Hi, make sure to exclude your local LAN from local IPsec traffic selectors, otherwise IPsec service will “think” that the subnet you’re trying to reach is on the other (remote) side and you won’t be able to connect to the router via its LAN IP while IPsec tunnel is up.
This feature is called “passthrough” - you can specify passthrough per interface or subnet.
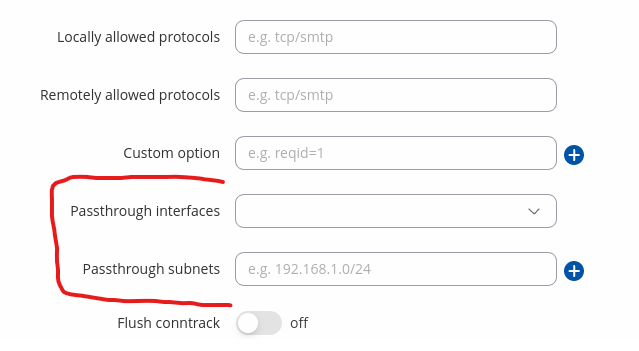
In simple terms, this feature tells the router to stop trying to reach your router LAN subnet via IPsec tunnel. Regarding why it works this way - this is the intended behavior. Routing rules and routing tables are two different entities in Linux-based OS. Routing rules will always be looked up first and only then a packet routing decision shall be made according to best match in the routing table.
StrongSwan is the daemon that makes IPsec work on RutOS routers and routing table 220 is a special table, dedicated specifically for IPsec traffic routing. More info about that here:
https://docs.strongswan.org/docs/5.9/howtos/introduction.html#_routing