I’ve upgrade my Rutx50 from version RUTX_R_00.07.04.5 to RUTX_R_00.07.05.3 but I can no longer see the VPN (IPSEC) configuration from the GUI.
The “ipsec status” command from CLI shows that the tunnels are still up/running. From a network point of view they are working correctly, so there is only a display issue in the GUI. The “uci show ipsec” shows all the correct information as well.
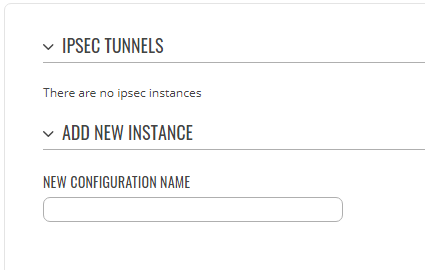
Here are the UCI settings from the running (upgraded) device:
ipsec.@ipsec[0]=ipsec
ipsec.@ipsec[0].rtinstall_enabled=‘1’
ipsec.@ipsec[0].make_before_break=‘0’
ipsec.CustomerX=remote
ipsec.CustomerX.crypto_proposal=‘CustomerX_ph1’
ipsec.CustomerX.enabled=‘1’
ipsec.CustomerX._multiple_secrets=‘0’
ipsec.CustomerX.force_crypto_proposal=‘1’
ipsec.CustomerX.gateway=‘vpnmgmt.CustomerX.nl’
ipsec.CustomerX.authentication_method=‘psk’
ipsec.CustomerX.pre_shared_key=‘xxxxxxxxxxxxxx’
ipsec.CustomerX.local_identifier=‘XXX-RTR01’
ipsec.CustomerX.remote_identifier=‘XXX-FW02’
ipsec.CustomerX.tunnel=‘CustomerX_c’
ipsec.CustomerX_c=connection
ipsec.CustomerX_c.crypto_proposal=‘CustomerX_ph2’
ipsec.CustomerX_c.defaultroute=‘0’
ipsec.CustomerX_c.aggressive=‘no’
ipsec.CustomerX_c.forceencaps=‘no’
ipsec.CustomerX_c.local_firewall=‘yes’
ipsec.CustomerX_c.remote_firewall=‘yes’
ipsec.CustomerX_c.comp_mode=‘1’
ipsec.CustomerX_c._dpd=‘1’
ipsec.CustomerX_c.force_crypto_proposal=‘1’
ipsec.CustomerX_c.mode=‘start’
ipsec.CustomerX_c.type=‘tunnel’
ipsec.CustomerX_c.lifetime=‘12h’
ipsec.CustomerX_c.ikelifetime=‘24h’
ipsec.CustomerX_c.local_subnet=‘10.101.128.0/25’ ‘10.100.128.254/32’
ipsec.CustomerX_c.remote_subnet=‘10.20.0.0/16’ ‘192.168.222.0/24’
ipsec.CustomerX_c.keyexchange=‘ikev2’
ipsec.CustomerX_c.dpdaction=‘restart’
ipsec.CustomerX_ph1=proposal
ipsec.CustomerX_ph1.encryption_algorithm=‘aes256’
ipsec.CustomerX_ph1.hash_algorithm=‘sha256’
ipsec.CustomerX_ph1.dh_group=‘modp2048’
ipsec.CustomerX_ph2=proposal
ipsec.CustomerX_ph2.encryption_algorithm=‘aes256’
ipsec.CustomerX_ph2.hash_algorithm=‘sha256’
ipsec.CustomerX_ph2.dh_group=‘modp2048’
Here are the UCI commands how the VPN was configured initially (the template we use):
uci set ipsec.@ipsec[0].rtinstall_enabled=1
uci set ipsec.CustomerX=remote
uci set ipsec.CustomerX.crypto_proposal=‘CustomerX_ph1’
uci set ipsec.CustomerX.enabled=‘1’
uci set ipsec.CustomerX._multiple_secrets=‘0’
uci set ipsec.CustomerX.force_crypto_proposal=‘1’
uci set ipsec.CustomerX.gateway=‘vpnmgmt.CustomerX.nl’
uci set ipsec.CustomerX.authentication_method=‘psk’
uci set ipsec.CustomerX.pre_shared_key=‘XXXXXXXXXXXX’
uci set ipsec.CustomerX.local_identifier=‘XXX-RTR01’
uci set ipsec.CustomerX.remote_identifier=‘XXX-FW02’
uci add_list ipsec.CustomerX.tunnel=‘CustomerX_c’
uci set ipsec.CustomerX_c=connection
uci set ipsec.CustomerX_c.crypto_proposal=‘CustomerX_ph2’
uci set ipsec.CustomerX_c.defaultroute=‘0’
uci set ipsec.CustomerX_c.aggressive=‘no’
uci set ipsec.CustomerX_c.forceencaps=‘no’
uci set ipsec.CustomerX_c.local_firewall=‘yes’
uci set ipsec.CustomerX_c.remote_firewall=‘yes’
uci set ipsec.CustomerX_c.comp_mode=‘1’
uci set ipsec.CustomerX_c._dpd=‘1’
uci set ipsec.CustomerX_c.force_crypto_proposal=‘1’
uci set ipsec.CustomerX_c.mode=‘start’
uci set ipsec.CustomerX_c.type=‘tunnel’
uci set ipsec.CustomerX_c.lifetime=‘12h’
uci set ipsec.CustomerX_c.ikelifetime=‘24h’
uci add_list ipsec.CustomerX_c.local_subnet=‘10.101.128.0/25’
uci add_list ipsec.CustomerX_c.local_subnet=‘10.100.128.254/32’
uci add_list ipsec.CustomerX_c.remote_subnet=‘10.20.0.0/16’
uci add_list ipsec.CustomerX_c.remote_subnet=‘192.168.222.0/24’
uci set ipsec.CustomerX_c.keyexchange=‘ikev2’
uci set ipsec.CustomerX_c.dpdaction=‘restart’
uci set ipsec.CustomerX_ph1=proposal
uci set ipsec.CustomerX_ph1.encryption_algorithm=‘aes256’
uci set ipsec.CustomerX_ph1.hash_algorithm=‘sha256’
uci set ipsec.CustomerX_ph1.dh_group=‘modp2048’
uci set ipsec.CustomerX_ph2=proposal
uci set ipsec.CustomerX_ph2.encryption_algorithm=‘aes256’
uci set ipsec.CustomerX_ph2.hash_algorithm=‘sha256’
uci set ipsec.CustomerX_ph2.dh_group='modp2048’h
I don’t know the prior firmware versions. But his configuration is used for years already, so we’ve seen quite a few.
My previous topic was closed, so I had to create a new one.