Hello Parsnip,
For some reason the IOT-lan still draws from the main lan IPv4 pool for addresses? Anyone aware of the configuration issue that I might have made?
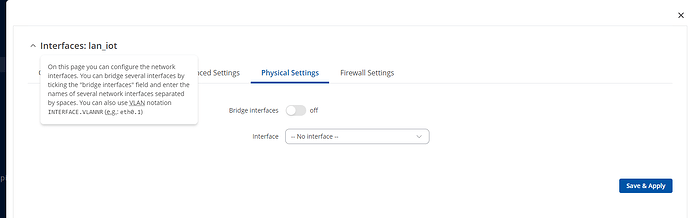
Issue is you chose interface br-lan, which is why it gets IPv4 from your main LAN. br-lan is made from wired LAN is eth0, 2.4 Ghz default AP is wlan0 and 5 Ghz default ap is wlan1.
What I am trying to say is that our network interface is wireless, so in this case we do not need to bridge anything, unless you would want that if any of the devices connect via LAN port, to be assigned to the same Guest network, but for that you would need VLAN configuration. For more information about VLAN you can read here: VLAN Set Up - Teltonika Networks Wiki
For our Guest Wi-Fi we need to keep the interface blank without any chosen interface.
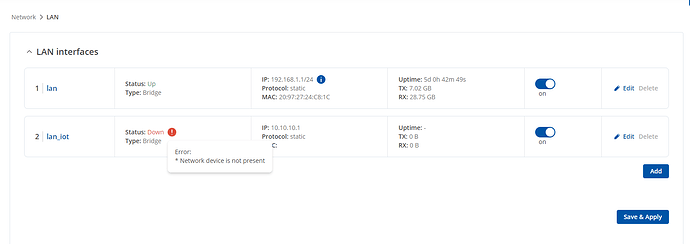
but I managed to only reach step New LAN interface. After I did the shown steps, I got the following error on the new LAN interface:
As for this issue, I tried replicating it from my side and the only time I got this error was when I had my Guest Wi-Fi disabled, once I enabled my Guest Wi-Fi, the Status went up, so try checking out if you have enabled your guest Wi-Fi.
As of the setup, I can provide you the steps for RUTX50:
-
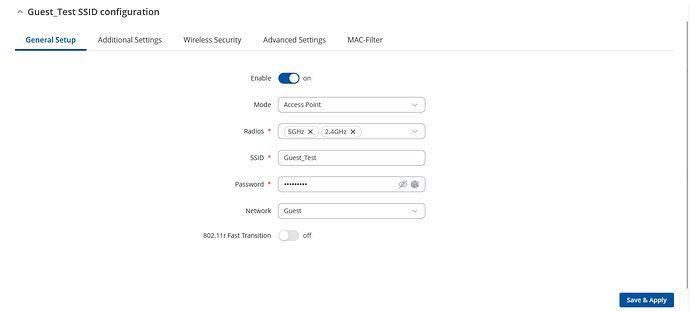
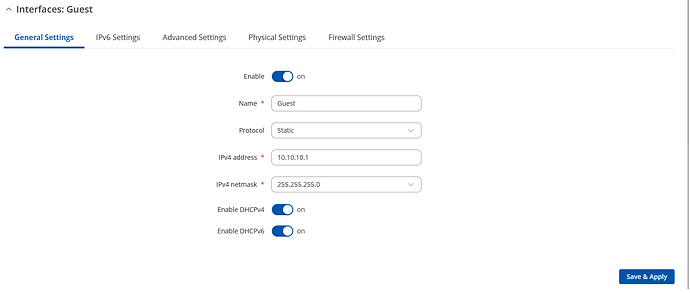
In your WebUI go to Network → Wireless → SSIDs → Add new SSID configuration with your chosen SSID/Password and other settings, Network choose Add a new and write the name for your new interface (“guest”), click “Save & Apply” and you will be prompted to your newly created interface.
-
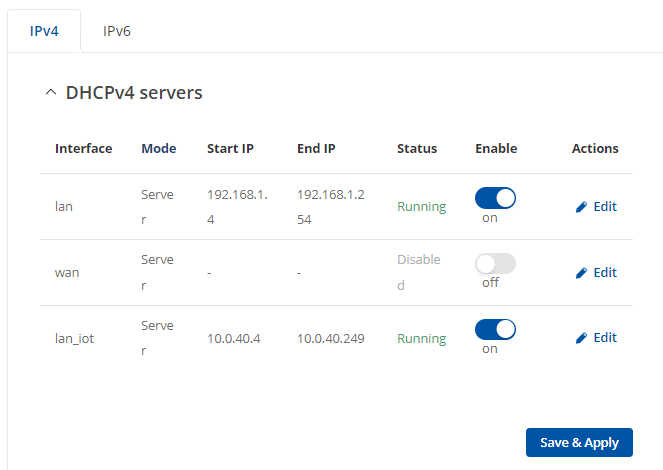
There for the IPv4 address write 10.10.10.1 (or whichever you are using) and click “Enable DHCPv4”, so we can assign it to our guest’s IPv4 address. After that “Save & Apply”.
-
Make sure that Router’s Wireless Access Point is running by checking it in Network → Wireless → SSIDs, once we made sure, move on to firewall settings.
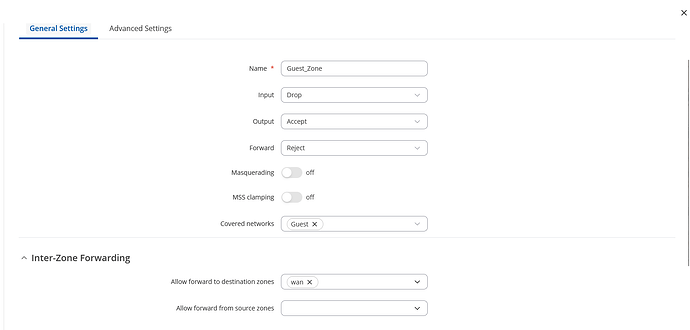
Go to Network → Firewall → General Settings → in Zones section add a new zone → name “Guest_Zone”:
Input: "Drop"
Output: "Accept"
Forward: "Reject"
Covered networks: The name of a newly created interface("Guest")
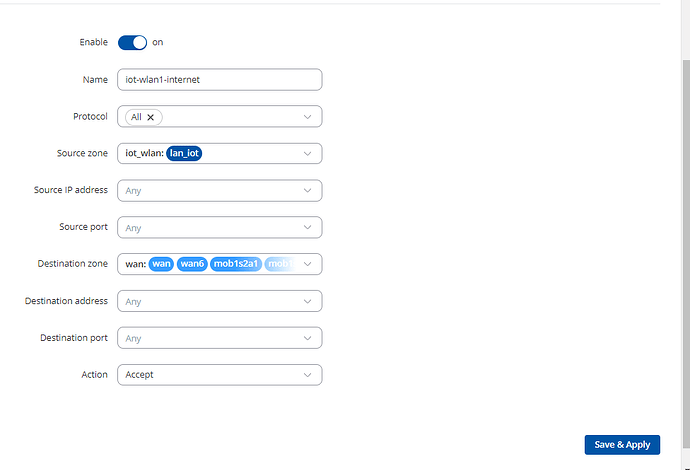
Allow forward to destination zones: wan
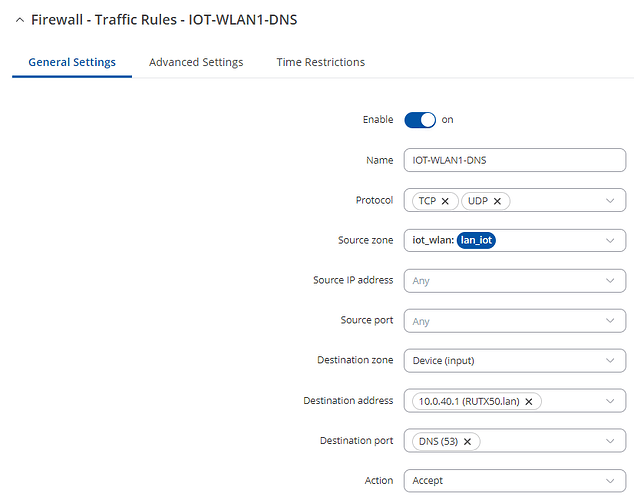
- Then move onto the “Traffic Rules” section, and create a new traffic rule for “Add new forward rule” from our newly created zone (“Guest_Zone”) to Destination zone “Device (input)”. Configure the settings accordingly:
Enable: On
Source zone: Guest_Zone
Protocol: TCP, UDP
Destination zone: Device (input)
Destination port: 53 (DNS)
Action: Accept
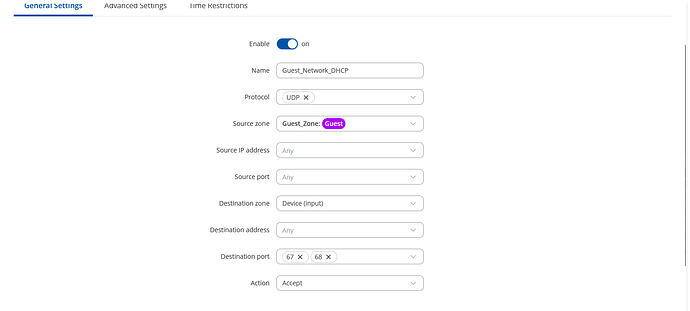
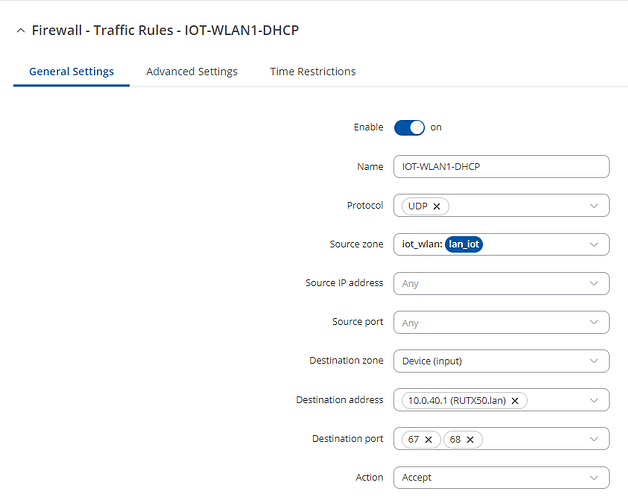
And another rule if we need DNS for IoT devices(if devices are connecting to server via domain name, not IP):
Enable: On
Source zone: Guest_Zone
Protocol: UDP
Destination zone: Device (input)
Destination port: 67, 68
Action: Accept
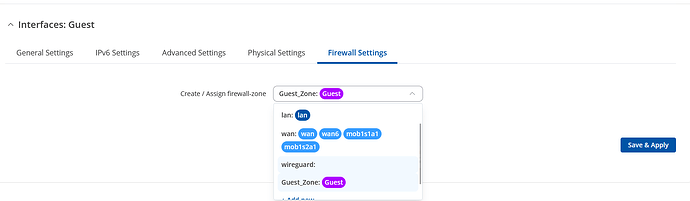
- If your guest interface is not assigned to Guest_Zone automatically, then you can move it manually. For that we need to assign our Firewall zone to Guest_Zone. Move onto Network → LAN → Guest interface edit → Firewall Settings section → Create / Assign firewall-zone.: Guest_Zone
After this configuration, you should not be able to reach your router’s local network, only assigned guest network.
Let me know if you have any further questions,
DziugasS