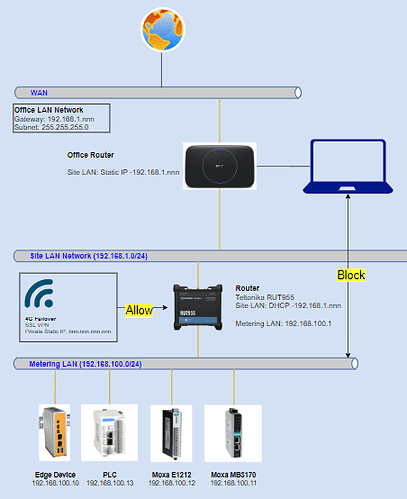
I have a setup where I am using a RUT955 device to create a small local network for an energy monitoring system, with the primary internet connection coming from an office router, connected via cable to the WAN port of the RUT955.
Alongside this, the RUT955 contains a SIM card that joins a private SSL VPN, with a fixed private IP address that I can use to remotely access the RUT955, and all devices on it’s LAN using Port Forwarding or PPTP.
As it is, the setup works well and I can remotely access my LAN devices on the RUT955 LAN via the Private IP of the SIM, due to the fact failover is set up.
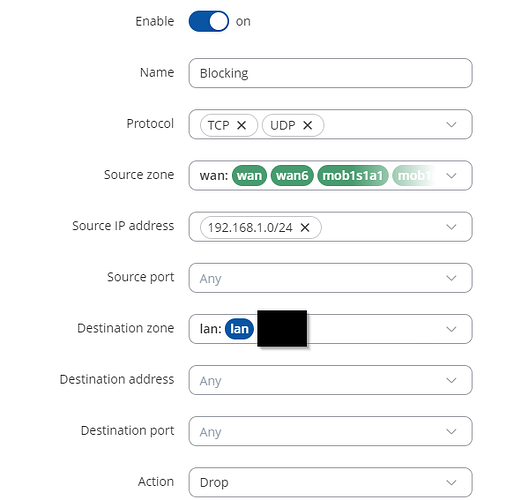
What I would like to do next is to block access to the RUT955 and all LAN devices on its LAN from the office LAN network such that no devices connected to the office Wi-Fi network are able to reach the RUT955 or any devices on it’s LAN via port forwarding, effectively making it invisible.
At the same time, I still want to be able to access and port forward via the mobile connection, which is working correctly now.
Currently I have not found a way to do this as the ‘wan’ zone contains ‘wan, mob1s1a1, and mobs2a2’ as a whole, meaning if I implement a firewall rule to block traffic from WAN to LAN, it also disallows any access via the mobile interfaces.
Is there a way I can set up different WAN zones, such that the wired WAN connection is a different firewall zone to the mobile connections?
I have included a diagram below outlining the network as it is, and the two main zones I want to block and allow traffic between.