jonjon
October 7, 2024, 1:57pm
1
HI Teltonika team,
I think you have another bug in the new firmware.
With the new firmware 7.6.13 and 7.6.16 my OpenVPN tunnels no longer work.
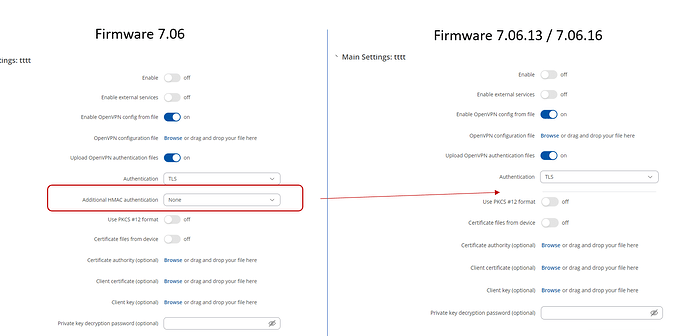
OpenVPN - Client:
It is therefore no longer possible to enter a key. ----> see image
After the firmware update the tunnel no longer worked.
Last Firmware that work ist 7.06
Can you check and fix the firmware.
Hi jonjon ,
Please make sure to revert to Advanced Mode to see additional settings in OpenVPN.
Let me know if this helps.
Regards,
jonjon
October 9, 2024, 10:05am
4
@ Janmiguel
sorry my mistakt but in Firmware 6.13 and 6.16 not work.
after firmware update i get the error:
Wed Oct 9 11:58:54 2024 daemon.warn openvpn(sfsff)[17315]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Wed Oct 9 11:58:54 2024 daemon.notice openvpn(sfsff)[17315]: SIGUSR1[soft,private-key-password-failure] received, process restarting
Wed Oct 9 11:58:54 2024 daemon.notice openvpn(sfsff)[17315]: Restart pause, 10 second(s)
if i create an new configuration and safe - i get the error:
Client key is encrypted, please enter decryption password
when i downgrade the firmware to 7.06 all works fine.
i use CA, Client-CA and Cline-Key, NO PASSWORD
i think you have an bug in the firmware.
Hi,
Can you try to generate new certificates and let me know if it works? I have a RUT955 here running on 7.16 FW and OpenVPN works as expected.
Regards,
jonjon
October 9, 2024, 1:26pm
6
@ Janmiguel
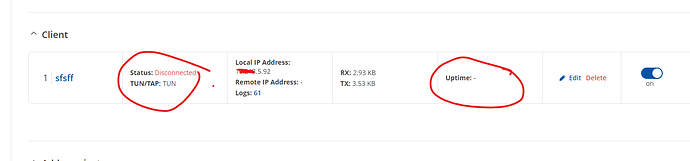
ok created all new but wont work:
the VPN start, but the state is disconnected, no uptime,
if i downgrade to 7.6 all works fine
Wed Oct 9 16:11:32 2024 daemon.warn openvpn(sfsff)[8293]: Multiple --down scripts defined. The previously configured script is overridden.
Wed Oct 9 16:11:32 2024 daemon.warn openvpn(sfsff)[8293]: Multiple --up scripts defined. The previously configured script is overridden.
Wed Oct 9 16:11:32 2024 daemon.notice openvpn(sfsff)[8293]: OpenVPN 2.5.3 mips-openwrt-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD]
Wed Oct 9 16:11:32 2024 daemon.notice openvpn(sfsff)[8293]: library versions: OpenSSL 3.0.12 24 Oct 2023, LZO 2.10
Wed Oct 9 16:11:32 2024 daemon.warn openvpn(sfsff)[8293]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Wed Oct 9 16:11:33 2024 daemon.notice openvpn(sfsff)[8293]: Outgoing Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key
Wed Oct 9 16:11:33 2024 daemon.notice openvpn(sfsff)[8293]: Outgoing Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication
Wed Oct 9 16:11:33 2024 daemon.notice openvpn(sfsff)[8293]: Incoming Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key
Wed Oct 9 16:11:33 2024 daemon.notice openvpn(sfsff)[8293]: Incoming Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication
Wed Oct 9 16:11:33 2024 daemon.notice openvpn(sfsff)[8293]: TCP/UDP: Preserving recently used remote address: [AF_INET]xxxxxxxxxxxxx
Wed Oct 9 16:11:33 2024 daemon.notice openvpn(sfsff)[8293]: Socket Buffers: R=[180224->180224] S=[180224->180224]
Wed Oct 9 16:11:33 2024 daemon.notice openvpn(sfsff)[8293]: UDP link local: (not bound)
Wed Oct 9 16:11:33 2024 daemon.notice openvpn(sfsff)[8293]: UDP link remote: [AF_INET]xxxxxxxxxxxxx
Wed Oct 9 16:11:33 2024 daemon.notice openvpn(sfsff)[8293]: TLS: Initial packet from [AF_INET]xxxxxxxxxxx, sid=5b03592a 0a32ff21
Wed Oct 9 16:11:33 2024 daemon.notice openvpn(sfsff)[8293]: VERIFY OK: depth=1, CN=xxxxxxxxxxxxxxxxxxxxx
Wed Oct 9 16:11:33 2024 daemon.notice openvpn(sfsff)[8293]: VERIFY KU OK
Wed Oct 9 16:11:33 2024 daemon.notice openvpn(sfsff)[8293]: Validating certificate extended key usage
Wed Oct 9 16:11:33 2024 daemon.notice openvpn(sfsff)[8293]: ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Wed Oct 9 16:11:33 2024 daemon.notice openvpn(sfsff)[8293]: VERIFY EKU OK
Wed Oct 9 16:11:33 2024 daemon.notice openvpn(sfsff)[8293]: VERIFY OK: depth=0, CN=xxxxxxxxxxx
Wed Oct 9 16:11:34 2024 daemon.notice openvpn(sfsff)[8293]: Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 384 bit EC, curve secp384r1, signature: ecdsa-with-SHA512
Wed Oct 9 16:11:34 2024 daemon.notice openvpn(sfsff)[8293]: [vpn-2024] Peer Connection Initiated with [AF_INET]xxxxxxxxxxxxxxxxxxxxx
Wed Oct 9 16:11:35 2024 daemon.notice openvpn(sfsff)[8293]: SENT CONTROL [vpn-2024]: 'PUSH_REQUEST' (status=1)
Wed Oct 9 16:11:35 2024 daemon.notice openvpn(sfsff)[8293]: PUSH: Received control message: 'PUSH_REPLY,route-gateway xxxxxxxxxx,topology subnet,ping 40,ping-restart 100,ifconfig xxxxxxxxxxx 255.255.0.0,peer-id 101,cipher AES-256-GCM'
Wed Oct 9 16:11:35 2024 daemon.notice openvpn(sfsff)[8293]: OPTIONS IMPORT: timers and/or timeouts modified
Wed Oct 9 16:11:35 2024 daemon.notice openvpn(sfsff)[8293]: OPTIONS IMPORT: --ifconfig/up options modified
Wed Oct 9 16:11:35 2024 daemon.notice openvpn(sfsff)[8293]: OPTIONS IMPORT: route-related options modified
Wed Oct 9 16:11:35 2024 daemon.notice openvpn(sfsff)[8293]: OPTIONS IMPORT: peer-id set
Wed Oct 9 16:11:35 2024 daemon.notice openvpn(sfsff)[8293]: OPTIONS IMPORT: adjusting link_mtu to 1624
Wed Oct 9 16:11:35 2024 daemon.notice openvpn(sfsff)[8293]: OPTIONS IMPORT: data channel crypto options modified
Wed Oct 9 16:11:35 2024 daemon.notice openvpn(sfsff)[8293]: Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Wed Oct 9 16:11:35 2024 daemon.notice openvpn(sfsff)[8293]: Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Wed Oct 9 16:11:35 2024 daemon.notice openvpn(sfsff)[8293]: TUN/TAP device tun_c_sfsff opened
Wed Oct 9 16:11:35 2024 daemon.notice openvpn(sfsff)[8293]: net_iface_mtu_set: mtu 1500 for tun_c_sfsff
Wed Oct 9 16:11:35 2024 daemon.notice openvpn(sfsff)[8293]: net_iface_up: set tun_c_sfsff up
Wed Oct 9 16:11:35 2024 daemon.notice openvpn(sfsff)[8293]: net_addr_v4_add: xxxxxxxxxx/16 dev tun_c_sfsff
Wed Oct 9 16:11:35 2024 daemon.notice openvpn(sfsff)[8293]: /etc/openvpn/updown.sh tun_c_sfsff 1500 1624 xxxxxxxxxxxx 255.255.0.0 init
Wed Oct 9 16:11:35 2024 daemon.notice openvpn(sfsff)[8293]: Initialization Sequence Completed
Wed Oct 9 16:14:30 2024 daemon.err openvpn(sfsff)[8293]: event_wait : Interrupted system call (code=4)
Wed Oct 9 16:14:30 2024 daemon.notice openvpn(sfsff)[8293]: Closing TUN/TAP interface
Hi, not sure if this is the issue here but a newer version of openvpn is more strict in certs. I’ve been bitten by that upgrading. Forgot the details but give it a try:
openvpn add to client config: tls-cipher “DEFAULT:@SECLEVEL=0”
possibly this will work? Then read in openvpn manuals what is the issue and repair, they have a reason to no longer support weaks certs.
system
October 22, 2024, 1:57pm
8
This topic was automatically closed after 15 days. New replies are no longer allowed.